XP Antivirus 2012
Posted: June 7, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 75 |
| First Seen: | August 9, 2011 |
|---|---|
| Last Seen: | May 6, 2024 |
| OS(es) Affected: | Windows |
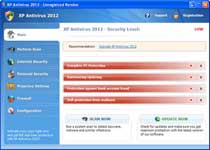 XP Antivirus 2012 is a new clone of rogue security software scams from the FakeXPA family. Even though XP Antivirus 2012 isn't capable of finding or removing threats from your PC, XP Antivirus 2012 will nevertheless pretend to do so by creating fake infection pop-ups and system scans that don't reflect the reality of your PC health. To lend additional credence to its claims, XP Antivirus 2012 will also hijack your browser and prevent certain programs from running. You should not give your credit card information to the criminals propping up XP Antivirus 2012, and instead remove XP Antivirus 2012 by using an actual anti-virus program.
XP Antivirus 2012 is a new clone of rogue security software scams from the FakeXPA family. Even though XP Antivirus 2012 isn't capable of finding or removing threats from your PC, XP Antivirus 2012 will nevertheless pretend to do so by creating fake infection pop-ups and system scans that don't reflect the reality of your PC health. To lend additional credence to its claims, XP Antivirus 2012 will also hijack your browser and prevent certain programs from running. You should not give your credit card information to the criminals propping up XP Antivirus 2012, and instead remove XP Antivirus 2012 by using an actual anti-virus program.
XP Antivirus 2012: A Fake Anti-Virus with Real Threats
XP Antivirus 2012 shares XP Antivirus 2012's appearance and harmful behavior with other rogue security programs in the same subgroup, including Antivirus 2010, Antivirus 360, AntivirusBEST, Nortel Antivirus, Alpha Antivirus, Cyber Security, MaCatte Antivirus 2009, Eco Antivirus, Antivir, Personal Security, Ghost Antivirus, Antivirus 7, Antivirus GT, Earth Antivirus, Antivirus 8, AntivirusProfessional, AVG Antivirus 2011, E-Set Antivirus 2011, XP Antivirus 2010 and XP Antivirus 2013. Although you may only see XP Antivirus 2012 on a computer that runs Windows XP, there are other clones for other operating systems like Windows 7 Antivirus 2012 and Vista Antivirus 2012.
XP Antivirus 2012 runs without your permission by adding startup entries directly into the default Windows loading configuration. In most cases, using Safe Mode will let you launch Windows without launching XP Antivirus 2012, although more extreme circumstances might require booting Windows from a CD.
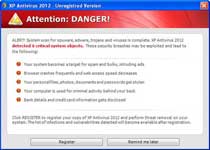
Once it's launched, XP Antivirus 2012 will pretend to scan your computer for threats, and fake finding many different types of infections. Alongside XP Antivirus 2012's fake scans, XP Antivirus 2012 will also create realistic-looking pop-ups that warn you about threats like the following:
System warning!
Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer.
System warning!
Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start.
Security Alert!
Your computer is being attacked from a remote machine !
Block Internet access to your computer to prevent system infection.
Critical Warning!
Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended)
You should avoid taking XP Antivirus 2012 at its word and purchasing a key to use XP Antivirus 2012's 'registered' version, since XP Antivirus 2012 can't find or delete any real computer threats. If you've already done this by mistake, speak to your credit card company and have the card canceled, to avoid further incidents of fraudulent charges.
What Else XP Antivirus 2012 Holds in Store for Your Victimized PC
XP Antivirus 2012 and related rogue security programs have also acquired a reputation for hijacking web browsers. Hijacks are often used to redirect browsers to harmful sites like the XP Antivirus 2012 homepage. They may also block your ability to visit sites by creating fake error screens, or simply redirecting you with no other excuses.
Other programs besides your web browser may also be attacked by XP Antivirus 2012, primarily for the purpose of preventing them from running at all. This may make diagnostic software like the Task Manager and anti-virus software inaccessible to you, until you get rid of XP Antivirus 2012.
