Data Recovery
Posted: September 14, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 19,156 |
|---|---|
| Threat Level: | 10/10 |
| Infected PCs: | 340 |
| First Seen: | September 14, 2011 |
|---|---|
| Last Seen: | February 17, 2025 |
| OS(es) Affected: | Windows |
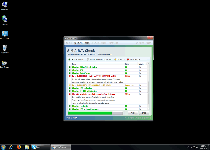
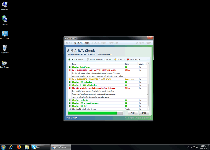
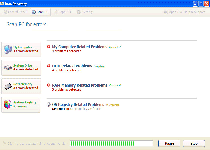 Data Recovery is a clone of System Recovery and other fake defraggers and file-recovery programs from the FakeSysDef family. Although Data Recovery pretends to offer file analysis, defragmentation and information-restoration services, these features don't really exist. Data Recovery's actual purpose as scamware is to filch the money from your bank account by creating a range of system problems on your computer and then demanding that you spend money on Data Recovery's registered version, supposedly to cure these problems. SpywareRemove.com malware researchers haven't seen any indications that Data Recovery is less malevolent than any of Data Recovery's relatives, and you should counteract any Data Recovery infection with anti-malware software that can remove all Data Recovery components via system scans.
Data Recovery is a clone of System Recovery and other fake defraggers and file-recovery programs from the FakeSysDef family. Although Data Recovery pretends to offer file analysis, defragmentation and information-restoration services, these features don't really exist. Data Recovery's actual purpose as scamware is to filch the money from your bank account by creating a range of system problems on your computer and then demanding that you spend money on Data Recovery's registered version, supposedly to cure these problems. SpywareRemove.com malware researchers haven't seen any indications that Data Recovery is less malevolent than any of Data Recovery's relatives, and you should counteract any Data Recovery infection with anti-malware software that can remove all Data Recovery components via system scans.
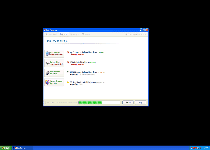
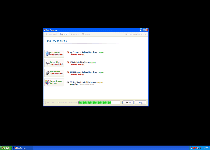
The Fake Scans and Defrags That Data Recovery Uses for Its Own Ill Gain
The majority of Data Recovery infections occur due to contact with fake software update downloads or contact with malicious websites that exploit drive-by-download scripts to install Data Recovery without consent. Although Data Recovery may pretend to scan your PC for errors or fragmented files, what Data Recovery is really doing is creating a simulation of such a scan as an excuse to create fake error messages. Errors may also appear without being prompted by direct usage of Data Recovery, since Data Recovery's only aim is to create an atmosphere of paranoia and desperation, before Data Recovery asks you for your money.
Data Recovery has been updated to have a new interface and name called Smart Data Recovery. Both apps utilize similar actions for tricking PC users out of money.
Typical Data Recovery errors can include, but aren't limited to:
Bad sectors on hard drive or damaged file allocation table – Critical Error
28% of HDD space is unreadable – Critical Error
Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.
A problem detected while reading boot operation system files
System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.
Boot sector of the hard drive disk is damaged – Critical Error – Limited Edition
Windows – No Disk
Exception Processing Message 0×0000013
Read time of hard drive cluster less than 500 ms – Critical Error
Serious system error
The system will reboot in 30 seconds
Windows can not continue operating due to fatal system error.
Windows was forced to restart.
All unsaved data will be lost.
Confirmation
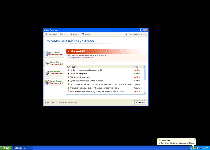
Data Recovery detected an error on your hard drive when trying to access a file
C:\Program Files\Internet Explorer\iexplore.exe
Perform data recovery now?
Disk Error
Can not find file: C:\Program Files\Messenger\msmsgs.exe
File may be deleted or corrupt.
It is strongly recommended to check the disk for errors.
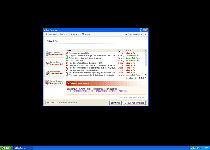
Confirmation
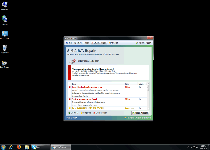
Your hard drive contains a lot of critical errors!
All your data including installed programs, documents, email, etc. are at risk of irreversible corrupt.
The trial version does not have low-level access module needed to fix the errors found.
It is strongly recommended to activate the full version software with necessary modules. Activate full version now?
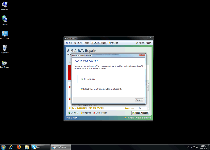
Since all of Data Recovery's supposed features are really just billboards for Data Recovery's fake warning messages, you should never try to use Data Recovery if you find Data Recovery on your computer. SpywareRemove.com malware experts also advise that you immediately cancel any credit card that was used to purchase Data Recovery's registration key, since allowing the card to remain active may put you in danger of other charges of a fraudulent nature in the future.
Recovering Your Computer from Data Recovery's Ravages
Unfortunately, SpywareRemove.com malware experts have also noted that Data Recovery infections can mean more than just being attacked by fake error messages. Some of the most prominent Data Recovery side effects can also include:
- Browser hijackers that block websites, redirect you to dangerous websites or control your web browser's settings. These hijacks may even be accomplished by a Master Boot Record rootkit component, such as a TDSS Rootkit, TDL3 Rootkit, Rootkit.Boot.Mybios.a or TDSS.e!rootkit.
