Win 7 Security 2012
Posted: June 9, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 49 |
| First Seen: | August 9, 2011 |
|---|---|
| Last Seen: | November 4, 2019 |
| OS(es) Affected: | Windows |
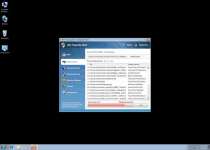
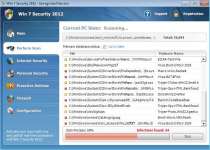 Win 7 Security 2012 is a recent clone of other rogue security programs that hide attacks on your web browser and other applications, by pretending to be anti-virus utilities. Though Win 7 Security 2012 looks the part of a trustworthy anti-virus program, it can only pretend to detect or remove infections, and has no functional redeeming features. Win 7 Security 2012 infection signs consist of browser hijacks, crashing or malfunctioning applications, and fake pop-up alerts, all of which can be solved once one removes Win 7 Security 2012.
Win 7 Security 2012 is a recent clone of other rogue security programs that hide attacks on your web browser and other applications, by pretending to be anti-virus utilities. Though Win 7 Security 2012 looks the part of a trustworthy anti-virus program, it can only pretend to detect or remove infections, and has no functional redeeming features. Win 7 Security 2012 infection signs consist of browser hijacks, crashing or malfunctioning applications, and fake pop-up alerts, all of which can be solved once one removes Win 7 Security 2012.
The Many False Alarms of Win 7 Security 2012
Win 7 Security 2012 is identical to other rogue security programs from the same line, including XP Security 2012, Vista Security 2012, Win 7 Anti-Virus 2012, XP Internet Security 2012 and XP Total Security 2012. Like them, Win 7 Security 2012 looks exactly like a normal anti-virus program, but most Win 7 Security 2012 installations are created by Trojans that attack your PC through browser security shortcomings.
While it's installed, Win 7 Security 2012 will use malicious Registry entries to launch itself every time you start Windows. Win 7 Security 2012 will abuse this positioning to fake system scans, always creating fake infection results regardless of how clean your PC might be.
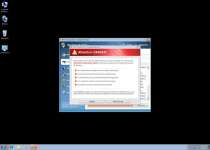
Just in case you're not convinced with the scans, Win 7 Security 2012 will also throw in fake system alerts like the following:
System warning!
Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer.
System warning!
Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start.
Security Alert!
Your computer is being attacked from a remote machine !
Block Internet access to your computer to prevent system infection.
Critical Warning!
Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended)
Win 7 Security 2012 will create these warnings no matter what your PC is doing, or what state of health your PC is in, so you don't need to worry about removing the supposed threats. Purchasing a registration key for Win 7 Security 2012, even just to make it stop its attacks, is strongly discouraged since it will give your credit card number to anonymous criminals.
If you've purchased Win 7 Security 2012 before realizing that it's a rogue security program instead of a real one, you should talk to your credit card company, and have both the charge and the credit card revoked.
More Reasons to Hurry and Uninstall Win 7 Security 2012
Win 7 Security 2012 will also attack your computer in several ways to make it look like multiple infections are troubling Windows, as well as to stop you from shutting down or deleting Win 7 Security 2012.
Any number of applications that aren't related to Win 7 Security 2012 may be shut down, as long as Win 7 Security 2012 is active. Closing Win 7 Security 2012 isn't a sure sign that Win 7 Security 2012 is deactivated, since Win 7 Security 2012 may remain open as a memory process, with no other visible signs of its influence. Application crashes that are caused by Win 7 Security 2012 can also use errors, such as the ones listed earlier to make it look like other infections are the root of the problem.
Win 7 Security 2012 may allow your web browser to function, but while doing so, Win 7 Security 2012 is likely to hijack it, instead of letting you use your browser unhindered. Win 7 Security 2012's browser hijacks can redirect you to malicious websites like the Win 7 Security 2012 homepage, create pop-ups, or halt you in your tracks before you can visit a safe website.
