Cerber Ransomware
Posted: March 4, 2016
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 12,379 |
|---|---|
| Threat Level: | 10/10 |
| Infected PCs: | 168,486 |
| First Seen: | March 4, 2016 |
|---|---|
| Last Seen: | March 7, 2025 |
| OS(es) Affected: | Windows |
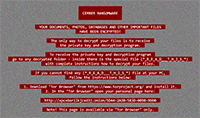 The Cerber Ransomware is a file encryptor that takes your data hostage for the sake of selling it back in return for Bitcoin currency. The general unreliability of this means of saving your files causes it to be discouraged as a solution when, instead, a sufficiently sound backup strategy can make the Cerber Ransomware's attacks relatively ineffectual. Due to the danger that the Cerber Ransomware poses to your system, data, and Web browser, malware analysts rate the Cerber Ransomware as a significant threat that should be uninstalled by dedicated anti-malware tools.
The Cerber Ransomware is a file encryptor that takes your data hostage for the sake of selling it back in return for Bitcoin currency. The general unreliability of this means of saving your files causes it to be discouraged as a solution when, instead, a sufficiently sound backup strategy can make the Cerber Ransomware's attacks relatively ineffectual. Due to the danger that the Cerber Ransomware poses to your system, data, and Web browser, malware analysts rate the Cerber Ransomware as a significant threat that should be uninstalled by dedicated anti-malware tools.
Making Deals with Con Artists for What's Yours
The Cerber Ransomware is a Trojan that uses file encryption (a data rearranging process often utilized in programs like file compressors) as a method of taking work and information hostage. Although the Cerber Ransomware's attacks are very similar to past threats like the Buddy Ransomware or the HydraCrypt Ransomware, this threat does exemplify the continued reliance fraudsters have on specific ransom techniques and technology. Like most threats the Cerber Ransomware is installed through non-consensual methods, including e-mail attachments, Web page-based exploits or even other Trojans, such as Zlob.
The Cerber Ransomware scans for non-OS files on any accessible hard drives and puts them through an encryption routine, with the key for decrypting them being specific to each infection. Besides attacking media formats like DOC, MP4, AVI, or HTML, the Cerber Ransomware also targets work-oriented ones, such as SQL databases, Excel spreadsheets and PowerPoint presentations. The Cerber Ransomware also inserts the '.cerber' file extension after each encrypted file name, and then places no less than three formats of ransom instructions in the same directory.
The Cerber Ransomware emphasizes time restrictions as an additional factor in forcing its victims to pay its ransom, and even includes a countdown timer in one of its ransom messages. While malware experts saw no cases of the Cerber Ransomware attacks deleting the encrypted files, the Cerber Ransomware does claim that its ransom cost will increase after a set amount of time. Like many file encryptors previous to it, the Cerber Ransomware hinges on demanding the victim's use of both TOR (an anonymous Web browsing application) and Bitcoin transactions for selling the decryption to you.
The Cheapest Cost of Getting Your Files Back
While threatening file encryptors often circumvent any local backups, such as Windows restore points, all PC users have other methods of saving their files from threats like the Cerber Ransomware. Con artists have no compulsion to follow through on providing any decryption services or applications after taking payments, and, in at least some cases, a threat even can be coded in such a way as to render conventional decryption impossible. Considering all of these factors, malware analysts always suggest that you use multiple, remote backups as an easy and efficient way of stopping the Cerber Ransomware from causing long term damage to your information.
Even without any risks to your data, the Cerber Ransomware always should be removed from your PC, and assumed to be a security breach equivalent to that presented by other, invasive Trojans. Common side effects unrelated to ransom tactics reported in conjunction with the Cerber Ransomware attacks include browser hijackings and disabled Web downloads, particularly in association with attempts to install new security programs. Accordingly, your pre-installed anti-malware products are the easiest solutions for deleting the Cerber Ransomware. Rebooting your PC with the additional protection of Safe Mode, or booting from a safe USB drive, are two tactics that can help you regain access to any blocked security tools.