- Vanishing shortcuts and other files. Data Recovery may alter file-viewing settings from your Registry that makes files from Windows Explorer invisible, although you should be able to view and access these files in another program (such as the Command Prompt). In other cases, Data Recovery may actually move files, especially shortcuts and place them in unusual locations, such as your Temp folder.
- Blocked security programs, including anti-virus scanners and some basic utilities like Windows Task Manager.
Other fake security programs that exhibit equivalent attacks to Data Recovery include System Defragmenter, Ultra Defragger, HDD Control, Win HDD, Win Defrag, Disk Doctor, Hard Drive Diagnostic, HDD Diagnostic, HDD Plus, HDD Repair, HDD Rescue, Smart HDD, Defragmenter, HDD Tools, Disk Repair, Windows Optimization Center, Scanner, HDD Low, Hdd Fix and Win Defragmenter. All of these scamware products, as well as Data Recovery, can be combatted with appropriate usage of anti-malware software and traditional anti-malware tactics (such as Safe Mode-based reboots). Since Data Recovery may include rootkits components, SpywareRemove.com malware researchers advise that you don't try to remove Data Recovery by yourself whenever software-based tools are available.



Aliases
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%ALLUSERSPROFILE%\Application Data\aaqcLbHptUym.exe
File name: aaqcLbHptUym.exeSize: 471.04 KB (471040 bytes)
MD5: c9eccf753d782b5427eb0e57c7e651c6
Detection count: 21
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: September 14, 2011
%ALLUSERSPROFILE%\Application Data\fjfYYuH67HH.exe
File name: fjfYYuH67HH.exeSize: 470.01 KB (470016 bytes)
MD5: 3cbccf2b1deb57b125069258c48abf7a
Detection count: 20
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: September 14, 2011
C:\rogues\w32 fakesysdef\6DSS92c31Apgjk.exe
File name: 6DSS92c31Apgjk.exeSize: 356.35 KB (356352 bytes)
MD5: bec326497bad81e5a9300739f62140c3
Detection count: 7
File type: Executable File
Mime Type: unknown/exe
Path: C:\rogues\w32 fakesysdef\6DSS92c31Apgjk.exe
Group: Malware file
Last Updated: May 6, 2024
C:\rogues\w32 fakesysdef\aaqcLAptUym.exe
File name: aaqcLAptUym.exeSize: 440.83 KB (440832 bytes)
MD5: 7e166a87270a0b8754ec946fb7a16626
Detection count: 7
File type: Executable File
Mime Type: unknown/exe
Path: C:\rogues\w32 fakesysdef\aaqcLAptUym.exe
Group: Malware file
Last Updated: May 6, 2024
%ALLUSERSPROFILE%\Application Data\VIKqcLAptUym.exe
File name: VIKqcLAptUym.exeSize: 472.06 KB (472064 bytes)
MD5: 433cf46d22a951113884be6ca7b0a5e7
Detection count: 5
File type: Executable File
Mime Type: unknown/exe
Path: %ALLUSERSPROFILE%\Application Data
Group: Malware file
Last Updated: August 17, 2022
%Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\1
File name: %Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\1Group: Malware file
%Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\2
File name: %Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\2Group: Malware file
%Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\3
File name: %Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\3Group: Malware file
%Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\4
File name: %Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\4Group: Malware file
%Documents and Settings%\[User Name]\Local Settings\Application Data\[RANDOM CHARACTERS]
File name: %Documents and Settings%\[User Name]\Local Settings\Application Data\[RANDOM CHARACTERS]Group: Malware file
%Documents and Settings%\[User Name]\Local Settings\Application Data\[RANDOM CHARACTERS].exe
File name: %Documents and Settings%\[User Name]\Local Settings\Application Data\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%Documents and Settings%\[User Name]\Local Settings\Application Data\~
File name: %Documents and Settings%\[User Name]\Local Settings\Application Data\~Group: Malware file
%Documents and Settings%\[User Name]\Start Menu\\Programs\Data Recovery\
File name: %Documents and Settings%\[User Name]\Start Menu\\Programs\Data Recovery\Group: Malware file
%Documents and Settings%\[User Name]\Start Menu\\Programs\Data Recovery\Data Recovery.lnk
File name: %Documents and Settings%\[User Name]\Start Menu\\Programs\Data Recovery\Data Recovery.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%Documents and Settings%\[User Name]\Start Menu\\Programs\Data Recovery\Uninstall Data Recovery.lnk
File name: %Documents and Settings%\[User Name]\Start Menu\\Programs\Data Recovery\Uninstall Data Recovery.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%Documents and Settings%\[User Name]\Desktop\Data Recovery.lnk
File name: %Documents and Settings%\[User Name]\Desktop\Data Recovery.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\
File name: %Documents and Settings%\[User Name]\Local Settings\Temp\smtmp\Group: Malware file
Registry Modifications
File name without pathData_Recovery.lnkHKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main "Use FormSuggest" = 'Yes'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "CertificateRevocation" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnonBadCertRecving" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop "NoChangingWallPaper" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes" = '/{hq:/s`s:/ogn:/uyu:/dyd:/c`u:/bnl:/ble:/sdf:/lrh:/iul:/iulm:/fhg:/clq:/kqf:/`wh:/lqf:/lqdf:/lnw:/lq2:/l2t:/v`w:/rbs:'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer "NoDesktop" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = '1'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS].exe"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[RANDOM CHARACTERS]"HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download "CheckExeSignatures" = 'no'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "Hidden" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced "ShowSuperHidden" = '0'HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedMRU "MRUList"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "DisableTaskMgr" = '1'
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.