Fake Windows Restore
Posted: April 4, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 19,139 |
|---|---|
| Threat Level: | 10/10 |
| Infected PCs: | 728 |
| First Seen: | April 6, 2011 |
|---|---|
| Last Seen: | December 29, 2024 |
| OS(es) Affected: | Windows |
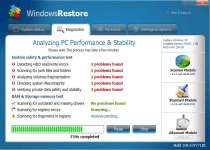 Fake Windows Restore may use the name of a Windows system utility, but actuality, Fake Windows Restore is a rogue defragmenter that shows fake alerts and causes file display errors. Registering Fake Windows Restore by purchasing the key is not recommended, since allowing Fake Windows Restore to persist in your PC will harm your system and any charges to your credit card are likely to be followed by other fraudulent abuses. You may think that your computer is seriously damaged due to Fake Windows Restore's alterations, but simply deleting Fake Windows Restore will reveal that little permanent harm has been done by the rogue security program.
Fake Windows Restore may use the name of a Windows system utility, but actuality, Fake Windows Restore is a rogue defragmenter that shows fake alerts and causes file display errors. Registering Fake Windows Restore by purchasing the key is not recommended, since allowing Fake Windows Restore to persist in your PC will harm your system and any charges to your credit card are likely to be followed by other fraudulent abuses. You may think that your computer is seriously damaged due to Fake Windows Restore's alterations, but simply deleting Fake Windows Restore will reveal that little permanent harm has been done by the rogue security program.
Fake Windows Restore is a Charlatan Malware Hiding Under the Windows Name
If you have a passing familiarity with other PC threats from the FakeSysDef family, you may notice that Fake Windows Restore looks and acts just like preexisting rogue security programs. A brief sampling of Fake Windows Restore's clones include System Defragmenter, Ultra Defragger, HDD Control, Win HDD, Win Defrag, Disk Doctor, Hard Drive Diagnostic, HDD Diagnostic, HDD Plus, HDD Repair, HDD Rescue, Smart HDD, Defragmenter, HDD Tools, Disk Repair, Windows Optimization Center, Scanner, HDD Low, Hdd Fix and Win Defragmenter. The only significant difference between these rogue security programs lies in their names and the fact that you may need different anti-malware software updates to detect and remove each one.
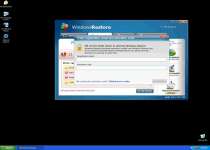
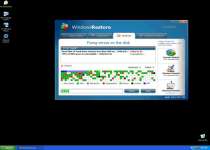
As a fake defragmenter or 'defragger' tool, Fake Windows Restore's foremost order of business is to show off a broad range of frightening-sounding error messages every time Fake Windows Restore scans your PC. Since Fake Windows Restore will launch itself from Windows without permission during any normal boot, you'll be seeing messages like these very often:
Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.
Critical Error
RAM memory usage is critically high. RAM memory failure.
Critical Error
Hard Drive not found. Missing hard drive.
Critical Error
Windows can't find hard disk space. Hard drive error.
Critical Error!
Windows was unable to save all the data for the file System32496A8300. The data has been lost. This error may be caused by a failure of your computer hardware.
Critical Error!
Damaged hard drive clusters detected. Private data is at risk.
System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.
It's vital to remember that these messages don't tell you anything about your computer's health, since Fake Windows Restore issues them automatically to lure you into providing your credit card number.
Restoring Your PC from Fake Windows Restore
Fake Windows Restore engenders further panic in the user by altering the display of files, folders, shortcuts and program list items. You may see folders that display the wrong contents or even nothing at all when using the standard Windows Explorer viewer. Once again, remember that these problems are just mirages cooked up by Fake Windows Restore – your files are safe and sound, even if you can't see them. Other common attacks by Fake Windows Restore include browser hijacks that redirect your browser to dangerous websites while blocking safe ones and blocked security application usage.
Restoring your system to true normalcy will require removing Fake Windows Restore. Manual removal by deleting individual files and Windows Registry entries should be reserved as a last resort, since it's likely to prove inefficient and may cause other system issues. A good anti-malware scanner that has built a reputation in the industry for quality will be able to remove Fake Windows Restore with few problems.
In some cases, faking registration by inputting the code '8475082234984902023718742058948' has been known to help by reducing Fake Windows Restore's attacks. However, it shouldn't be used as an alternative to removing Fake Windows Restore, which remains dangerous as long as Fake Windows Restore is on your computer.
Be certain to scan your entire system rather than stopping the scan once Fake Windows Restore is found; since Fake Windows Restore infects computers surreptitiously, you may also have Trojans or other linked infections. With patience, judicious application of threat database updates and scans launched in Safe Mode you should have no difficulty in getting your PC back out of Fake Windows Restore's clutches.