Safe Mode or a CD-based system boot will let you stop XP Antivirus 2012 from launching itself. Removing XP Antivirus 2012 by manually deleting XP Antivirus 2012's files is inadvisable, unless done by an expert; in most cases, using automated security software to delete XP Antivirus 2012, is safer for your computer.
Aliases
More aliases (48)
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%SystemDrive%\Documents and Settings\adrian.agnew\Local Settings\Application Data\mmc.exe
File name: mmc.exeSize: 344.06 KB (344064 bytes)
MD5: 1434c50385a6e81f7ba5d081aafa9e0e
Detection count: 95
File type: Executable File
Mime Type: unknown/exe
Path: %SystemDrive%\Documents and Settings\adrian.agnew\Local Settings\Application Data
Group: Malware file
Last Updated: August 9, 2011
oqf.exe
File name: oqf.exeSize: 367.1 KB (367104 bytes)
MD5: 718b31c6d90a7731f88f92400cc1a212
Detection count: 93
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: August 9, 2011
C:\Users\<username>\fakereanbraviax trojans\vxe (2).exe
File name: vxe (2).exeSize: 339.96 KB (339968 bytes)
MD5: 45d35cc0fbd7ffdf35f7ef86730cdc15
Detection count: 21
File type: Executable File
Mime Type: unknown/exe
Path: C:\Users\<username>\fakereanbraviax trojans\vxe (2).exe
Group: Malware file
Last Updated: May 6, 2024
%ALLUSERSPROFILE%\QuestScan\questscan172.exe
File name: questscan172.exeSize: 26.11 KB (26112 bytes)
MD5: 5bffd0b4493b22b8385b73e17638fff6
Detection count: 19
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\QuestScan
Group: Malware file
Last Updated: August 12, 2011
C:\rogues\w32 fakerean braviax\aka.exe
File name: aka.exeSize: 339.96 KB (339968 bytes)
MD5: 8759b185ac5d846a6665f47e0a9bdf13
Detection count: 9
File type: Executable File
Mime Type: unknown/exe
Path: C:\rogues\w32 fakerean braviax\aka.exe
Group: Malware file
Last Updated: May 6, 2024
%ALLUSERSPROFILE%\QuestScan\questscan173.exe
File name: questscan173.exeSize: 26.11 KB (26112 bytes)
MD5: e53fb610fb4c8800db4dd1209066d2e0
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\QuestScan
Group: Malware file
Last Updated: August 12, 2011
%AllUsersProfile%\[RANDOM CHARACTERS].exe
File name: %AllUsersProfile%\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS].exe
File name: %AppData%\Local\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS].exe
File name: %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%Temp%\[RANDOM CHARACTERS].exe
File name: %Temp%\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%UserProfile%\Local Settings\Application Data\opRSK
File name: %UserProfile%\Local Settings\Application Data\opRSKGroup: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Classes\.exe "(Default)" = 'exefile'HKEY_CURRENT_USER\Software\Classes\.exe "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon "(Default)" = '%1' = '"%UserProfile%\Local Settings\Application Data\.exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile "(Default)" = 'Application'HKEY_CURRENT_USER\Software\Classes\exefile "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon "(Default)" = '%1'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\.exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "IsolatedCommand" – '"%1" %*'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe"'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\.exe" /START "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\commandHKEY..\..\..\..{RegistryKeys}HKEY_CLASSES_ROOT\.exe\DefaultIcon "(Default)" = '%1'HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\.exe" /START "%1" %*'HKEY_CLASSES_ROOT\.exe\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CLASSES_ROOT\.exe\shell\runas\command "(Default)" = '"%1" %*'HKEY_CLASSES_ROOT\.exe\shell\runas\command "IsolatedCommand" = '"%1" %*'HKEY_CLASSES_ROOT\exefile "Content Type" = 'application/x-msdownload'HKEY_CLASSES_ROOT\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\.exe" /START "%1" %*'HKEY_CLASSES_ROOT\exefile\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CLASSES_ROOT\exefile\shell\runas\command "IsolatedCommand" = '"%1" %*'
Additional Information
| # | Message |
|---|---|
| 1 | Critical Warning! Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended) |
| 2 | Security Alert! Your computer is being attacked from a remote machine! Block Internet access to your computer to prevent system infection. |
| 3 | System warning! Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer. |
| 4 | System warning! Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start. |
I just got this virus today and i'm having trouble removing it. I located the file its eae.exe on my computer. I can remove it from the processes but when i try to open any program it comes back. When i delete it and try to open any program a message comes up saying windows was not able to locate the file. I can't even open my registry too. So i restore the eae.exe i can open a program but it xp ativurs 2012 opens as well. I haven't had many problems removing viruses but this ones stumping me. Need help. Thanks
As Jacob before me has written, I am unable to open anything without the box appearing. I tried to go in and delete the program, but it will not let me have access to any programs at all. Please help!
