Windows Malware Sleuth
Posted: March 4, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 2/10 |
|---|---|
| Infected PCs: | 15 |
| First Seen: | March 4, 2012 |
|---|---|
| OS(es) Affected: | Windows |
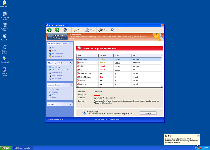
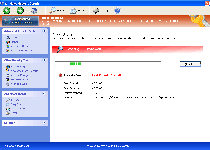 Windows Malware Sleuth is a fresh addition to a family of fake anti-virus scanners that are known for showing inaccurate threat alerts, blocking critical Windows applications and attacking your web browser. Like its brethren, Windows Malware Sleuth has no ability to follow through on its claims to protect your computer from viruses, phishing attacks and other PC threats, and SpywareRemove.com malware researchers recommended that you remove Windows Malware Sleuth as soon as it's possible to alleviate the symptoms noted above. In its attempt to come across as a real anti-malware product, Windows Malware Sleuth may provide its own removal utility, but Windows Malware Sleuth should always be deleted by appropriate anti-malware software that can insure that all of its components and related threats (such as Trojan droppers) are also removed.
Windows Malware Sleuth is a fresh addition to a family of fake anti-virus scanners that are known for showing inaccurate threat alerts, blocking critical Windows applications and attacking your web browser. Like its brethren, Windows Malware Sleuth has no ability to follow through on its claims to protect your computer from viruses, phishing attacks and other PC threats, and SpywareRemove.com malware researchers recommended that you remove Windows Malware Sleuth as soon as it's possible to alleviate the symptoms noted above. In its attempt to come across as a real anti-malware product, Windows Malware Sleuth may provide its own removal utility, but Windows Malware Sleuth should always be deleted by appropriate anti-malware software that can insure that all of its components and related threats (such as Trojan droppers) are also removed.
Sorting Through the Evidence of Windows Malware Sleuth's Numerous Crimes
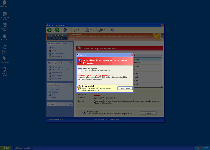
Windows Malware Sleuth's aesthetics are built off of a Windows Security Center-based template that's rotated throughout the FakeVimes family of scamware, each member of which bears a different name but the same goal in mind – to annoy and frighten you until you buy a full version of the software in question. While Windows Malware Sleuth and other fake anti-virus scanners from the Rogue.FakeVimes group are able to create very convincing warning messages and alerts that can be displayed in various ways (such as within your web browser or as a taskbar notification), SpywareRemove.com malware researchers emphasize that Windows Malware Sleuth isn't able to provide any system information that isn't fraudulent.
As is typical for fake anti-virus scanners of its ilk, Windows Malware Sleuth also subscribes to a philosophy of refusing to be uninstalled or even disabled. On Windows-based computers, Windows Malware Sleuth will launch itself automatically and conduct its fake alerts, system scans and other attacks without your consent. SpywareRemove.com malware analysts note that Safe Mode, also commonly available on most Windows PCs, is one of the easiest ways to disable Windows Malware Sleuth so that you can scan your PC and remove Windows Malware Sleuth without further problems. Similar tactics are also effective against clones of Windows Malware Sleuth, such as Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0.
The Final Windows Malware Sleuth Attacks That Seal the Deal
While poor threat detection is worth labeling Windows Malware Sleuth a nuisance, SpywareRemove.com malware research team recommends that you treat Windows Malware Sleuth as an actively malicious threat to your PC, since Windows Malware Sleuth and similar Rogue.FakeVimes-based PC threats are known for additional hostilities. Common issues that can persist until Windows Malware Sleuth is deleted by appropriate anti-malware products include such problems as:
- Browser-based redirect attacks. Redirects may be used to display fake warning messages, control your search results, take you to Windows Malware Sleuth's website or block PC security sites.
- Blocked applications. In most cases, Windows Malware Sleuth will block programs by displaying an inaccurate warning message, but with regards to the Task Manager and Registry Editor, Windows Malware Sleuth actually will replace them with its own Advanced Process Control window.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%AppData%\Protector-[RANDOM 3 CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM 3 CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%CommonStartMenu%\Programs\Windows Malware Sleuth.lnk
File name: %CommonStartMenu%\Programs\Windows Malware Sleuth.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%Desktop%\Windows Malware Sleuth.lnk
File name: %Desktop%\Windows Malware Sleuth.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = 2012-3-4_1HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "wbukxhryfk"HKEY..\..\..\..{Subkeys}HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\autoupdate.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avpdos32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\antivirus.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hbinst.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\jdbgmrg.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\brasil.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\csc.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\qh.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svchostc.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vbust.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\win32us.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\exe.avxw.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nav.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nupgrade.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mcvsrte.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pctsTray.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SecurityFighter.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\..{RunKeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
Additional Information
| # | Message |
|---|---|
| 1 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 2 | Warning! Virus Detected Threat detected: FTP Server Infected file: C:\Windows\System32\dllcache\wmpshell.dll |
| 3 | Warning Firewall has blocked a program from accessing the Internet C:\program files\internet explorer\iexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |




This is not my computer I am useing to cantact you. My computer will not stay online long enough to down load your anti spy ware program. Windows sleuth is killing me, I have to do all my stuff at work. Not good if I am cought by my boss. Can you help me.
I can not get online because of windows sleuth ink. What can I do I can not keep useing the work computer.