These attacks don't directly damage any of the applications targeted by Win 7 Security 2012, and so you can resume normal use of your computer as soon as you delete Win 7 Security 2012. The recommended removal method for Win 7 Security 2012 is to reboot into Safe Mode or boot from an external device before using an anti-malware application to scan your PC.
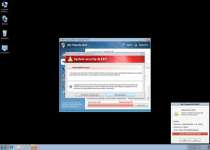
Since Win 7 Security 2012 is a new threat, keeping both your browser and your security software updated, is a significant step in defending your PC against possible Win 7 Security 2012 incursions.
Aliases
More aliases (38)
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%LOCALAPPDATA%\guv.exe
File name: guv.exeSize: 330.75 KB (330752 bytes)
MD5: ccfbc220b145119da810362bee192638
Detection count: 90
File type: Executable File
Mime Type: unknown/exe
Path: %LOCALAPPDATA%
Group: Malware file
Last Updated: August 9, 2011
%USERPROFILE%\Local Settings\Application Data\oey.exe
File name: oey.exeSize: 342.01 KB (342016 bytes)
MD5: c61f2496eb9da3c68d5c7129572be209
Detection count: 76
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Local Settings\Application Data
Group: Malware file
Last Updated: December 21, 2011
%USERPROFILE%\Local Settings\Application Data\cil.exe
File name: cil.exeSize: 330.24 KB (330240 bytes)
MD5: c634de87f21ee489080d2845c83a7566
Detection count: 65
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Local Settings\Application Data
Group: Malware file
Last Updated: December 21, 2011
%USERPROFILE%\Local Settings\Application Data\nur.exe
File name: nur.exeSize: 312.83 KB (312832 bytes)
MD5: 12d802c56e02606be89f0f7807833c83
Detection count: 41
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Local Settings\Application Data
Group: Malware file
Last Updated: December 22, 2011
%USERPROFILE%\Local Settings\Application Data\auf.exe
File name: auf.exeSize: 332.28 KB (332288 bytes)
MD5: 8b7f140ecd9593fee3c86b607afdc8bd
Detection count: 40
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Local Settings\Application Data
Group: Malware file
Last Updated: December 21, 2011
%USERPROFILE%\Local Settings\Application Data\mbw.exe
File name: mbw.exeSize: 333.31 KB (333312 bytes)
MD5: 1fe4e5893ef9b3b03dbc1bcea96923c4
Detection count: 40
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Local Settings\Application Data
Group: Malware file
Last Updated: December 21, 2011
%USERPROFILE%\Local Settings\Application Data\xwo.exe
File name: xwo.exeSize: 324.09 KB (324096 bytes)
MD5: 63edc3d8270df5d5da81ffc654a8e9be
Detection count: 23
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Local Settings\Application Data
Group: Malware file
Last Updated: December 21, 2011
%USERPROFILE%\Local Settings\Application Data\ugs.exe
File name: ugs.exeSize: 333.82 KB (333824 bytes)
MD5: 3241489ed05497104d196812ea610a8d
Detection count: 20
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Local Settings\Application Data
Group: Malware file
Last Updated: December 21, 2011
%LOCALAPPDATA%\uio.exe
File name: uio.exeSize: 339.96 KB (339968 bytes)
MD5: 953e9170934cfeccb7d4509a70274d4d
Detection count: 14
File type: Executable File
Mime Type: unknown/exe
Path: %LOCALAPPDATA%
Group: Malware file
Last Updated: August 9, 2011
%LOCALAPPDATA%\etq.exe
File name: etq.exeSize: 352.25 KB (352256 bytes)
MD5: 784b903aefb5b895c65b20da699db29c
Detection count: 6
File type: Executable File
Mime Type: unknown/exe
Path: %LOCALAPPDATA%
Group: Malware file
Last Updated: August 9, 2011
%LOCALAPPDATA%\afu.exe
File name: afu.exeSize: 335.87 KB (335872 bytes)
MD5: e86a084051e4fb393b282858357e6a79
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %LOCALAPPDATA%
Group: Malware file
Last Updated: August 9, 2011
%USERPROFILE%\Local Settings\Application Data\kpr.exe
File name: kpr.exeSize: 330.75 KB (330752 bytes)
MD5: 16eea9f8977d11cbd3a3d80fafdef3cb
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Local Settings\Application Data
Group: Malware file
Last Updated: December 21, 2011
%AllUsersProfile%\[RANDOM CHARACTERS]
File name: %AllUsersProfile%\[RANDOM CHARACTERS]Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS]
File name: %AppData%\Local\[RANDOM CHARACTERS]Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS].exe