is there any software disc I can buy and insert into my computer to fix this? I have had no computer usage for 3 days now- need my computer back - best buy wants to charge $250 - my computer is 7 years old and only has 512 MB of memory - might as well buy new computer- plases let me know if anyone knows if buying McAfee or Norton, AVG or Avira ( Avira's free version did not prevent the virus from getting on my computer so I dont recommend it) PLEASE LET ME KNOW
Hey,
I've got the virus and all help I can find online is to download a program but that's impossible from my infected pc as the malware does not let me open up any Internet browser! So how do I delete it as a 'non expert'??
Thanks for any help,
H
THIS IS HIGHLY NOTORIUS AND I SEEM TO BE HAVING THE SAME PROBLEM.NOTHING SEEMS TO WORK.KINDLY HELP?
What to do when can't even get past deskmtp. Is there a way to copy repair suggestions on a memory stick and insert in to affected laptop
This virus re-writes the registry to intercept the EXE class handler to point to itself. If you delete the virus EXE, then you can't run any EXE's on your machine, so you need to download and run the REG fragment that restores the machine's default EXE behaviour.
Hey just restore it back to a checkpoint before you got it it worked for me hope this helps
I turned computer off for 1 week and it disappeared.
It keeps rewriting itself. My neighbor told me to use safe mode. What is safe mode and how will it help me remove XP Antivirus 2012? it is completely annoying every time i use my PC
turn off the computer for one week seems the most promising option at this stage...i will take mine to a shop...luckily it's only on my laptop...but it certainly seems a persistent fkkd up kinda program...like others I cannot access anything..it blocked my avast so no point trying to delete it..can't uninstall anything...can't open anything without the fkkr poppin up...here a very pissed off customer!
I've had a go-round with this thing and really do not want to take it to the Geek Squad, but glad to know they are available if I can't get it deleted. Just for fun I zipped every one of it's files which sent it into enough of a spin that I was able to finally get onto the internet and download an anti-malware file ... which was promptly eaten by the viral program. This note is being written from a totally different computer, and my plan is to restore my computer to an earlier date. The directions I will follow are found at: http://technet.microsoft.com/en-us/library/bb457025.aspx and appear to be well within my limited computer savvy to follow. Good luvk to everyone else. I can't afford to shut my 'puter off for a week and hope it goes away! 🙂
restore to a previous checkpoint seems to have eliminated the problem for me also....
Hay people, I haven\'t seen this listed on here yet. But what I was able to do to get internet restored to my computer was go into the setting for the lan and change if from automatically get ip address to manually input it. so it you would use another computer on your network to get the ip settings by hitting the windows key + R. then type in CMD and in command prompt type in ipconfig. use those settings to manually input your ip address. so it should be something like 192.168.1.??? so if yours is 192.168.1.104 you should chose like 192.168.1.135 and your DNS would be 192.168.1.1. This opened up the internet for me to use other programs to remove the virus. you should also download and run a program called CCleaner.
so, I don't see any comments where anyone actually paid these people for anything (other than myself, I guess? STUPID, STUPID, STUPID!!) is there any chance anyone might know where or to whom a complaint can/should be filed? any way to track where my payment went? luckily, what I gave them was the LAST $$ in my account, so they won't be getting any use out of that....by the time my DD hits, I'll have the information changed....OMG!! what a sucker I am!!!
