Windows Privacy Extension
Posted: June 28, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 9 |
| First Seen: | June 28, 2012 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
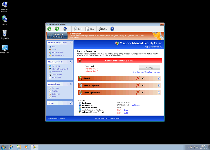
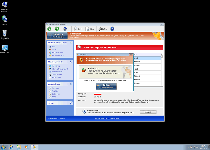
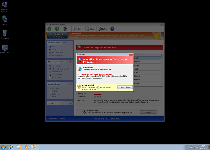
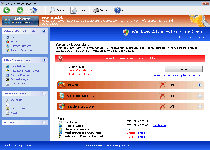 The suitably-titled Windows Privacy Extension, instead of being an independent program unto itself, can be considered a clone of other FakeVimes-based rogue anti-malware programs. As a faux security product, Windows Privacy Extension can display fake alerts and system scans, but Windows Privacy Extension's real abilities at malware detection and removal are completely lacking. SpywareRemove.com malware researchers also note that the probability of other attacks in any Windows Privacy Extension infection is also high and that these malfunctions can include browser redirects or even attacks against real security-related applications. Therefore, it should be conspicuously evident that Windows Privacy Extension must be deleted ASAP to ensure your PC's continued well-being, although it's recommended for you to use anti-malware software to delete Windows Privacy Extension and its system modifications.
The suitably-titled Windows Privacy Extension, instead of being an independent program unto itself, can be considered a clone of other FakeVimes-based rogue anti-malware programs. As a faux security product, Windows Privacy Extension can display fake alerts and system scans, but Windows Privacy Extension's real abilities at malware detection and removal are completely lacking. SpywareRemove.com malware researchers also note that the probability of other attacks in any Windows Privacy Extension infection is also high and that these malfunctions can include browser redirects or even attacks against real security-related applications. Therefore, it should be conspicuously evident that Windows Privacy Extension must be deleted ASAP to ensure your PC's continued well-being, although it's recommended for you to use anti-malware software to delete Windows Privacy Extension and its system modifications.
Windows Privacy Extension: More of a Peril to Your Privacy Than Anything Else
Windows Privacy Extension, like all members of FakeVimes, pretends to be a general-purpose security and anti-malware product, even though all of its security-related features are hoaxes. System scans by Windows Privacy Extension always display Trojans and other PC threats without any attempt to corroborate with reality, and warning messages by Windows Privacy Extension will use various means to trick you into believing that your PC is under attack. Of course, the irony that your PC is under attack – by Windows Privacy Extension, which will not stop until you give in to its purchase requests or banish Windows Privacy Extension from your hard drive. SpywareRemove.com malware researchers recommend the latter, since criminals connected with scamware like Windows Privacy Extension are known for exploiting financial information (such as credit card numbers) in illegal and highly-damaging ways.
The fake security 'features' of Windows Privacy Extension, as noted above, can be considered its most obvious symptoms, but other symptoms that SpywareRemove.com malware analysts consider highly probable in any Windows Privacy Extension infection are also noted below:
- Search engine hijacks that redirect you to untrustworthy, malicious or advertisement-based search engines (regardless of what brand of browser you may be using at the time).
- Unrelated programs being blocked, such as Task Manager, the Registry Editor, the UAC or popular brands of anti-malware scanners. Windows Privacy Extension may also display pop-ups to convince you that the aforementioned applications have been compromised or damaged.
- Registry-based system settings being changed in ways that make your PC vulnerable to attacks by other PC threats, particularly regarding file-downloading settings.
Wrenching Your Real Privacy Back from Windows Privacy Extension's Grasp
As long as you avoid spending money on Windows Privacy Extension and remove Windows Privacy Extension as soon as possible, your PC shouldn't suffer long-lasting harm from its attacks. SpywareRemove.com malware researchers recommend similar actions for all other PC threats from Windows Privacy Extension's family, including Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. While purchasing Windows Privacy Extension's registration is discouraged, using a free code for this process, such as '0W000-000B0-00T00-E0020,' is safe, and may even alleviate issues with removing Windows Privacy Extension.
As a routine part of its behavior, Windows Privacy Extension changes some Windows components, including the Registry. Since these changes can damage your OS if removed improperly, SpywareRemove.com malware research team encourages using anti-malware software for this purpose whenever it's available.

Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-yagp.exe
File name: Protector-yagp.exeSize: 2.23 MB (2233856 bytes)
MD5: 6c3b6c1bd9b6472f162fd567e9942af2
Detection count: 95
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
npswf32.dll
File name: npswf32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
Protector-[rnd].exe
File name: Protector-[rnd].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Protector-[rnd].exe
File name: %AppData%\Protector-[rnd].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "ID" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-2-17_2"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "rudbxijemb"HKEY..\..\..\..{Subkeys}HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avp32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avpcc.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashDisp.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\divx.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mostat.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\platin.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zapsetup3001.exe
Additional Information
| # | Message |
|---|---|
| 1 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
| 2 | Error There’s a suspicious software running on your PC. For more details, run a system file check. |
| 3 | Warning! Identity Theft attempt detected! Hidden connection IP: 210.1.58.100 Target: Microsoft corporation keys Your IP: 127.0.0.1 |
I have the "Windows Privacy Extension" since yesterday