File name: %AppData%\Local\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS]
File name: %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS]Group: Malware file
%Temp%\[RANDOM CHARACTERS]
File name: %Temp%\[RANDOM CHARACTERS]Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Classes\.exe "(Default)" = 'exefile'HKEY_CURRENT_USER\Software\Classes\.exe "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon "(Default)" = '%1" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile "(Default)" = 'Application'HKEY_CURRENT_USER\Software\Classes\exefile "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon "(Default)" = '%1'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "IsolatedCommand" – '"%1" %*'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Mozilla Firefox\firefox.exe"'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Mozilla Firefox\firefox.exe" -safe-mode'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Internet Explorer\iexplore.exe"HKEY..\..\..\..{RegistryKeys}HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CLASSES_ROOT\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'
Additional Information
| # | Message |
|---|---|
| 1 | Critical Warning! Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended) |
| 2 | Security Alert! Your computer is being attacked from a remote machine ! Block Internet access to your computer to prevent system infection. |
| 3 | System warning! Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer. |
| 4 | System warning! Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start. |
Hi, I want to thank the guy who posted this solution. I used manual way and it worked!
I was so embarassed with this "protector", so once again thank you!
I can't fix my computer! I tried using Windows Task Manager, but I don\'t know what the file is for Win 7 Security 2012. I looked at the place where it would give me the file names, but when I click on what it\'s giving me, it doesn\'t give me the file name. I\'ve basically been on every website to get rid of this virus, and i can\'t find anything. I\'ve been having this virus for a week. Can someone help me step-by-step manually?
Would not let me forward date my date/time as suggested. Used system restore which worked. Then scanned with malwarebytes. Nothing showed up on its scan. Really appreciate your efforts.
hello.
I was just randomly browsing stumbleupon, when i suddenly got this virus. i couldnt ipen my internet, i couldnt run a security scan, or anything. However, just go to accesories, go to system tools, click system restore, pick a date before you were infected with the virus. IT took my computer about 20 mionutes to reboot, but it was fine after that. So far, everythings been perfectly fine. let you know if it comes back!
I got this win 7 fake anti virus on my computor and i\'ve tried everything to get rid of it.. it won\'t let me do anything. System restore won\'t work and any of the solutions on this site. someone help!!
Megan - You can find out the file name for Win 7 Security by clicking the upwards arrow at the bottom right of your taskbar (next to the speaker symbol and date/time) and going to Customise.
This will show you a breakdown of the active notifications.
There should be one called Win 7 Internet Security 2012, underneath it (in italics) will have the .exe name that will appear in your Task Manager.
Mine was something random like 0.88272739431.exe - this appeared in my local files as listed above and could be deleted
I used mbam to locate the registry key that pointed to the exe then simply deleted the exe and all exe's associated with it. You may need to be in safe mode to do this as the virus doesn't allow you to access many applications, but I cannot confirm this as I immediately restarted in safe mode with F8 and took the above steps. SO... Thank you mbam!!!! 😀
Tried using the safe mode F8 boot thing and somehow I was able to get rid of some of the files and registry entries. It no longer pops up on my screen now but i still need to remove the program. Somehow it is still on my computer and I get one pop-up when I surf the internet. Any ideas? I will just use spyhunter and remove all of it if nothing else works. thanks for any help.