I was able to get rid of XP Antivirus 2012 by following the directions in this video.
http://www.youtube.com/watch?v=qi4MomWaLEM
The programs used are Rogue Killer and Malwarebytes Anti-Malware. The rogue killer link he gives doesn't work anymore. So, you will have to download that from somewhere else. I recommend downloading the install files on a computer that isn't infected and transferring them to the desktop of the infected computer with a flash drive.
I restored my computer to a setpoint from about a week before and the xp anti virus is gone. thanks for the tips,
My computer is full with virus. I would like it to speed up faster.
The 2012 version of this fake antivirus is considerably more of a problem than the 2011 and older versions of it. I'm surprised that many of the well-known antivirus programs still don't catch and prevent this. Anyhow, removal will be time consuming and if you don't know what you're doing on a computer, it's probably not a good idea to attempt it yourself. You can attempt to use a system restore, but most viruses save themselves where they won't be erased and then reappear weeks or even months down the road, so it's better to really remove it instead of doing a system restore. But it does take work.
One thing about this virus is that you don't need safe mode at all to remove it. Start your computer. Once you are on the desktop, right click on the taskbar and choose Start Task Manager. Go to the Processes tab and look for a 3 letter filename (like dyx.exe). You will have some legitimate ones (mdm.exe and jqs.exe are a couple legitimate ones). Take note of the filename because you will need it. Click on that filename and then choose End Process and say OK. The fake antivirus popup will be closed if it was open. Leave Task Manager open in case it comes back.
Next, you want to fix the EXE files. To do so, copy the following into Notepad on a different computer and save it as fix.reg (make sure it doesn't save as fix.reg.txt). Copy it to your infected computer and double click on it. If you named it correctly, it will ask if you want to import it to the registry. Choose Yes. Now all your EXE files will work again (and so will your web browsers).
(Copy what is between the ------- lines, without copying the ------- lines):
------
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
[HKEY_CLASSES_ROOT\.exe\PersistentHandler]
@="{098f2470-bae0-11cd-b579-08002b30bfeb}"
[HKEY_CLASSES_ROOT\exefile]
@="Application"
"EditFlags"=hex:38,07,00,00
"TileInfo"="prop:FileDescription;Company;FileVersion"
"InfoTip"="prop:FileDescription;Company;FileVersion;Create;Size"
[HKEY_CLASSES_ROOT\exefile\DefaultIcon]
@="%1"
[HKEY_CLASSES_ROOT\exefile\shell]
[HKEY_CLASSES_ROOT\exefile\shell\open]
"EditFlags"=hex:00,00,00,00
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\exefile\shell\runas]
[HKEY_CLASSES_ROOT\exefile\shell\runas\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\exefile\shellex]
[HKEY_CLASSES_ROOT\exefile\shellex\DropHandler]
@="{86C86720-42A0-1069-A2E8-08002B30309D}"
[HKEY_CLASSES_ROOT\exefile\shellex\PropertySheetHandlers]
[HKEY_CLASSES_ROOT\exefile\shellex\PropertySheetHandlers\{B41DB860-8EE4-11D2-9906-E49FADC173CA}]
@=""
[HKEY_CLASSES_ROOT\exefile\shellex\PropertySheetHandlers\PifProps]
@="{86F19A00-42A0-1069-A2E9-08002B30309D}"
[HKEY_CLASSES_ROOT\exefile\shellex\PropertySheetHandlers\ShimLayer Property Page]
@="{513D916F-2A8E-4F51-AEAB-0CBC76FB1AF8}"
[HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command]
@="C:\Program Files\Mozilla Firefox\firefox.exe"
[HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command]
@="C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode
[HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command]
@="C:\Program Files\Internet Explorer\iexplore.exe"
[-HKEY_CURRENT_USER\Software\Classes\.exe]
[-HKEY_CURRENT_USER\Software\Classes\pezfile]
[-HKEY_CLASSES_ROOT\.exe\shell\open\command]
----------
Before continuing, verify that the fake antivirus is still closed in Task Manager. If it opened again, End Process on it again.
