XP Antispyware 2012
Posted: June 8, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 12 |
| First Seen: | August 9, 2011 |
|---|---|
| OS(es) Affected: | Windows |
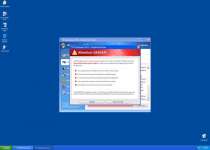
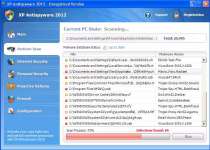 XP Anti-Spyware 2012 is a fake anti-spyware program that's a copy of other threats like Vista Anti-Spyware 2012. Like its kin, XP Anti-Spyware 2012 will block programs and hijack web browsing applications, while creating fake infection warnings instead of implementing real security features. Purchasing XP Anti-Spyware 2012 is strongly discouraged since XP Anti-Spyware 2012 has no positive features, and is designed strictly to steal money and credit card information. Removing XP Anti-Spyware 2012 with the proper use of real anti-malware software will also neutralize all XP Anti-Spyware 2012-related attacks.
XP Anti-Spyware 2012 is a fake anti-spyware program that's a copy of other threats like Vista Anti-Spyware 2012. Like its kin, XP Anti-Spyware 2012 will block programs and hijack web browsing applications, while creating fake infection warnings instead of implementing real security features. Purchasing XP Anti-Spyware 2012 is strongly discouraged since XP Anti-Spyware 2012 has no positive features, and is designed strictly to steal money and credit card information. Removing XP Anti-Spyware 2012 with the proper use of real anti-malware software will also neutralize all XP Anti-Spyware 2012-related attacks.
XP Anti-Spyware 2012 Illusory Security Capabilities
As is the case with most types of rogue security programs, XP Anti-Spyware 2012 doesn't bother to implement any real threat detection functions; XP Anti-Spyware 2012 simply creates fake errors instead that warn you about serious threats, often located in critical programs like your anti-virus scanners and basic Windows applications. XP Anti-Spyware 2012 infection warnings can take the form of false system scans or pop-up alerts that appear semi-randomly.
Some of fake XP Anti-Spyware 2012 alert pop-ups that you might see are:
System warning!
Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer.
System warning!
Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start.
Security Alert!
Your computer is being attacked from a remote machine !
Block Internet access to your computer to prevent system infection.
Critical Warning!
Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended)
XP Anti-Spyware 2012 will continue to pester you with fake warnings like these, while telling you that the only way to stop these threats is to purchase a registered version of XP Anti-Spyware 2012. Since XP Anti-Spyware 2012 neither detects nor removes PC threats like Trojans and worms, you can save your money.
The Real Danger Behind XP Anti-Spyware 2012's Illusion
XP Anti-Spyware 2012 is also able to create genuine problems for your PC, to make it look like different infections are interfering with your computer's operation. Known XP Anti-Spyware 2012 attacks include program-blocking and browser-hijacking.
Program-blocking attacks will often be combined with XP Anti-Spyware 2012's fake errors, to give the appearance of the program crashing because of an infection. The truth, however, is that XP Anti-Spyware 2012 is deliberately blocking the program, and you'll be able to run the application after preventing XP Anti-Spyware 2012 from loading during the Windows startup routine.
XP Anti-Spyware 2012's hijacks will use a variety of methods to redirect you to malicious websites, including changing your homepage settings and altering your results in search engines. More dangerously, XP Anti-Spyware 2012 can also use hijacks to stop you from visiting any website it doesn't want you to see, including security-oriented domains. This can include the use of fake website error pages that usually contain links back to XP Anti-Spyware 2012's own site.
Manual attempts to undo XP Anti-Spyware 2012 browser setting changes or other browser-related attacks will usually fail, since XP Anti-Spyware 2012 will simply remake the changes once you close the application or reboot. Removing XP Anti-Spyware 2012 itself is generally required before you can permanently stop any of the changes that have been made to your browser.
To remove XP Anti-Spyware 2012 with the greatest chance of success, you should first stop XP Anti-Spyware 2012 from launching by booting from a CD or using Safe Mode. Using security software to delete XP Anti-Spyware 2012 is strongly advised, since XP Anti-Spyware 2012 has advanced components that can harm your PC if removed improperly.