I got it... Nikki, thanks so much for the help!!!! This junk is GONE!
Entering 2233-298-3424 for the registration number allowed me to start using the internet for now to try to find something to get rid of this virus.
Hello,
I got the virus today. I tried system restore in safe mode and I also tried windows defender but the virus didn’t let me open any applications. Even in safe mode it seems like is the normal mode. I am not able to access the internet and I tried to download an antispysoftware in a different computer and then install it. But the computer doesn’t let me install it. I am stock.
I would appreciate any help.
i got to system restore via the control panel and am going that route
I was able to successfully remove the virus. You can launch the applications through "Run as Administrator" mode. So this is what I did:
1. Click on the small white up-arrow in the system tray, which is next to the clock and volume icons. Go to "customize" option. Here, you can see one of the entries as "Win 7 Security" or something in italics, and another name (process name) right above it.
2. Go to C:\Windows\System32 , and right-click on taskmgr.exe and click on "run as administrator".
3. Once taskmanager opens up, look for a 3-letter .exe file, and the description column with the process name you got in step 1. In my case, it was pqm.exe with "Microsoft directPlay..." process name.
4. Right click on the process and get the file location.
5. Kill the process and go to the file location, and delete it.
6. Re-start the laptop and press F8. You would get a repair option. Use this option to get to System restore utility and restore the system to an earlier date prior to virus attack.
7. You should be good now.
I found a very easy, simple, idiot-proof, FREE way to remove this asshole of a virus from Windows 7 in five minutes or less without
buying any bullshit software....
This method is DUH easy after you think about it.
step 1: restart the computer/laptop
step 2: press ESC to enter booting options
step 3: begin windows system restore
step 4: choose a recent date that was created by the last backup point Wwindows Update created for you
step 5: press enter
step 6: wait for the PC to finsh and reboot
Now the hard part: (which is definitely worth it to me)
Step 1: find these sons-a-bitches that made that virus
Step 2: fucking torture them
Step 3: painfully, slowly, brutally kill them!
Step 4: leave them outside near the center of a large city for public display as a warning to future virus makers
i got this virus today and i found the best way to find it was to go first to the bottom right corner of ur screen click the arrow and hit customize and find the win 7 mine was called something wierd then go to task manger and look for the process with the same name it will show u the .exe if u cant open anything right-click and run as admin hope this helps!!!
Guys, what Nikki said is completely correct...
"Nikki says:
June 26, 2011 at 9:09 am
Megan – You can find out the file name for Win 7 Security by clicking the upwards arrow at the bottom right of your taskbar (next to the speaker symbol and date/time) and going to Customise.
This will show you a breakdown of the active notifications.
There should be one called Win 7 Internet Security 2012, underneath it (in italics) will have the .exe name that will appear in your Task Manager.
Mine was something random like 0.88272739431.exe – this appeared in my local files as listed above and could be deleted"
The name of the file on my computer was tub.exe, found inside /username/AppData/Local/. Hope this helps!
Did a system restore and fixed my problem
Please Please help if you can. I followed the instructions pasted below and now anytime I try to run a program it does not know what program to use to launch it and ask for me to select a program. I am not getting the the treats from windows 7 security 2012 or whatever but I am still getting an Avast intrusion detection message. When I try to run a system restore via System Tools I get a run32dll file not found error. I tried to restore via the control panel and it says there are no backups. I have scheduled backups every week set. I am at a lost as to what to do. If I download ANY program the operating system doe snot know what program to use to open the executable file. I have been working on this for 4 hours and I have a lot of stuff on this Toshiba Laptop that I do not want to lose. I am afraid to shut it down because I am afraid it will not come back to life. Please any assistance would be appreciated.
No I do not have the backup disk unless I miraculously find them tomorrow. (Did I say that already?)
Thanks!
