Windows Safety Maintenance
Posted: May 24, 2012
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 26 |
| First Seen: | May 24, 2012 |
|---|---|
| OS(es) Affected: | Windows |
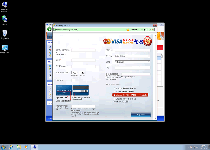
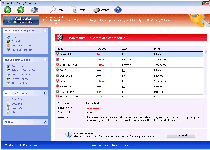 With the scamware factory of Win32/FakeVimes showing no signs of stopping, Windows Safety Maintenance is just the next model on its production line and shares all the common (and fraudulent) traits of its family. Like many other types of FakeVimes-derived PC threats, Windows Safety Maintenance pretends to be an anti-malware product, but Windows Safety Maintenance's warning messages sound alarms about fake threats and its scans will always show negative results that don't sync with reality. Even if you know well enough to avoid spending money on Windows Safety Maintenance's valueless registration key, SpywareRemove.com malware researchers still recommend that you delete Windows Safety Maintenance as soon as you can launch suitable security software. Until Windows Safety Maintenance is removed, your PC will also be compromised by a variety of security attacks as well as suffering through potential browser redirects to harmful sites.
With the scamware factory of Win32/FakeVimes showing no signs of stopping, Windows Safety Maintenance is just the next model on its production line and shares all the common (and fraudulent) traits of its family. Like many other types of FakeVimes-derived PC threats, Windows Safety Maintenance pretends to be an anti-malware product, but Windows Safety Maintenance's warning messages sound alarms about fake threats and its scans will always show negative results that don't sync with reality. Even if you know well enough to avoid spending money on Windows Safety Maintenance's valueless registration key, SpywareRemove.com malware researchers still recommend that you delete Windows Safety Maintenance as soon as you can launch suitable security software. Until Windows Safety Maintenance is removed, your PC will also be compromised by a variety of security attacks as well as suffering through potential browser redirects to harmful sites.
Why Maintaining Your Distance from Windows Safety Maintenance is a Terrific Idea
Windows Safety Maintenance, rather than being the original anti-malware program that Windows Safety Maintenance wants you to believe Windows Safety Maintenance is, is a clone built off of the same template that other recent variants of Win32/FakeVimes have used. Closely-related names in rogue anti-malware software include (among other possible examples) Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security. These PC threats, including Windows Safety Maintenance, aren't capable of providing actual protection for your PC but cover for their shortcomings by displaying fraudulent security information.
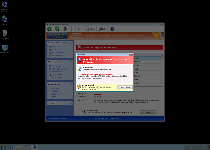
Windows Safety Maintenance's fake security displays can include various pop-ups, including fake toolbar notifications that cloak themselves in the guise of Windows alerts, as well as system scans that always return results that are full of nonexistent infections (including technically-identified Trojans, spyware, and other types of high-level PC threats). Since all of this information is fraudulent, SpywareRemove.com malware research team encourages you to turn a stiff upper lip to Windows Safety Maintenance's fake warnings and avoid spending any money on the software registration process that Windows Safety Maintenance attempts to foist upon you.
The Danger of Scamware That Pretends to Be a Safety-Enhancer
In-between its attempts to snatch your money in return for the equally-unpleasant 'paid' version of its software, Windows Safety Maintenance may also make attacks against your web browser and overall Windows security. SpywareRemove.com malware experts have found the following Windows Safety Maintenance-related symptoms to be especially worth mentioning, since they can cause your PC to be vulnerable to future attacks:
- Windows Safety Maintenance may alter your Windows Hosts file to cause browser redirects to malicious sites. SpywareRemove.com malware researchers have noted that popular search engines like Google are especially likely to be used as triggers for these redirect attacks.
- Windows security features may be disabled; this includes the User Account Control and default protection against files with improper ID signatures.
- You may also find that your security programs, such as anti-virus scanners and Windows tools like Task Manager are blocked by Windows Safety Maintenance. Either registering Windows Safety Maintenance with the code '0W000-000B0-00T00-E0020' or disabling Windows Safety Maintenance via Safe Mode can help to avoid these attacks and remove Windows Safety Maintenance with your choice of anti-malware product.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:file.exe
File name: file.exeSize: 621.63 KB (621632 bytes)
MD5: 868c130259a35bf95f80c642de40cc45
Detection count: 86
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: April 8, 2014
%APPDATA%\Protector-ttqo.exe
File name: Protector-ttqo.exeSize: 1.81 MB (1816576 bytes)
MD5: 796aa00839dbaf2184accbc24aefbba2
Detection count: 42
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: May 24, 2012
%APPDATA%\Protector-trei.exe
File name: Protector-trei.exeSize: 2.04 MB (2045440 bytes)
MD5: 0c23465333b236c6bba316fac9513290
Detection count: 21
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: May 24, 2012
%APPDATA%\Protector-ysgk.exe
File name: Protector-ysgk.exeSize: 1.95 MB (1955840 bytes)
MD5: cb2a1efb9a03dd129169e6ecef5b8e7d
Detection count: 8
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: May 24, 2012
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\Protector-{RANDOM 3 CHARACTERS}.exe
File name: %AppData%\Protector-{RANDOM 3 CHARACTERS}.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Protector-{RANDOM 4 CHARACTERS}.exe
File name: %AppData%\Protector-{RANDOM 4 CHARACTERS}.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%StartMenu%\Windows Safety Maintenance.lnk
File name: %StartMenu%\Windows Safety Maintenance.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%AppData%\Microsoft\Internet Explorer\Quick Launch\Windows Safety Maintenance.lnk
File name: %AppData%\Microsoft\Internet Explorer\Quick Launch\Windows Safety Maintenance.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%AppData%\Windows Safety Maintenance\Instructions.ini
File name: %AppData%\Windows Safety Maintenance\Instructions.iniMime Type: unknown/ini
Group: Malware file
%AppData%\Windows Safety Maintenance\ScanDisk_.exe
File name: %AppData%\Windows Safety Maintenance\ScanDisk_.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%CommonAppData%\58ef5\SPT.ico
File name: %CommonAppData%\58ef5\SPT.icoMime Type: unknown/ico
Group: Malware file
%CommonAppData%\58ef5\SP98c.exe
File name: %CommonAppData%\58ef5\SP98c.exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%CommonAppData%\SPUPCZPDET\SPABOIJT.cfg
File name: %CommonAppData%\SPUPCZPDET\SPABOIJT.cfgMime Type: unknown/cfg
Group: Malware file
%Desktop%\Windows Safety Maintenance.lnk
File name: %Desktop%\Windows Safety Maintenance.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%Programs%\Windows Safety Maintenance.lnk
File name: %Programs%\Windows Safety Maintenance.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [RANDOM CHARACTERS]HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[rnd].exeHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXEHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe
Additional Information
| # | Message |
|---|---|
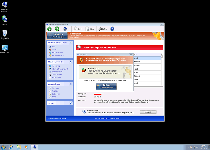
| 1 | System alert Suspicious software which may be dangerous has been detected on your PC. Click here to remove this threat immediately using System Protection Tools. |
| 2 | System alert System Protection Tools has detected potentially harmful software in your system. It is strongly recommended that you register System Protection Tools to remove all found threats immediately. |
| 3 | System warning No real-time malware, spyware and virus protection was found. Click here to activate. |
| 4 | Warning Warning! Virus detected |
| 5 | Warning! Identity theft attempt detected Hidden connection IP: 128.154.26.11 Target: Microsoft Corporation keys |

OMG! This saved my son's computer. Thank you so much!!!