Windows Threats Destroyer
Posted: March 1, 2012
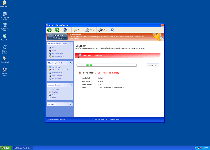
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
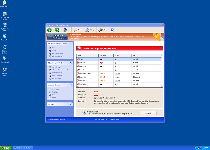
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 93 |
| First Seen: | March 1, 2012 |
|---|---|
| OS(es) Affected: | Windows |
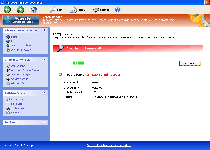 Windows Threats Destroyer claims to be able to detect and take care of an entire spectrum of PC threats that encompass everything from phishing attacks to viruses, but a close look at Windows Threats Destroyer's features will show that Windows Threats Destroyer is just another fake anti-virus product that's been cloned from previous examples of the same. As a FakeVimes-derived rogue anti-virus program Windows Attacks Preventor is identical to such PC threats as Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. Windows Threats Destroyer should be removed from your PC whenever you have access to anti-malware software of good repute. Until you do so, fraudulent warning messages, browser redirect attacks and blockades against your real security software are likely to haunt your PC while Windows Threats Destroyer is active.
Windows Threats Destroyer claims to be able to detect and take care of an entire spectrum of PC threats that encompass everything from phishing attacks to viruses, but a close look at Windows Threats Destroyer's features will show that Windows Threats Destroyer is just another fake anti-virus product that's been cloned from previous examples of the same. As a FakeVimes-derived rogue anti-virus program Windows Attacks Preventor is identical to such PC threats as Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. Windows Threats Destroyer should be removed from your PC whenever you have access to anti-malware software of good repute. Until you do so, fraudulent warning messages, browser redirect attacks and blockades against your real security software are likely to haunt your PC while Windows Threats Destroyer is active.
Windows Threats Destroyer – a True Destroyer of Threats... to Itself
Windows Threats Destroyer's rather ominous name may be memorable, but all of Windows Threats Destroyer's features and even its appearance are all cheap copies of preexisting aspects of other brands of Rogue.VirusDoctor scamware. While Windows Threats Destroyer will make every attempt to fool you into believing that there's a teeming swarm of PC threats assaulting your computer, Windows Threats Destroyer doesn't have any real anti-virus or threat removal capabilities, and as such, should be ignored whenever its many fake alerts appear.
SpywareRemove.com malware researchers have also concluded that likely attacks from Windows Threats Destroyer aren't limited to these fake security pop-ups, or even inaccurate simulations of system scans. Windows Threats Destroyer may also:
- Launch itself without your permission when Windows starts (by inserting startup entries into the Windows Registry).
- Remain open in the background as a memory process even if you attempt to close its visible window.
- Attack your web browser to constrict your ability to load PC security sites or to force you to visit Windows Threats Destroyer's homepage.
- Block certain system tools, such as Task Manager, which Windows Threats Destroyer may replace with its own fake security functions.
- Prevent you from running anti-malware scanners or other security applications that could remove Windows Threats Destroyer without trouble.
Taking Windows Threats Destroyer Out to the Trash
Due to Windows Threats Destroyer's proclivity for launching itself right along with Windows, it's recommended that you launch your OS in a way that prevents Windows Threats Destroyer from loading before you try to delete Windows Threats Destroyer. Common options for achieving this include booting into Safe Mode, booting from a removable drive or loading a second OS, and any of these choices should allow you to scan your PC with suitable software and remove Windows Threats Destroyer and any related PC threats.
Since Windows Threats Destroyer is still newly-identified as of March 2012, you may want to update your anti-malware software before you attempt a scan. Although the scamware that Windows Threat Destroyer is based on are fairly old, Windows Threat Destroyer may include updates that make it more difficult to detect than its ancestors, and having an updated threat database will insure as much accuracy in threat detection as possible.
Windows Threats Destroyer, like other members of its family, is designed to attack Windows-based computers, and SpywareRemove.com malware researchers note that Linux, Mac and other operating systems should be safe from Windows Threats Destroyer attacks.



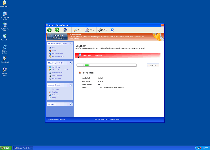
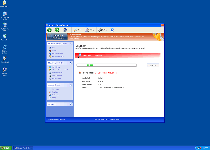
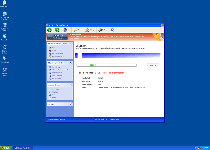
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\Protector-rxi.exe
File name: Protector-rxi.exeSize: 1.89 MB (1894400 bytes)
MD5: 89c3bd82bc57b2b7bdc4acd8b49b6b45
Detection count: 20
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: March 1, 2012
delete 3 trojans from my pc system.