Windows Secure Web Patch
Posted: June 15, 2012
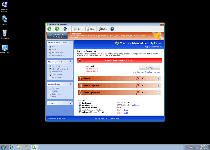
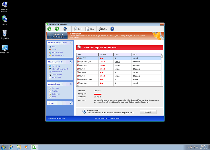
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 35 |
| First Seen: | June 15, 2012 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
 Even though Windows Secure Web Patch has cribbed most of its looks from old versions of Windows Security Center, Windows Secure Web Patch is neither a security tool nor a Microsoft-endorsed product. As rogue anti-malware software, Windows Secure Web Patch has only one intention in mind: to mislead you with bad security information until you spend money on its 'full' software. Since Windows Secure Web Patch belongs to a family that's also known for its browser redirects, attacks against browser security and attempts to prevent victims from using actual security-oriented software, SpywareRemove.com malware researchers always urge you to remove Windows Secure Web Patch quickly and with an appropriate anti-malware application.
Even though Windows Secure Web Patch has cribbed most of its looks from old versions of Windows Security Center, Windows Secure Web Patch is neither a security tool nor a Microsoft-endorsed product. As rogue anti-malware software, Windows Secure Web Patch has only one intention in mind: to mislead you with bad security information until you spend money on its 'full' software. Since Windows Secure Web Patch belongs to a family that's also known for its browser redirects, attacks against browser security and attempts to prevent victims from using actual security-oriented software, SpywareRemove.com malware researchers always urge you to remove Windows Secure Web Patch quickly and with an appropriate anti-malware application.
Windows Secure Web Patch: the Patch That Downgrades Your PC's Safety
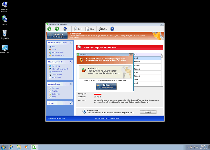
At first glance, Windows Secure Web Patch might look like an anti-malware scanner with a surprising breadth of safety features, but SpywareRemove.com malware research team has confirmed that Windows Secure Web Patch is nothing more than another assembly-line clone from FakeVimes. As scamware all of Windows Secure Web Patch's security scans and pop-ups should be ignored as fraudulent, as well as the ones issued by its clones like Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. As long as it's open, Windows Secure Web Patch will always display warning messages about nonexistent infections and attacks as part of its scam.
Windows Secure Web Patch may also have hidden but more significant effects on your PC than a few simple pop-ups. Some of the worst of Windows Secure Web Patch's capabilities that SpywareRemove.com malware experts have divined include:
- Browser redirects that alter your online searches or expose you to harmful sites.
- Windows security settings that are changed without your consent, especially in the case of browser settings that protect you against suspicious downloads.
- Monitored memory processes and altered Registry settings, both of which work hand-in-hand to block unrelated and legitimate security programs.
The latter attack especially causes SpywareRemove.com malware researchers to suggest disabling Windows Secure Web Patch's startup method before you attempt to scan your PC for Windows Secure Web Patch's removal. Fortunately, standard techniques like booting from removable media will work well for preventing Windows Secure Web Patch from starting itself.
Keeping Windows Secure Web Patch Out of Your Hard Drive in the First Place
Windows Secure Web Patch, like its kin, is promoted through fake online scanners and Trojans that are labeled via misleading links (such as fake media codecs and movie player updates). Keeping your downloads limited to reputable sources, avoiding updates from unusual third-parties and being careful around suspicious security programs will all help to keep Windows Secure Web Patch from getting anywhere near your PC. SpywareRemove.com malware researchers additionally recommend that you keep scripts disabled for untrustworthy sites, especially those that are promoted in Windows Secure Web Patch's browser-redirecting attacks, as a means of blocking drive-by-downloads.
Windows Secure Web Patch should never be removed by normal software-deletion methods or treated as an actual security program, since Windows Secure Web Patch is criminal software that lacks any real features for your PC's benefit. Although Windows Secure Web Patch's presentation is that of security software, it should be stressed that Windows Secure Web Patch is no better or worse than any Trojan, virus or rootkit.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-tkbu.exe
File name: Protector-tkbu.exeSize: 2.41 MB (2416128 bytes)
MD5: 9be34127493f172fe42959ee6520ad6d
Detection count: 45
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: January 8, 2020
%AppData%\Protector-[RANDOM CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "rudbxijemb"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "ID" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-2-17_2"HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ashDisp.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\divx.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avp32.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\_avpcc.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\tapinstall.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zapsetup3001.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mostat.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\platin.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ERROR_PAGE_BYPASS_ZONE_CHECK_FOR_HTTPS_KB954312
Additional Information
| # | Message |
|---|---|
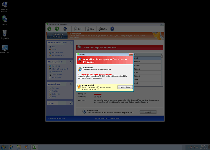
| 1 | Error Keylogger activity detected. System information security is at risk. It is recommended to activate protection and run a full system scan. |
| 2 | Error Serious slowdown in system performance. To eliminate the causes, full check is recommended. |
| 3 | Error Software without a digital signature detected. Your system files are at risk. We strongly advise you to activate your protection. |
I bought the program recently and every time I try to open it, it says "the 'Protector-kkgh.exe' that this shorcut refers to has been changed or moved, so this shorcut will no longer work properly." I've also tried to open the program on the start bar and "all programs" option. Please help and thanks.