Windows Active Guard
Posted: July 23, 2012
Threat Metric
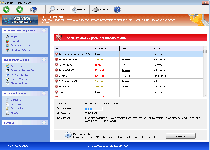
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 2/10 |
|---|---|
| Infected PCs: | 5 |
| First Seen: | July 23, 2012 |
|---|---|
| Last Seen: | April 23, 2023 |
| OS(es) Affected: | Windows |
 Windows Active Guard's features may look like anti-malware and online safety functions that could preserve your PC's wellbeing, but SpywareRemove.com malware experts better know Windows Active Guard as a rogue anti-malware program from FakeVimes. While Windows Active Guard does have an ample supply of security alerts and functions that look as though they can detect and thwart various types of PC threats, Windows Active Guard's security information is always fraudulent, and Windows Active Guard never makes a true effort to provide the features that Windows Active Guard prides itself on possessing. Because Windows Active Guard and other members of FakeVimes are also noted for anti-security characteristics (such as blocking unrelated applications arbitrarily), deleting Windows Active Guard as soon as you can make your way to a legitimate anti-malware brand of software is strongly advised.
Windows Active Guard's features may look like anti-malware and online safety functions that could preserve your PC's wellbeing, but SpywareRemove.com malware experts better know Windows Active Guard as a rogue anti-malware program from FakeVimes. While Windows Active Guard does have an ample supply of security alerts and functions that look as though they can detect and thwart various types of PC threats, Windows Active Guard's security information is always fraudulent, and Windows Active Guard never makes a true effort to provide the features that Windows Active Guard prides itself on possessing. Because Windows Active Guard and other members of FakeVimes are also noted for anti-security characteristics (such as blocking unrelated applications arbitrarily), deleting Windows Active Guard as soon as you can make your way to a legitimate anti-malware brand of software is strongly advised.
Windows Active Guard – a Toxic Defense from a Typical Piece of Scamware
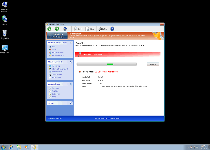
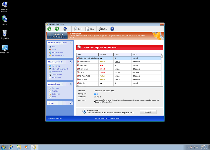
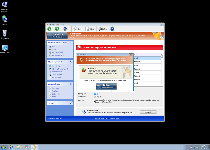
As a fake anti-malware scanner, Windows Active Guard may put up a strong showing of defending your computer from live attacks or ongoing infections, but SpywareRemove.com malware researchers have confirmed that Windows Active Guard can't find or remove any PC threat regardless of origin. Windows Active Guard infections are identifiable posthaste by the rapid-speed series of fake pop-up warnings that Windows Active Guard displays, supposedly on behalf of protecting your computer, although the alerts contained in these pop-ups always are fake. Some of these error messages may imitate normal Windows notifications, imply that OS components are damaged or claim (with inaccuracy) that specific types of high-level PC threats are on your hard drive. Alongside Windows Active Guard's pop-ups, you can also expect to be forced to endure equally fraudulent system scans that always show poor results.
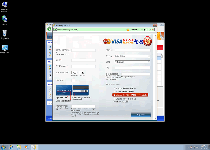
Windows Active Guard's intention with this fake security information is to encourage you to purchase a registry key that will empower Windows Active Guard to remove all of these PC threats... that Windows Active Guard, of course, made up in the first place. While using a freely-distributed code to register Windows Active Guard can help make removing Windows Active Guard less tedious than usual, SpywareRemove.com malware analysts strongly warn against spending actual money on Windows Active Guard or any other member of scamware from the FakeVimes family.
Even a passing familiarity with the FakeVimes category of rogue anti-malware programs should allow you to detect Windows Active Guard as soon as Windows Active Guard displays itself, since Windows Active Guard includes characteristic traits such as an 'Advanced Process Control,' 'All-in-one Suite' and overall features that are copied from outdated versions of Microsoft's Windows Security Center. Similar rogue anti-malware programs from Windows Active Guard's family include Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0.
The Importance of Having Your Own Guard Against Windows Active Guard
Even once you realize that Windows Active Guard's security alerts can be ignored in perfect safety, Windows Active Guard is still capable of being a danger to your PC. High-priority attacks by Windows Active Guard that cause SpywareRemove.com malware experts to recommend Windows Active Guard's immediate removal by real anti-malware software can include such functions as:
- Browser hijacks that alter your online searches or redirect you to unusual websites.
- Blocked security-related programs.
- Damaged and deleted Registry entries that can be used to prevent programs from launching or attack your computer's security features (such as the UAC or browser protection against malicious file downloads).
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\Protector-[RANDOM CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[RANDOM CHARACTERS].exe
File name: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [RANDOM CHARACTERS]
File name: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [RANDOM CHARACTERS]Group: Malware file
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4
File name: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4Group: Malware file
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0
File name: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]
File name: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exe
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXEFile type: Executable File
Mime Type: unknown/EXE
Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exe
File name: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Additional Information
| # | Message |
|---|---|
| 1 | Error Attempt to modify Registry key entries detected. Registry entry analysis recommended. Warning! Spambot detected! Attention! A spambot sending viruses from your e-mail has been detected on your PC. |
| 2 | Warning Firewall has blocked a program from accessing the Internet C:\program files\internet explorer\iexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
hi!,I could not boot my PC into any safe mode or delete any of the malware files. going go try an alternative. thanks.