Windows Web Combat
Posted: July 12, 2012
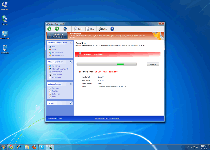
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
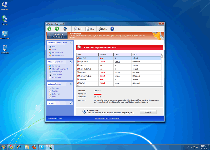
| Threat Level: | 2/10 |
|---|---|
| Infected PCs: | 24 |
| First Seen: | July 12, 2012 |
|---|---|
| OS(es) Affected: | Windows |
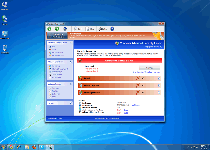
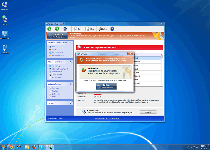
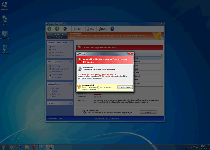
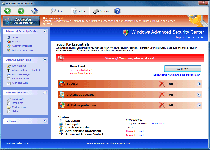 With all the outer looks of a real anti-malware program but none of the genuine anti-malware features that a reputable brand would boast, Windows Web Combat is a good example of looks being deceiving for little-known software. Since SpywareRemove.com malware research team has identified Windows Web Combat, not only as a rogue anti-malware scanner, but as an explicit member of the FakeVimes family of the same, you should be prepared for the possibility of unwarranted security changes, browser redirects and blocked security applications with any Windows Web Combat infection. Nonetheless, Windows Web Combat's most common and easily-detected symptoms are the various fake warnings and scans that Windows Web Combat uses to create a mockup of countless PC threats attacking your computer, and Windows Web Combat's security information should never be considered accurate or purchase-worthy.
With all the outer looks of a real anti-malware program but none of the genuine anti-malware features that a reputable brand would boast, Windows Web Combat is a good example of looks being deceiving for little-known software. Since SpywareRemove.com malware research team has identified Windows Web Combat, not only as a rogue anti-malware scanner, but as an explicit member of the FakeVimes family of the same, you should be prepared for the possibility of unwarranted security changes, browser redirects and blocked security applications with any Windows Web Combat infection. Nonetheless, Windows Web Combat's most common and easily-detected symptoms are the various fake warnings and scans that Windows Web Combat uses to create a mockup of countless PC threats attacking your computer, and Windows Web Combat's security information should never be considered accurate or purchase-worthy.
Windows Web Combat and the Battle for Control Over Your Computer
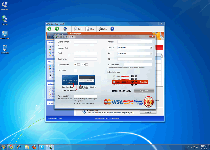
Windows Web Combat is unable to provide any of the anti-malware features that Windows Web Combat claims are worth your money, although its external appearance may initially obfuscate this. As scamware that launches right along with Windows, Windows Web Combat will display its fake pop-up alerts for phishing attacks, identity theft, Trojan infections and other PC threats without any regard for their accuracy or lack of such. Likewise, Windows Web Combat may also look as though Windows Web Combat can scan your PC, but its scanner results are predefined to include inaccurate lists of infections, as well as the scan results presented by its many clones which have among them Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0.
However, fake security features should be the least of your concerns in any Windows Web Combat infection, given that SpywareRemove.com malware experts have also spotted this class of rogue anti-malware programs using more severe attacks than simple pop-ups and simulated scans. Any infection by Windows Web Combat can also include such possible attacks as:
- Applications that are blocked under fraudulent pretenses. Blocked programs can include various types of security software, such as firewall utilities, anti-virus scanners, memory-monitoring tools and baseline Windows applications. Windows Web Combat may simply prevent the application from being run, or Windows Web Combat may delete Registry entries that are necessary for the application to function even if Windows Web Combat is disabled.
- Browser redirects that promote malicious sites or sites with questionable reputations. SpywareRemove.com malware researchers have found that online search-related redirects are particularly probable with Windows Web Combat and similar FakeVimes infections.
- Security settings that are changed to heighten your PC's susceptibility to future attacks from other PC threats besides Windows Web Combat. These changes can include browser settings that are changed in negative ways, as well as disabled Windows features like the UAC.
Knocking Windows Web Combat Out of the Ring for the Sake of Your PC's Safety
Contrary to its numerous protests, Windows Web Combat can be removed without registering Windows Web Combat, and SpywareRemove.com malware researchers strongly encourage this in lieu of spending any money whatsoever on Windows Web Combat. Despite this, the code '0W000-000B0-00T00-E0020' can be used for free if you still deem registering Windows Web Combat necessary or useful for deleting Windows Web Combat in the long term. Disabling Windows Web Combat entirely is also generally encouraged before you attempt to remove Windows Web Combat, and this can be done by, for example, booting your PC from a removable data storage device.
Windows Web Combat, like all FakeVimes-based PC threats, can be removed by qualified anti-malware products. Because Windows Web Combat is a recent addition to the FakeVimes family, your anti-malware software may require database updates before it can detect Windows Web Combat perfectly, although, in most cases, basic heuristic methods should suffice.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:Protector-[rnd].exe in %AppData% folder
File name: Protector-[rnd].exe in %AppData% folderMime Type: unknown/exe in %AppData% folder
Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd]HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXEHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exe
Ineed to uninstall windows web combat