File System Modifications
- The following files were created in the system:
# File Name 1 %AllUsersProfile%\[RANDOM CHARACTERS].dll 2 %AllUsersProfile%\[RANDOM CHARACTERS].exe 3 %AllUsersProfile%\Application Data\[RANDOM CHARACTERS].dll 4 %AllUsersProfile%\Application Data\[RANDOM CHARACTERS].exe 5 %AllUsersProfile%\Application Data\~[RANDOM CHARACTERS] 6 %AllUsersProfile%\Application Data\~[RANDOM CHARACTERS]r 7 %AllUsersProfile%\~[RANDOM CHARACTERS] 8 %AllUsersProfile%\~[RANDOM CHARACTERS]r 9 %AppData%\Microsoft\[RANDOM CHARACTERS].exe 10 %Temp%\internetexplorerupdate.exe 11 %UserProfile%\Desktop\Windows Restore.lnk 12 %UserProfile%\Start Menu\Programs\Windows Restore\ 13 %UserProfile%\Start Menu\Programs\Windows Restore\Uninstall Windows restore.lnk 14 %UserProfile%\Start Menu\Programs\Windows Restore\Windows Restore.lnk
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = 'no'HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'yes'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "Hidden" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "ShowSuperHidden" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "CertificateRevocation" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnonBadCertRecving" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop "NoChangingWallPaper" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = '{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq2:/l2t:/v`w:/rbs:'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments"SaveZoneInformation" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS]"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS].exe"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "DisableTaskMgr" = '1'
Additional Information on Fake Windows Restore
- The following messages's were detected:
# Message 1 Internet Protection
External software tries to control variety of your system files. This may lead to breaking of some data in your system. Click here to protect remote access to your PC & delete these programs.2 Internet Protection
Your system has come under attack of harmful software. Click here to deactivate it.3 Internet Protection
Spyware.IEMonster process is found. The virus is going to send your passwords from Internet browser (Explorer, Mozilla Firefox, Outlook & others) to the third-parties. Click here for further protection of your data with Internet Protection.4 Internet Protection Firewall Alert
Your computer is being attacked from a remote machine!
Block Internet access to your computer to prevent system infection.
Attacker IP:
Attack type: RCPT exploit5 Internet Protection Firewall Alert
Internet Protection has prevent a program from accessing the Internet.
"iexplore.exe" is infected with Trojan. This worm has tried to use "iexplore.exe" to connect to remove host and send your credit card information.6 Internet Protection Firewall Alert
Suspicious activity in your registry system space was detected. Rogue malware detected in your system. Data leaks and system damage are possible. Please use a deep scan option.7 Internet Protection Firewall Alert
Warning
Keylogger activity detected!
Your account in social network is under attack. Click here to block unauthorized modification by removing threats (Recommended)8 Internet Protection
Your computer is under the infections threat. Run instant shield protection to safe your data and prevent internet access to your credit card information. Select this to run instant shield.9 Critical Error
Hard drive critical error. Run a system diagnostic utility to check your hard disk drive for errors. Windows can't find hard disk space. Hard drive error.10 Critical Error
Hard Drive not found. Missing hard drive.11 Critical Error!
Damaged hard drive clusters detected. Private data is at risk.12 Critical Error!
Windows was unable to save all the data for the file \System32\496A8300. The data has been lost. This error may be caused by a failure of your computer hardware.13 Critical Error
RAM memory usage is critically high. RAM memory failure.14 Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.15 Critical Error
Windows can't find hard disk space. Hard drive error.16 Windows - No Disk
Exception Processing Message 0x000001317 Activation Reminder
Windows Restore Activation
Advanced module activation required to fix detected errors and performance issues. Please purchase Advanced Module license to activate this software and enable all features.18 System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.19 Low Disk Space
You are running very low disk space on Local Disk (C:).
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%ALLUSERSPROFILE%\Application Data\dpdclcVKsU.exe
File name: dpdclcVKsU.exeSize: 548.86 KB (548864 bytes)
MD5: f99e9b62e80b2e491dde49f457fd9bdb
Detection count: 90
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: April 6, 2011
%ALLUSERSPROFILE%\Application Data\17555252.exe
File name: 17555252.exeSize: 479.23 KB (479232 bytes)
MD5: eadcd8526e23e8a1ed75ea969b841d7f
Detection count: 85
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: April 6, 2011
Registry Modifications
File name without pathWindows Restore.lnk
After removing Fake Windows XP Restore I have no shorcuts in my program list when I click on the Srart tab in my task bar. How can I restore these links to they will appear in my program drop down list?
Thanks...
Neal...
The virus may have moved them to C:\Documents and Settings\user\Local Settings\Temp\smtmp\1. It also seems to have moved quick launch to C:\Documents and Settings\user\Local Settings\Temp\smtmp\2.
My pc was hit by fake alert windows 7 fix on July 8, 2011 and Im still working on getting my pc back in proper working order.
The desktop was hijacked and all icons and shortcuts are gone. The Windows menu has been altered so that accessories, microsoft office, run, command prompt just to name a few have been hidden. I can access the files by going through control panel but I want my
computer back to the original state.
McAfee virus caught and quarintined the trojan, McAfee stinger, Malwarebytes anti-malware, Micrsoft IE fixer, microsoft security scanner, ESET scanner, all have been run on my pc, (I think that's all) hoping to correct the problem. The scans detected no threats, but has not corrected the missing items and desktop.
Restore points do not go back prior to the infection. What can I do?
Thanks,
Linda
my windows is not working well please repair it.