Aliases
More aliases (26)
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%USERPROFILE%\Configuraci??n local\Datos de programa\cuw.exe
File name: cuw.exeSize: 344.06 KB (344064 bytes)
MD5: 6c036a1a0b3b25b83fbea52f332c69d5
Detection count: 58
File type: Executable File
Mime Type: unknown/exe
Path: %USERPROFILE%\Configuraci??n local\Datos de programa
Group: Malware file
Last Updated: August 9, 2011
%WINDIR%\system32\config\systemprofile\AppData\Local\sae.exe
File name: sae.exeSize: 335.87 KB (335872 bytes)
MD5: 1a54aff914485e76e7d51bf488e186e5
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %WINDIR%\system32\config\systemprofile\AppData\Local
Group: Malware file
Last Updated: August 9, 2011
%LOCALAPPDATA%\lmk.exe
File name: lmk.exeSize: 532.48 KB (532480 bytes)
MD5: fbcbd2aba5d5aff5c8d1cd93fe304204
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %LOCALAPPDATA%
Group: Malware file
Last Updated: August 9, 2011
dls.exe
File name: dls.exeSize: 2.28 MB (2281472 bytes)
MD5: 0ddd81708871ad2bf1e241f07c774647
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: August 9, 2011
xkj.exe
File name: xkj.exeSize: 348.16 KB (348160 bytes)
MD5: 7c095640bc204e19c44fa40d9a00d58a
Detection count: 4
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: August 9, 2011
%AllUsersProfile%\[RANDOM CHARACTERS]
File name: %AllUsersProfile%\[RANDOM CHARACTERS]Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS]
File name: %AppData%\Local\[RANDOM CHARACTERS]Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS].exe
File name: %AppData%\Local\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Roaming\Microsoft\Windows\Templates\[rRANDOM CHARACTERS]
File name: %AppData%\Roaming\Microsoft\Windows\Templates\[rRANDOM CHARACTERS]Group: Malware file
%Temp%\[RANDOM CHARACTERS]
File name: %Temp%\[RANDOM CHARACTERS]Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Classes\.exe "(Default)" = 'exefile'HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon "(Default)" = '%1" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile "(Default)" = 'Application'HKEY_CURRENT_USER\Software\Classes\exefile "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon "(Default)" = '%1'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "IsolatedCommand" – '"%1" %*'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Mozilla Firefox\firefox.exe"'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Internet Explorer\iexplore.exe"HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Mozilla Firefox\firefox.exe" -safe-mode'HKEY..\..\..\..{RegistryKeys}HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CLASSES_ROOT\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'
Additional Information
| # | Message |
|---|---|
| 1 | Malware Intrusion Sensitive areas of your system were found to be under attack. Spy software attack or virus infection possible. Prevent further damage or your private data will get stolen. Run an anti-spyware scan now. Click here to start |
| 2 | Privacy threat! Spyware intrusion detected. Your system is infected. System integrity is at risk. Private data can be stolen by third parties, including credit card details and passwords. Click here to perform a security repair. |
| 3 | Stealth intrusion! Infection detected in the background. Your computer is now attacked by spyware and rogue software. Eliminate the infection safely, perform a security scan and deletion now. |
| 4 | System Hijack! System security threat was detected. Viruses and/or spyware may be damaging your system now. Prevent infection and data loss or stealing by running a free security scan. |
| 5 | System danger! Your system security is in danger. Privacy threats detected. Spyware, keyloggers or Trojans may be working the background right now. Perform an in-depth scan and removal now, click here |
| 6 | XP Antispyware 2012 Alert Security Hole Detected! A program is trying to exploit Windows security holes! Passwords and sensitive data may be stolen. Do you want to block this attack? |
| 7 | XP Antispyware 2012 Firewall Alert XP Home Security 2012 has blocked a program from accessing the internet Internet Explorer is infected with Trojan-BNK.Win32.Keylogger.gen Private data can be stolen by third parties, including credit card details and passwords. |
I've tried downloading this file. but it does not
when I click run then comes, XP Antispyware 2012 that I should register and then I can downloading.
can you help me please
change the exe to scr extension
u must open my computer
go to folder options
select show extensions
then rename file to .scr instead of .exe
this virus actually won't allow me to open system, add/remove programs, automatic updates on my control panel.
this virus won't allow me to access control panel, add/remove programs, system restore, etc.
I also noticed recently that i was receiving e-mails from people mentioned in e-mails that i sent via hotmail, i.e., it was spam. i'm wondering if this virus is part of that. (one person i had mentioned in e-mail and then who i received e-mail from, she passed away about a decade ago, and had never used e-mail).
at first i could not access most site and could not download your spyhunter. I tired the alt link: https://www.enigmasoftware.com/SpyHunter-Installer.com and that was the trick! you guys rock. SF, you may need to try this link to download the program so you can detect and remove XP Antispyware 2012.
THis saved me a trip to Best Buy geek squad. I was about to just have them fix this XP Antispyware 2012 bug. It would not let me go online to the internet at all. Thanks for being honest.
I was listening to a radio program when this thing pop up. Not even my own anti virus software could load. I couldn't even open up wordpad. I found your site and started in safe mode which does not allow the xp program to load. Then I set the system to restore for a month earlier. The computer now works again and my anti virus software removed any remaining infected files and the boot log scan removed all the infected files as well. Just turn on the computer, press enter when prompted and then choose safe mode.
I have been a little nervous about modifying the registry on my Windows Vista computer to remove entries associated with viruses and spyware. It would be wonderful to locate an automatic program that could remove the entries from your registry on auto-pilot. Any tips?
Use this on home computer and it works great!