Now open regedit (XP: Start Menu > Run > regedit > OK; Vista/7: Start Menu > type regedit in the box and hit enter). *** BE CAREFUL HERE -- Changing the wrong things in the registry can make Windows no longer work. ***
Do a search for the filename you found in Task Manager. Press Ctrl-F and type in the filename, for example dyx.exe . You're probably going to find it a lot. On the left side of regedit is a list of "folders" and the right side is what is in the folders. When it finds the file, look on the left side. If the folders appear something like this:
AHX
--> DEFAULT ICON
--> SHELL
--> OPEN
--> COMMAND
(The AHX will be a random set of 2 or 3 letters without a . in front of it. The folders in there should include SHELL > OPEN > COMMAND). If that's what you see, right click on the AHX folder (or whatever 2-3 letters are there) and choose Delete and say OK. If it's anything else, the right click on the highlighted item on the RIGHT side of the screen and choose Delete. Press F3 to continue your search. Repeat this for everything you find. Keep pressing F3 until it says it's done searching the registry. Note that there could be 20-30 things you will have to delete.
Next, go to the Start menu and click on Search. Choose All Files. Don't enter a filename, but click on the When Was It Modified and then select the date range of the current date. * If you first saw the fake antivirus before the current date, then select the date you first saw it. * So, if I saw this on 12/16/11, I'd enter that for the from AND to dates. Press Search and wait. It will take awhile to search. **Not everything that appears will be related to the virus, so don't start deleting everything!!**
Once the search finishes, start by looking for the filename for the virus (such as dyx.exe) and right click on it and choose Delete. ** Do not run it or you'll have to start over. ** Next, expand the columns so you can see the path really well. Look for anything that includes macrovision. Delete any that are listed there. Look through the filenames for anything that looks like a web address (especially to what sounds like a porn site). Delete all of those. If you know what you're doing, you can also check for other files that may be related to the virus. These vary, so it's not possible to just list everything you have to delete.
Finally, go to the Start Menu and click on Control Panel. Double click on Java. Under Temporary Internet Files, click Settings. Then click Delete Files. This is important because you could be reinfected by not removing these files.
You should not be free of the virus. I recommend also downloading and running SpyBot S&D. It's a free malware/trojan scanner. Just be careful with it as it can list legitimate items in its results. You can expand each item it finds to see the path. If the path is for something legitimate such as your antivirus software or some other program you use, then uncheck it before clicking Fix.
You should also delete all temporary files. Go to the Start Menu and click Run (for XP) or type in (for Vista/7): %temp% and press OK or hit Enter. Delete everything in there. If it says it can't delete something, just skip that item and continue deleting the rest. Then also open C:\Windows\Temp\ and delete all files in there. Again, if something can't be deleted, just skip it.
In most cases, this will fix your problems. But keep a very close eye on your computer for awhile to make sure it doesn't come back. This virus varies and can hide itself to a limited extent. Following instructions to remove it will work in most cases, but it is possible that you'll need someone who knows what they are doing to sit there and remove it directly.
I hope this helps people. One thing you might also want to do is to get an ad blocker addon for your browser such as Ad Block Plus for Firefox. Many of these kinds of viruses come from ads on legitimate websites. By blocking the ads, you have a lower chance of getting these kinds of viruses. Good luck everyone.
What a mess .........and scary too! I had XP Antivirus 2012 virus. After alot of reading, I tried changing the computer date up 10 days and then restarting. Not a good idea any more. It really "F'ed " things up. I copied and pasted the above Windows Registry Editor Version 5.00 and followed those instructions. Then I went to Start, programs, accessories, system tools, and clicked on the system restore. This took a couple of minutes to even register. Very slow....Finally, the RESTORE screen. Hooray. I restored the computer back 2 days before the attack. Wow, It worked. Now I went and loaded "Malwarebytes Anti Malware software" from a flash drive, then ran the program. this takes a while. Be patient. Once loaded, run the scan. It found a "Trojan" called.....cpnprt2.cid (a coupon print driver known to have been hacked)
I then deleted Spybot S&D, which didn't catch the culprit, and Microsoft security essentials, which also didn't catch the culprit. I loaded Norton Security Suite from my Xfinity/comcast provider and am back up and running. I did notice that
while I was checking out e-mail and some other files several hours later, I noticed that a small Norton window in the lower right hand corner of the screen appeared and said it was dealing with a "Trojan Virus" and then said it had eliminated the threat. That little prick was still hiding in there! Here it is about 36 hours later and all is well.