Lori
Nikki thank you so much you saved me from restoring my sons computer! Mine was called Microsoft play 8
Thank you all for putting up these steps to get rid of this crap!
step 1: restart the computer/laptop
step 2: press ESC to enter booting options
step 3: begin windows system restore
step 4: choose a recent date that was created by the last backup point Wwindows Update created for you
step 5: press enter
step 6: wait for the PC to finsh and reboot
THANK YOU SCOTT, IT WORKED FOR ME. I WAS ABLE TO REMOVE THE VIRUS FROM MY WIFE\'S AND MY UNCLES COMPUTER
I too was hit hard with Win 7 Security 2012, therefore I follow your instruction and it worked...thank you so much 🙂
While I was able to remove the worm/malware before I did it rendered my Windows firewall useless. I can no longer find the services required to run the firewall on my computer one is the Baseline filter engine service. Now as son as I connect some bot on the web reinfects the computer. Any idea how to restore the services required by windows firewall? There are no restore points left it appears to have high-jacked those too. This years version of this malware is the most destructive one I have encountered. In the past I had a friends machine get the 2010 variant and it was easy to repair.
I am in full support of the hard part 🙂
I bought this system and now can't activate it because I wasn't given the Reg Key.
I also just recently picked up this virus (Windows 7 Home Security 2012).
Although my computer was incapacitated for all practicle puirposes I was able to run a full scan and then load a recovery point into it to which my computer responded. So far this virus seems to be gone. Should it return I will update my experience.
I just wanted to thank u all. I also did a sytem restore and the Win 7 security is now gone. Any other advice would be greatly appreciated.
Scott's method worked for me! Thank you.
Out of curiosity, does anybody know how the virus gets onto your system in the first place? I want to try and avoid it happening again.
Hi, I have this stupid Win 7 virus too and I also did a system restore yesterday, after which everything looked normal and I was able to access .exe files and the internet. However, the virus re-appeared and attacked my system AGAIN, so beware - a system restore DOES NOT get rid of it.
I followed your advice. It worked, now I have subscribed to Norton antivirus to keep me safe from any of these attacks. Hopefully it will protect my machine in future. THANKS!!
You may need to go to View, then Select Columns to change which columns appear in task manager.
STEP 4: End any of those tasks you find in Task Manager. OH! Make note of the path to the .exe that you killed. You'll go find it and delete it in STEP 5. Also end IExpore.exe (IE) or FF.exe (firefox) or anything that looks browser-related while you're there.
STEP 5: Delete the actual file xxx.exe file from step 4. Start Windows Exporer by clicking Start --> Programs --> accessories, then rt-click on Windows Explorer and select "run as administrator." It won't work if you try to just click on it due to the malware.
STEP 6: find the file and delete it.
At this point the threat is gone, but your system is still screwed up. To fix your computer, there's a single .reg file you need to run from the bleepingcomputer.com URL I posted above. Find the .reg file and open it with "Registry Editor." This will fix your registry and undo all the harm that was done. Remember you can't launch IE normally. You need to find the icon in the start menu and select "run as administrator". At this point all is fixed.
I know all that sounds like a lot, but an expert computer user could do all that in about 2 minutes. It's actually quite simple: 1) Kill the running process, 2) Delete the program from your computer, then 3) fix your computer. Hope that helps!!!
STEP 5:
Background information: This malware alters settings (registry keys) which interferes with the normal way of launching applications. Most of your applications won't work until you do this fix.
Step 1: Don't click on anything and don't panic. It's not really doing as much as you think.
Step 2: Start "Task Manager". It doesn't start the way I normally start it, but try this way: CTRL-ALT-DELETE, then Start Task Manager
STEP 3: In the Task Manager list, find a process that ends in .exe and is usually 3 chars long like wxd.exe. You'll know which one it is if you display the "command line" in the Task Manager list. Look for the command that starts with C:\Users\ on Win7... or it may be C:\Documents and Settings. It WON'T be C:\Program Files or C:\Windows
Sarat has got it right. works in like 5 minutes. Easy peasy.
WHAT LINK?
