Windows Custom Safety
Posted: June 8, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 19,228 |
|---|---|
| Threat Level: | 2/10 |
| Infected PCs: | 23,988 |
| First Seen: | June 8, 2012 |
|---|---|
| Last Seen: | February 12, 2025 |
| OS(es) Affected: | Windows |
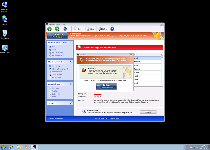
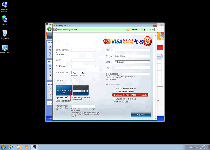
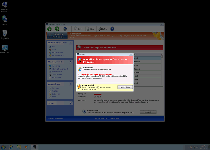
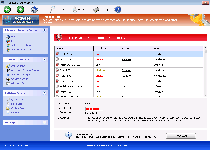 The FakeVimes scamware train has shown no signs of slowing down with its latest offering to the masses, Windows Custom Safety. This rogue anti-malware scanner may pretend to keep phishing attacks, rootkits, spyware and other threats away from your hard drive, but SpywareRemove.com malware researchers have verified Windows Custom Safety's inability to do any of the aforementioned defensive acts. Instead of giving your computer an increase in safety, Windows Custom Safety will institute a lock down against your PC's real security software, redirect your browser to hostile sites and display fake explanations for these attacks that include the names of practically every PC threat imaginable – except itself. Once it's identified, deleting Windows Custom Safety should occupy the top slot on your schedule, although you may also need to disable Windows Custom Safety with any of the methods below to access appropriate anti-malware programs.
The FakeVimes scamware train has shown no signs of slowing down with its latest offering to the masses, Windows Custom Safety. This rogue anti-malware scanner may pretend to keep phishing attacks, rootkits, spyware and other threats away from your hard drive, but SpywareRemove.com malware researchers have verified Windows Custom Safety's inability to do any of the aforementioned defensive acts. Instead of giving your computer an increase in safety, Windows Custom Safety will institute a lock down against your PC's real security software, redirect your browser to hostile sites and display fake explanations for these attacks that include the names of practically every PC threat imaginable – except itself. Once it's identified, deleting Windows Custom Safety should occupy the top slot on your schedule, although you may also need to disable Windows Custom Safety with any of the methods below to access appropriate anti-malware programs.
How Windows Custom Safety Customizes Your Safety in Perverse Ways
Windows Custom Safety is marketed in the form of a multi-featured security and anti-malware product, but its software actually is focused on the opposite aim: of making your computer unsafe, feeding you false security information and blocking anything that could thwart these attacks. These are traits that Windows Custom Safety shares with other variants of FakeVimes such as Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. While Windows Custom Safety launches with Windows and is easily identified, its attacks are not always as out-in-the-open, and SpywareRemove.com malware researchers have noted common Windows Custom Safety symptoms as shown below:
- Search engine redirects to malicious sites.
- Blocked PC security websites that are replaced by fraudulent error pages.
- Pop-up alerts that warn you about the presence of attacks or harmful programs that actually aren't present in the first place (such as identity theft or unrelated rootkits).
- Fake system scans that Windows Custom Safety uses to continue its illusion of your PC being attacked by unrealistically large amounts of varied PC threats.
- Anti-malware and security programs that Windows Custom Safety blocks with inaccurate warning messages – typically about supposed infections that have latched onto these programs. Blocked software can extend to basic Windows utilities like Task Manager.
Getting Windows Back to Normal without Windows Custom Safety's Shifty Assistance
Windows Custom Safety, like all modern members of the FakeVimes family of rogue anti-malware programs, has been confirmed to make modifications to Windows file during its infection process. These changes may allow your PC to be continued to be attacked by browser redirects and other issues even after Windows Custom Safety is deleted, if you fail to remove all of Windows Custom Safety's alterations. SpywareRemove.com malware researchers suggest using a reputable brand of anti-malware equipment to scan your complete PC for all traces of Windows Custom Safety and remove them in an automated fashion, since manual removal is hazardous for non-experts in PC security.
Since PC threats from Windows Custom Safety's family may also be installed by other forms of hostile software, such as Trojan droppers, SpywareRemove.com malware research team also recommends that you use thorough system scanning features that can detect related PC threats, in addition to Windows Custom Safety. Updating your anti-malware software prior to trying to delete Windows Custom Safety is also encouraged since Windows Custom Safety is a recent derivative of its family.

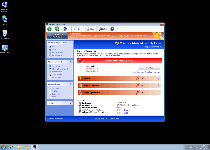
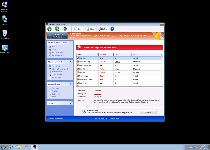
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector = %AppData%\Protector-[RANDOM CHARACTERS].exe
File name: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector = %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\About.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\a.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aAvgApi.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ackwin32.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ad-Aware.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentsvr.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\adaware.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\advxdwin.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV.exe\Debugger = svchost.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alogserv.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentw.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe\"Debugger" = "svchost.exe"HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector = %AppData%\Protector-[RANDOM CHARACTERS].exe
Additional Information
| # | Message |
|---|---|
| 1 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 2 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
| 3 | Warning Firewall has blocked a program from accessing the Internet. Windows Media Player Resources C:\Windows\system32\dllcache\wmploc.dll C:\Windows\system32\dllcache\wmploc.dll is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
I bought windows custom safety but did not get a product key
downloaded wjndows custom safety thought it was with windows now not sure what i did need to get rid of it
thought windows custom safety was with windows 7
0W000-000B0-00T00-E0020
with this code can you stop the fake alerts
🙂