For reasons I don't understand, I was able to get the computer to run after leaving it idle for about a week. I ran Spybot, which took care of some of the other problems, but did not get rid of the XP 2012 mess. Internet access was marginal with Firefox, couldn't get on line with Explorer. I'm going to try some of the registry solutions mentioned above.
hello dan cud dos from indiana im also removing this asshole deleted some temp files from my computer and edited the registry. but mine wasnt stoping the opening of i.e or fire fox , i think its because i stoped its process from opening every time it opened.i call it killin the program it rly help when things start to slow down just be careful
you can open task manager and right click on the 'xp virus' and hit "go to process".Task manager will show you what its process name is which will probably be something like "ubk.exe". Then right click that and hit "end process" and the messages will stop and allow you to use a real virus remover . Also if you were using 'internet expl' when you got the virus don't use it again! Just use another browser if possible (the virus somehow inserts itself into the browser it downloaded itself from), if not download one in 'safe mode w/networking' along with a virus remover.
Thank you, Thank you, Thank you. It worked for me.
mE RUSKIE WILL F UP YOU COMPUTTER WIITH VIRUS AND TAKE MONEY BACK TO MUTTER RUSSIA
Hi Jeremy,
Your detailed instructions have saved my day. I was looking all around for solutions and following your instructions solved my problem. Especially by running the regedit instructions (saved in notepad) i was able to open all my exe programs again. 1 comment though, i did not have access to another computer (to create the fix.reg) and on my system i was not able to open the notepad.exe..because of the virus..a solution is if you click the notepad.exe program it will open up a list of programs to open the file with..here i selected notepad again and it opened the content in a notepad program, i did a select all, then delete and then copied the regedit instructions and then saved it as 'fix.reg' and then double clicked it and my registry got updated and i am able to poen the exe files again. Thanks a Lot.
OMG This helped sooooo much. I was able to delete ALL the reg entries and paste back in the reg fix you provided. THANK YOU. THANK YOU. THANK YOU. This was a hot mess. I have not had this much trouble cleaning out a virus since \"nimda\" LOL and that was several years back. Believe it or not I have been cleaning this thing out for the past 9 hours. I got it cleaned out and didnt realize that it destroyed the exe files to everything. so that reg fix is esential to cleaning out this 2012 virus. Thanks again. Advise to anyone else who has this to follow these instructions and dont forget to copy the reg fix to a flash drive. This does work and then install a real antivirus program. avg did not stop this.
I got a virus and downloaded avira to remove it. But it didnt work, so I decide to uninstall avira.
Control panel can't remove avira! Plz help me! Thx in advance!
Windows security center says that my firewall is off, but Avira has a firewall, how do I turn it on?
When avira finds a virus in my computer, which option should i choose to completely delete the virus from my comuter? (quarantine, deny access, etc.) I am running windows 7
I've tried many things but can't get streaming to work. I've installed the webcam part and that is working but streaming doesn't work for me. I get the "Media not found" dialog box and have checked that the entry in /usr/share/red5/conf/context.xml and it does have between the outer . Can you let me know what to look for? any error log or ways to trace what's going on? I am using Kaltura CE 4.0 VMWare version and currently have videos that I've uploaded before and was trying to use RTMP streaming using those. Am I supposed to re-encode those existing video again for RTMP to work or it should work as is? They are a mixture of MP4 and FLV files and all of the returned "file not found" error when I played them using the Embedded Player (Progressive works fine). Thanks for your help.
I wanted to know how to delete the internet security out of my computer when i turn on the computer
How come XP malware alerts me when my PC is at idle? I don't get it. Somehow I cannot find any removal of this in add/remove programs. Shouldn't this be listed? So confused. Please help!