Help! I opened up an email and the whole win 7 security thing came up. i read everyones previous comments, i didnt download it, but there's still pop ups coming up. and i cant access my internet. how do i get rid of it even though i didnt download it. I tried to download it a few time at first, but my card got declined and now, i dont know how to get rid of all of this crap. im in desperate need of help.
I have experienced the exact same problem as you. I got rid of the virus, but now my programs won't open. Did you find a solution?
WHO is behind this? I want to sue them in small claims court and go after their property. If enough people do, they will regret their theft of our computers.
I also got scamed out of $69.95 for 2 yrs of protection 12-24-11 Called my bank to see if I had any money left in my checking acc. Had my Debit card cancelled & issue another one. Thank goodness the thieves only deducted the $69.95 & didn't touch the other $44,000.00. They will try to get my $69.95 back but no promises. My bank said the name of the person or persons who got my money was: videocaverptro.com I'm not contacting them because I don't want them in my computer again.. My McAfee got rid of this Trojan Virus thank God..
Hi Makr - Could you please provide the .reg file name and where to find that in bleepingcomputer.com. I tried to find the reg file but couldn't find it 🙁 Please help! i'm stuck. I couldn't access anything.
I am trying really hard to follow the directions explaining how to find the file/delete via the task manager, but I am having a hell of a time figuring it out. Any tips that you think may help me through this so I don\'t have to pay someone to clean this up.....
USA laws do not affect people that reside in China or Korea. (for example) so taking someone to court, would be a waste of your time.
The name of the virus is usually a 3 letter name eg: klr.exe
Sarat's method seems to have worked fine here too. Thank you, appreciate the help!
My reply is to SARAT. Good job you did it! I was able to remove this on my Toshiba laptop! You wrote, \"I was able to successfully remove the virus. You can launch the applications through \"Run as Administrator\" mode. So this is what I did:
1. Click on the small white up-arrow in the system tray, which is next to the clock and volume icons. Go to \"customize\" option. Here, you can see one of the entries as \"Win 7 Security\" or something in italics, and another name (process name) right above it.
2. Go to C:\\Windows\\System32 , and right-click on taskmgr.exe and click on \"run as administrator\".
3. Once taskmanager opens up, look for a 3-letter .exe file, and the description column with the process name you got in step 1. In my case, it was pqm.exe with \"Microsoft directPlay…\" process name.
4. Right click on the process and get the file location.
5. Kill the process and go to the file location, and delete it.
6. Re-start the laptop and press F8. You would get a repair option. Use this option to get to System restore utility and restore the system to an earlier date prior to virus attack.
7. You should be good now.
However mine differed from yours in the fact that my 3 letter exe file was msq.exe (it was a scripting file), but after ending the process and finding the file location and deleting it. I was able to restart my computer, pressing F8, and got to the Repair Computer section. Then went to system restore, went back 2 days earlier, restored, restarted, and the win7 security (anti spyware) was removed and did not effect my laptop. Everything is fine and I want to thank you for your easy and effective help in this situation. Have a good New Year, SARAT!
Trying to get this virus off my computer....have got all the way to the step where you find the 3 letter.exe file the 3 letter I have is not showing up in the task manager. When I pull up the customize options it does not have a process name with and the only one showing up in my task manager has been there for almost 2 yrs so it is not that one. I have also tried the esc etc. option it does not pull up anything. any help
i too got scamed for $60
My Dad’s computer was pretty much inoperable. Nothing could be done. After doing a bunch of research, this is what I did to get it off my Dad’s computer.
1) Go to bottom right corner of your screen. Click the arrow and then click on customize. Search for Win 7. It will have a name assigned to it. Every computer will have a different name. The one on my Dad’s said Windows Error Reporting Service.
2) Ctr-Alt-Delete for task manager. Go to process screen. Look for the file. It will be a 3 letter .exe file. (I right clicked on the files and clicked on properties to see if I had the right file called Windows Error Reporting Service. This was listed as wmt.exe, but again every computer will have a different file name) Once I found the file, I ended the process or killed it.
