Windows Maintenance Guard
Posted: June 18, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 2/10 |
|---|---|
| Infected PCs: | 50 |
| First Seen: | June 18, 2012 |
|---|---|
| OS(es) Affected: | Windows |
 Windows Maintenance Guard is one of the most recent variants of scamware from the FakeVimes family, a group of rogue anti-malware programs that use fake pop-up alerts and similar security 'features' to persuade victims to part with their money. Although Windows Maintenance Guard isn't able to identify or remove PC threats, Windows Maintenance Guard does possess substantial features with respect to causing online search redirects, blocking actual security programs or attacking your Windows security settings. Since Windows Maintenance Guard doesn't have any positive functions and endangers your computer with its mere presence, SpywareRemove.com malware experts recommend that you delete Windows Maintenance Guard by scanning your PC with a reputable equivalent of the anti-malware software that Windows Maintenance Guard pretends to be.
Windows Maintenance Guard is one of the most recent variants of scamware from the FakeVimes family, a group of rogue anti-malware programs that use fake pop-up alerts and similar security 'features' to persuade victims to part with their money. Although Windows Maintenance Guard isn't able to identify or remove PC threats, Windows Maintenance Guard does possess substantial features with respect to causing online search redirects, blocking actual security programs or attacking your Windows security settings. Since Windows Maintenance Guard doesn't have any positive functions and endangers your computer with its mere presence, SpywareRemove.com malware experts recommend that you delete Windows Maintenance Guard by scanning your PC with a reputable equivalent of the anti-malware software that Windows Maintenance Guard pretends to be.
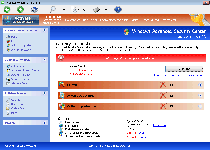
Windows Maintenance Guard's Failing Grade at PC Safety
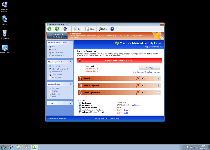
By borrowing the basic looks of Windows Security Center and appearing to include features like an anti-phishing barrier and an 'advanced process control' memory manager, Windows Maintenance Guard may seem to be able to solve all your computer security problems. However, as is typical for a security product that looks as though it can do more than all of the big-name brands put together, Windows Maintenance Guard actually is a fake anti-malware program without any working security functions to its name. SpywareRemove.com malware researchers especially note that Windows Maintenance Guard's scamware traits come into evidence after observation of its pop-up warnings and system scans, which always display negative results that aren't corroborated by reputable anti-malware scanners.
Windows Maintenance Guard's fake security data can include both warnings about live attacks and infection alerts, including identifying real (but not present on your hard drive) viruses, Trojans and similar types of high-level PC threats. Since Windows Maintenance Guard will also display these pop-ups in conjunction with blocking unrelated programs, you may be unable to access security software to expedite Windows Maintenance Guard's removal until you disable Windows Maintenance Guard itself. SpywareRemove.com malware researchers recommend Safe Mode or a system boot from a removable media device (IE, a USB drive, etc) to stop Windows Maintenance Guard from launching without consent.
The Danger of Trusting Windows Maintenance Guard for Your Computer
While ignoring Windows Maintenance Guard's fake security information is a good start to dealing with Windows Maintenance Guard, SpywareRemove.com malware experts advise against allowing Windows Maintenance Guard to remain on your computer once Windows Maintenance Guard is identified. As a member of the FakeVimes family Windows Maintenance Guard may also use security-damaging attacks against your PC. Some of Windows Maintenance Guard clones are Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. The most prominent attacks that Windows Maintenance Guard and its relatives are capable of utilizing are noted below:
- Windows Maintenance Guard may expose you to malicious sites by redirecting your web browser-based searches.
- Likewise, your browser's ability to protect your PC against improperly-identified (via signatures) files may also be attacked by Windows Maintenance Guard's system Registry changes.
- Legitimate security programs, including anti-malware scanners and firewall utilities, may also be blocked by Windows Maintenance Guard, either at the Registry level or the system memory level. In cases of the former, restoring the Registry or reinstalling affected applications may be required, although, for the latter, Maintenance Guard malware researchers have found that merely disabling Windows Maintenance Guard will prove effective.
As a closing point, it should be stressed that Windows Maintenance Guard should never be treated as a legitimate software product or be purchased, since this can allow criminals to gain access to confidential fiscal information.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%AppData%\1st$0l3th1s.cnf
File name: %AppData%\1st$0l3th1s.cnfMime Type: unknown/cnf
Group: Malware file
Protector-[RANDOM 3 CHARACTERS].exe
File name: Protector-[RANDOM 3 CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Protector-[RANDOM 4 CHARACTERS].exe
File name: Protector-[RANDOM 4 CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-6-18_7"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "idhsudrgrf"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\ASProtectHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\escanv95.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avnt.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mbamservice.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spoolcv.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vsmain.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\procexplorerv1.0.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\npf40_tw_98_nt_me_2k.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Anti-Virus Professional.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\..{RunKeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
Additional Information
| # | Message |
|---|---|
| 1 | Error
Attempt to modify registry key entries detected. Registry entry analysis is recommended. |
| 2 | Error
Attempt to run a potentially dangerous script detected. Full system scan is highly recommended. |
I can't find any files on my computer