Vista Internet Security 2012
Posted: June 8, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 14,482 |
|---|---|
| Threat Level: | 8/10 |
| Infected PCs: | 187 |
| First Seen: | December 14, 2011 |
|---|---|
| Last Seen: | January 8, 2025 |
| OS(es) Affected: | Windows |
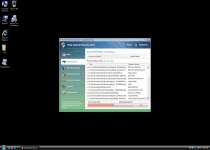
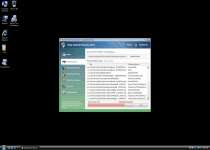
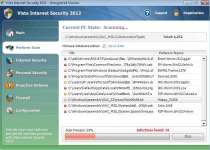 Vista Internet Security 2012 is a threat that fakes the appearance and functions of an anti-virus application. In spite of its seemingly benign purpose, Vista Internet Security 2012's actual features are related to creating false positive warnings, dominating your web browser and walling you off from any program that could delete Vista Internet Security 2012 and related threats. Avoid giving your credit card information to the criminals that market Vista Internet Security 2012, and remove Vista Internet Security 2012 from your PC, as quickly as is practical.
Vista Internet Security 2012 is a threat that fakes the appearance and functions of an anti-virus application. In spite of its seemingly benign purpose, Vista Internet Security 2012's actual features are related to creating false positive warnings, dominating your web browser and walling you off from any program that could delete Vista Internet Security 2012 and related threats. Avoid giving your credit card information to the criminals that market Vista Internet Security 2012, and remove Vista Internet Security 2012 from your PC, as quickly as is practical.
Vista Internet Security 2012: One of a Multitude of Fake Security Scams
Vista Internet Security 2012 will make no mention that it's a clone of other rogue security programs, but Vista Internet Security 2012 is sufficiently similar to many other rogue security programs that you can treat them as a singular entity. Here are just a few samples of other threats that are closely related to Vista Internet Security 2012: Win 7 Security 2012, Vista Total Security 2012, XP Total Security 2012, XP Internet Security 2012 and XP Anti-Spyware 2012.
Most Vista Internet Security 2012 infections are caused by Trojans that abuse browser security limitations to attack your computer discreetly. These Trojans, then, install Vista Internet Security 2012 or another threat, which will proceed to run whenever Windows starts.
Vista Internet Security 2012's automatic startup lets it create fake warnings about infections through simulations of system scans and security pop-ups. Although both these features look similar to a real anti-virus program's functions, Vista Internet Security 2012 doesn't try to detect real threats and is happy to alert you about fake ones.
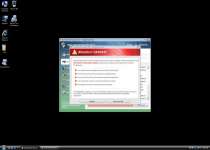
Some common Vista Internet Security 2012 pop-up warnings are:
System warning!
Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer.
System warning!
Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start.
Security Alert!
Your computer is being attacked from a remote machine !
Block Internet access to your computer to prevent system infection.
Critical Warning!
Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended)
These pop-ups may also reinforce the appearance of multiple infections by being used when Vista Internet Security 2012 prevents a program from running. You don't need to worry about a blocked program being infected or otherwise damaged; removing Vista Internet Security 2012 will let you use these applications normally once again.
Why You Don't Want Vista Internet Security 2012 Anywhere Near Your Browser
Along with creating fake anti-virus functions, Vista Internet Security 2012 will also interfere with your web-browsing activities by hijacking your web browser. Browser hijacks can manifest in multiple ways, all of them easy to spot:
- Vista Internet Security 2012 may change your homepage setting, so that you're brought to the Vista Internet Security 2012 homepage whenever you launch your browser.
- Vista Internet Security 2012 may also create fake website warnings that redirect you away from websites that aren't malicious. You can recognize these warnings by the inclusion of links to malicious websites, and the fact that they appear for websites that are normally benign like anti-malware sites.
- Other online content may also be changed to suit Vista Internet Security 2012's preferences. The most common browser hijacking play is to alter your search results to redirect you to hostile websites while maintaining the original search engine's appearance.
- Vista Internet Security 2012 hijacks may also cause pop-ups or advertisements to appear even if your browser appears to be closed.
You can avoid Vista Internet Security 2012 hijacks by booting from a CD or rebooting in Safe Mode. Either choice will let you use your browser without Vista Internet Security 2012 being active to attack it, thus giving you access to any required anti-malware websites and software.
File System Modifications
- The following files were created in the system:
# File Name 1 %AllUsersProfile%\wrdgt6knnhg8qwxst6hfljs11 2 %AppData%\Local\(random 3 letters).exe 3 %AppData%\Local\wrdgt6knnhg8qwxst6hfljs11 4 %AppData%\Roaming\Microsoft\Windows\Templates\wrdgt6knnhg8qwxst6hfljs11 5 %Temp%\wrdgt6knnhg8qwxst6hfljs11
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Classes\.exe “(Default)” = ‘exefile’HKEY_CURRENT_USER\Software\Classes\.exe “Content Type” = ‘application/x-msdownload’HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon “(Default)” = ‘%1? = ‘”%UserProfile%\Local Settings\Application Data\.exe” /START “%1? %*’HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “IsolatedCommand” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command “(Default)” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command “IsolatedCommand” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile “(Default)” = ‘Application’HKEY_CURRENT_USER\Software\Classes\exefile “Content Type” = ‘application/x-msdownload’HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon “(Default)” = ‘%1?HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\.exe” /START “%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “IsolatedCommand” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command “(Default)” = ‘”%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command “IsolatedCommand” – ‘”%1? %*’HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\.exe” /START “C:\Program Files\Mozilla Firefox\firefox.exe”‘HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\.exe” /START “C:\Program Files\Mozilla Firefox\firefox.exe” -safe-mode’HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\.exe” /START “C:\Program Files\Internet Explorer\iexplore.exe”‘HKEY..\..\..\..{RegistryKeys}HKEY_CLASSES_ROOT\.exe\DefaultIcon “(Default)” = ‘%1?HKEY_CLASSES_ROOT\.exe\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\.exe” /START “%1? %*’HKEY_CLASSES_ROOT\.exe\shell\open\command “IsolatedCommand” = ‘”%1? %*’HKEY_CLASSES_ROOT\.exe\shell\runas\command “(Default)” = ‘”%1? %*’HKEY_CLASSES_ROOT\.exe\shell\runas\command “IsolatedCommand” = ‘”%1? %*’HKEY_CLASSES_ROOT\exefile “Content Type” = ‘application/x-msdownload’HKEY_CLASSES_ROOT\exefile\shell\open\command “(Default)” = ‘”%UserProfile%\Local Settings\Application Data\.exe” /START “%1? %*’HKEY_CLASSES_ROOT\exefile\shell\open\command “IsolatedCommand” = ‘”%1? %*’HKEY_CLASSES_ROOT\exefile\shell\runas\command “IsolatedCommand” = ‘”%1? %*’
Andr/SMSRep-B), but it is far more scary when propagated by the ZeuS gang," says Fortinet security researcher Axelle