However, for the time being, the Cerber Ransomware's con artists will continue profiting off of less cautious PC owners who don't protect their data from easily-implemented attacks.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%APPDATA%\README.hta
File name: README.htaSize: 63.11 KB (63113 bytes)
MD5: 777e13c9a5cad4e1d2134d5104188ff6
Detection count: 101
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
u.exe
File name: u.exeSize: 63.72 KB (63723 bytes)
MD5: 3dabcb3463ab266e734c83285c977106
Detection count: 76
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
%APPDATA%\wP6fT.exe
File name: wP6fT.exeSize: 322.56 KB (322560 bytes)
MD5: 731279e3c09f8e52a849c0a9c1043bb5
Detection count: 72
File type: Executable File
Mime Type: unknown/exe
Path: %APPDATA%
Group: Malware file
Last Updated: July 18, 2017
%APPDATA%\_HELP_HELP_HELP_KJ2P.hta
File name: _HELP_HELP_HELP_KJ2P.htaSize: 75.78 KB (75787 bytes)
MD5: 6689ad9f43ab19a1ccfad9db6a16b772
Detection count: 71
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_GLP9_.hta
File name: _HELP_HELP_HELP_GLP9_.htaSize: 75.86 KB (75864 bytes)
MD5: 5f7533c663ddb4c0ae4dbbaafb50d491
Detection count: 60
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_SUXEZY_.hta
File name: _HELP_HELP_HELP_SUXEZY_.htaSize: 75.9 KB (75904 bytes)
MD5: 5190e890725bf431ba44001e190c70f5
Detection count: 56
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_READ_THI$_FILE_DB3DT9_.hta
File name: _READ_THI$_FILE_DB3DT9_.htaSize: 77.05 KB (77053 bytes)
MD5: 7476a75b0680d99f5338b886bc7def62
Detection count: 54
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_5B3HEZ6.hta
File name: _HELP_HELP_HELP_5B3HEZ6.htaSize: 75.78 KB (75787 bytes)
MD5: b10e6f69d0c16008410b5c8cfaae0138
Detection count: 53
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_2R9I63OS.hta
File name: _HELP_HELP_HELP_2R9I63OS.htaSize: 75.78 KB (75787 bytes)
MD5: a2daec078c54bb6bc5e96038a1506f2c
Detection count: 34
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_HUUKTW_.hta
File name: _HELP_HELP_HELP_HUUKTW_.htaSize: 75.86 KB (75864 bytes)
MD5: 0224da72bc3638b351cf509cdfc443c2
Detection count: 30
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%USERPROFILE%\Start Menu\Programs\Startup\_HELP_HELP_HELP_RSHI_.hta
File name: _HELP_HELP_HELP_RSHI_.htaSize: 75.9 KB (75904 bytes)
MD5: a46e5f2ce8a20bbb8548959debb9ac0c
Detection count: 23
Mime Type: unknown/hta
Path: %USERPROFILE%\Start Menu\Programs\Startup
Group: Malware file
Last Updated: April 15, 2017
%USERPROFILE%\Start Menu\Programs\Startup\_HELP_HELP_HELP_STOV8H1_.hta
File name: _HELP_HELP_HELP_STOV8H1_.htaSize: 75.86 KB (75864 bytes)
MD5: 1632ca0953d5499bf251455159a80ea0
Detection count: 14
Mime Type: unknown/hta
Path: %USERPROFILE%\Start Menu\Programs\Startup
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_ND8FZ.hta
File name: _HELP_HELP_HELP_ND8FZ.htaSize: 75.78 KB (75787 bytes)
MD5: 041ef4b6a12e0b3165172884301b0d1e
Detection count: 12
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
c:\Users\<username>\appdata\roaming\{6b977300-2501-f740-f2c0-799d6aca21c2}\cmdkey.exe
File name: cmdkey.exeSize: 659.58 KB (659585 bytes)
MD5: 27cf39d205567505d840391e4761a7a0
Detection count: 12
File type: Executable File
Mime Type: unknown/exe
Path: c:\Users\<username>\appdata\roaming\{6b977300-2501-f740-f2c0-799d6aca21c2}
Group: Malware file
Last Updated: October 17, 2018
%APPDATA%\_HELP_HELP_HELP_XJ7UC8.hta
File name: _HELP_HELP_HELP_XJ7UC8.htaSize: 75.78 KB (75787 bytes)
MD5: 4ab1a256a5115d00fa7a3222936ddc03
Detection count: 7
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_XFCV_.hta
File name: _HELP_HELP_HELP_XFCV_.htaSize: 75.9 KB (75904 bytes)
MD5: 01ec9e50d17de043a23997d6562293ad
Detection count: 7
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_3NNARI.hta
File name: _HELP_HELP_HELP_3NNARI.htaSize: 75.78 KB (75787 bytes)
MD5: 0ef13a9213c456db231825061eec294c
Detection count: 5
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_HELP_HELP_HELP_L41VV_.hta
File name: _HELP_HELP_HELP_L41VV_.htaSize: 75.86 KB (75864 bytes)
MD5: c63b4a524713e4c5f3802463cb46dab8
Detection count: 5
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
%APPDATA%\_READ_THI$_FILE_L81EB65A_.hta
File name: _READ_THI$_FILE_L81EB65A_.htaSize: 77.01 KB (77010 bytes)
MD5: 2a6828d2ba37bb97efb4773619b80715
Detection count: 5
Mime Type: unknown/hta
Path: %APPDATA%
Group: Malware file
Last Updated: April 15, 2017
More files
Registry Modifications
File name without path# DECRYPT MY FILES #.html# DECRYPT MY FILES #.url# DECRYPT MY FILES #.vbs_README_.hta
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.