3)The virus is still in the system, but killing the file should enable you to open the Malware/Malbytes program, which I couldn’t do before. (I recognized it by the wmt.exe file name when Malware/Malbytes listed certain files as infected and removed it, so I knew that I had licked it.) Have had no problems since running the computer or any other programs.
Sarat\'s method worked partially. I was able to find, stop, and delete the xxx.exe file that bwas causing the problem. However, there are still some altered files in that my computer says my System Restore is turned off and that no are no previous backup dates to retore to. This is still a remnant of the virus. How do I correct the registry file that makr refers to so all works normally again?
Thanks in advance!
Makr - I'm almost home....just need to correct the registry error that is screwing things up. Please post how to fix the remaining virus residual effects.
Once the virus has been removed you may have problems accessing files. The virus has corrupted your registry and needs to be fixed. The easiest way is to do a system "restore to a previous date" (not the same as a full system restore as in backup & restore). Restoring to a previous date does not affect data files only system files. That should do it!
System Restore was all that I needed to do in order to fix this. Thank you
Thanks Sarat and Kelly, your instructions saved me!
Sarat...Thank YOU!!!!!!!!! You\'re great.....helped my Daughter over the phone with your instructions!!!
What If I don\'t have a system remote point ?
Thank you for your easy to follow instructions. My laptop is now working and virus removed.
I have tried to kill an delete the file but it keeps coming back and my computer keeps turning of any tips
This works?
When I try this. grilled cheese comes out of the disk drive.
Omg!!! I went back to previous date and it doesn\'t show anymore. However, i remember when the Win7 popped up it said Free Ride Games so I went back to customize and it\'s there I deleted it from the regestry and now on window task manager finally a 3 letter word popped out. It is dwm.exe should I delete that bc on description it says it is desktop windows manager....??? Idk what to dooo Soooo help pls!!!
Help!! So this is what I did, first I went back to date to restore pc. Started pc again no win7, then I went to task manager no three letter. After that went to customize and saw Free ride games as notifications which is what I had seen on the win7 program. Then I went to registry to delete this free rider. Once that was done I went to task manager and a 3 letter popped up. It was dwm.exe but on description it says desktop windows manager...should I still erase it??
So how exactly do I remove this virus from my computer?
Don't delete that file Beth. That is a legitimate process. For you to check what is the process of the virus open up task manager then got to application tab, right click on the task of the virus which is the one that has a 2012 at the last part and then choose got to process. It will highlight the process of the virus pop up. If you are using Windows 7 check first the properties of the process for you to check the location of the virus before you end the process tree of it. When you end the process tree it will close the virus pop up and now you can go to the location of the virus usually it is under c:\User\%your user account%\AppData\Local\%3letter.exe%. Delete the icons that has the same date with that 3 letter .exe file then press on shift+delete so it will not go to recycle bin.
Inform me again if what will happen to your computer after removing the virus and I am willing to guide with this case
that helped me too
this thing is makeing me mad i did what i normal do on a computer then one day it just poped up i never download anything so and it ont even let me open up games or documents and stuff like that and every 5 minits the thing wants me to activate it and my brother says i should prob get a windows disc to reformat my laptop i cant afford this stuff and the only usb for me the thing is lost so im stuck here i just dont know what to do
Re: SARAT
thank you so much for your easy instructions. I followed them to the letter and it worked perfectly. Once again thanks you saved my computer and ME! 🙂
there is also a win 7 security that never stops popping up in our computer. I want to get rid of it,but how?
Karen - it's federal law that ur bank pursue the fradulent assholes.
Hi there, just was able to detect this program with the malware download Spyhunter. Going to give it a try. Wish me luck. Will report back if it was able to remove the malware. thanks all.
If you remove those files and entries, it still will display pop-up. the win 7 malware keeps coming back. please help! I am at wits end here trying to remove it manually.
I simply could not navigate any sites. Win 7 security gone now and can navigate. thanks
"error": "Service Unavailable"