Windows Pro Defence
Posted: June 24, 2012
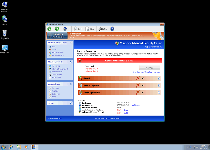
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
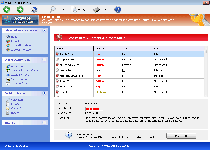
| Threat Level: | 2/10 |
|---|---|
| Infected PCs: | 82 |
| First Seen: | June 24, 2012 |
|---|---|
| OS(es) Affected: | Windows |
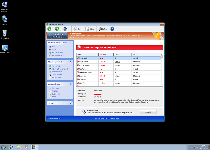
 One of the latest variants from a well-known group of rogue anti-malware products, Windows Pro Defence uses system scans, pop-up alerts and other forms of fake security information to wheedle a purchase out of its victims. While Windows Pro Defence may seem as though Windows Pro Defence is detecting malicious software and direct attacks left and right, SpywareRemove.com malware researchers haven't seen any indications that Windows Pro Defence is any more capable of performing security functions than other scamware from FakeVimes. Even if you can identify Windows Pro Defence as the fraudster Windows Pro Defence is, Windows Pro Defence's simple presence on your PC can result in security risks due to altered Windows settings and inaccessible software, and Windows Pro Defence's speedy deletion via a real anti-malware scanner is heavily advised.
One of the latest variants from a well-known group of rogue anti-malware products, Windows Pro Defence uses system scans, pop-up alerts and other forms of fake security information to wheedle a purchase out of its victims. While Windows Pro Defence may seem as though Windows Pro Defence is detecting malicious software and direct attacks left and right, SpywareRemove.com malware researchers haven't seen any indications that Windows Pro Defence is any more capable of performing security functions than other scamware from FakeVimes. Even if you can identify Windows Pro Defence as the fraudster Windows Pro Defence is, Windows Pro Defence's simple presence on your PC can result in security risks due to altered Windows settings and inaccessible software, and Windows Pro Defence's speedy deletion via a real anti-malware scanner is heavily advised.
Why Putting Your Dukes Up Against Windows Pro Defence Might Be Wise
Windows Pro Defence looks and is promoted by other PC threats as a form of anti-malware and PC security software, but Windows Pro Defence's seemingly multitudinous security functions are inaccurate, and, at best, can only dish out fake information about Trojan infections, identity theft attacks, Windows Registry attacks and the like. While Windows Pro Defence's error messages and scans will try to make it appear like many types of PC threats are endangering your computer, Windows Pro Defence doesn't have any ability to find or remove harmful software. Naturally, SpywareRemove.com malware experts discourage spending money on Windows Pro Defence's poor services, although faking the registration process with the code '0W000-000B0-00T00-E0020' can be useful for both Windows Pro Defence and other FakeVimes-based scamware.
Likely infection vectors for Windows Pro Defence and related PC threats include fake media downloads (such as updates for codecs or movie players) and online simulations of system scanners that recommend the installation of unspecific security software. Avoiding disreputable or vague software downloads is one of several methods that can be used to protect your computer from likely FakeVimes-based scamware attacks – a group that includes both Windows Pro Defence and similar PC threats like Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0.
Windows Pro Defence: Starting at Fake Threat Detector and Workings It Way to Real Threat Provider
Windows Pro Defence may not be able to fill any niches that you'd want from real anti-malware programs, but, lamentably, Windows Pro Defence does include real features that can be significantly detrimental to your computer's safety. SpywareRemove.com malware experts have outlined the worst of these as follows, and also note that they may occur without visible symptoms:
- Redirects to malicious, fraudulent or spam-oriented websites (typically by redirecting your browser's search results).
- An inability to use other applications, including tools like the Task Manager that could be used to help remove Windows Pro Defence. You may also receive fake pop-ups that announce that these blocked programs are infected.
- Lowered security settings for your web browser; this places your PC at a greater risk than normal of being attacked by malicious websites, drive-by-downloads and fraudulent files.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%AppData%\1st$0l3th1s.cnf
File name: %AppData%\1st$0l3th1s.cnfMime Type: unknown/cnf
Group: Malware file
Protector-[RANDOM 3 CHARACTERS].exe
File name: Protector-[RANDOM 3 CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Protector-[RANDOM 4 CHARACTERS].exe
File name: Protector-[RANDOM 4 CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-6-24_4"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "wmlkovyjad"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\ASProtectHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srng.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msdm.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\protector.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bipcpevalsetup.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\W3asbas.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\gbmenu.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\..{RunKeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
Additional Information
| # | Message |
|---|---|
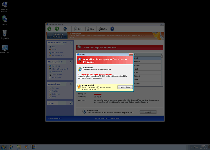
| 1 | Error
Attempt to modify registry key entries detected. Registry entry analysis is recommended. |
| 2 | Error
Attempt to run a potentially dangerous script detected. Full system scan is highly recommended. |
| 3 | Error
Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 4 | Error Attempt to modify registry key entries detected. Registry entry analysis is recommended. |
| 5 | Error Attempt to run a potentially dangerous script detected. Full system scan is highly recommended. |
| 6 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
How serious a threat is Windows Pro Defense and are there any subscribers that have related their problems with it?