Windows Pro Safety
Posted: May 20, 2012
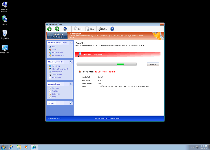
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 2/10 |
|---|---|
| Infected PCs: | 59 |
| First Seen: | May 20, 2012 |
|---|---|
| OS(es) Affected: | Windows |
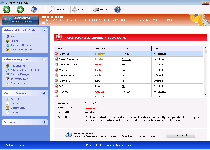 Windows Pro Safety, while Windows Pro Safety acts like an individual anti-spyware scanner, in reality, is a clone of other recent variants of Win32/FakeVimes-based scamware. Although alerts from Windows Pro Safety will imply that your PC is suffering through such grave misfortunes as unauthorized Windows Registry changes, attempts to steal identity-related information or keylogging attacks from unrelated PC threats, Windows Pro Safety isn't able to detect any type of malicious software or attack against your computer. Since, in-between dodging Windows Pro Safety's fake alerts, you'll also be forced to sit through blocked security features and browser redirects, SpywareRemove.com malware analysts suggest removing Windows Pro Safety once you have access to any trustworthy anti-malware product. Regardless of all else, however, you should never purchase Windows Pro Safety, which doesn't have any beneficial security features and can't protect your computer regardless of how much money you spend on Windows Pro Safety.
Windows Pro Safety, while Windows Pro Safety acts like an individual anti-spyware scanner, in reality, is a clone of other recent variants of Win32/FakeVimes-based scamware. Although alerts from Windows Pro Safety will imply that your PC is suffering through such grave misfortunes as unauthorized Windows Registry changes, attempts to steal identity-related information or keylogging attacks from unrelated PC threats, Windows Pro Safety isn't able to detect any type of malicious software or attack against your computer. Since, in-between dodging Windows Pro Safety's fake alerts, you'll also be forced to sit through blocked security features and browser redirects, SpywareRemove.com malware analysts suggest removing Windows Pro Safety once you have access to any trustworthy anti-malware product. Regardless of all else, however, you should never purchase Windows Pro Safety, which doesn't have any beneficial security features and can't protect your computer regardless of how much money you spend on Windows Pro Safety.
Windows Pro Safety: a Professional at Online Thievery
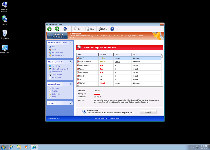
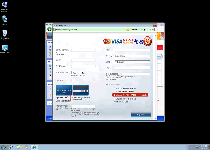
Unlike actual anti-spyware programs, Windows Pro Safety copies the appearance but not the functionality of PC security. While Windows Pro Safety is capable of spitting out a vast assortment of warning messages and Trojan notifications, all of Windows Pro Safety's warnings are false and should be ignored as valueless with respect to detecting PC threats. Similarly, Windows Pro Safety's scanner features are just as poorly functional, and many of its features are only excuses to redirect you to a purchase form for its registration key. SpywareRemove.com malware researchers don't recommend that you give in to Windows Pro Safety's offer, since Windows Pro Safety can endanger your financial credentials and is definitely a pointless waste of money.
In spite of the above caveat, you may find registering Windows Pro Safety for free with the code '0W000-000B0-00T00-E0020' to be helpful. This code also functions for many other members of the FakeVimes group of rogue anti-spyware programs, such as Privacy Guard Pro, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus, Smart Security and PrivacyGuard Pro 2.0. Other safety measures that can be used to disable Windows Pro Safety's attacks before its deletion include booting Windows from a remote source (such as a removable hard drive) or booting into Safe Mode.
Why You Should Hurry to Get Safe without Windows Pro Safety
Windows Pro Safety, like every other member of its family, is also capable of blocking several PC security applications. Common victims of Windows Pro Safety's blocking attacks include Windows tools like the Registry Editor and Task Manager, as well as popular brands of anti-spyware software. However, SpywareRemove.com malware researchers haven't seen any indications that these attacks cause permanent damage to the programs in question, and disabling Windows Pro Safety should allow you to access any software that Windows Pro Safety has been preventing you from using.
Other significant attacks by Windows Pro Safety include disabling the UAC and redirecting your web browser to promote malicious websites, such as fake search engines. Since prolonged contact with these attacks risks further contamination of your PC, SpywareRemove.com malware researchers suggest removing Windows Pro Safety the very moment you can access a good anti-malware product of your preference.



Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AppData%\NPSWF32.dll
File name: %AppData%\NPSWF32.dllFile type: Dynamic link library
Mime Type: unknown/dll
Group: Malware file
%AppData%\Protector-[RANDOM 3 CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM 3 CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Protector-[RANDOM 4 CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM 4 CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%CommonStartMenu%\Programs\Windows Pro Safety.lnk
File name: %CommonStartMenu%\Programs\Windows Pro Safety.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%Desktop%\Windows Pro Safety.lnk
File name: %Desktop%\Windows Pro Safety.lnkFile type: Shortcut
Mime Type: unknown/lnk
Group: Malware file
%AppData%\result.db
File name: %AppData%\result.dbMime Type: unknown/db
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings "WarnOnHTTPSToHTTPRedirect" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegedit" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableRegistryTools" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System "DisableTaskMgr" = 0HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "net" = "2012-5-20_4"HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings "UID" = "rohjjdbsbt"HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorAdmin" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "ConsentPromptBehaviorUser" = 0HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system "EnableLUA" = 0HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\ASProtectHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\portmonitor.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mrt.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\belt.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\vpc32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wnt.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\fsgk32.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sms.exeHKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\..{RunKeys}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Inspector"
Additional Information
| # | Message |
|---|---|
| 1 | Error
Attempt to modify Registry key entries detected. Registry entry analysis recommended. |
| 2 | Warning
Firewall has blocked a program from accessing the Internet C:\program files\internet explorer\iexplore.exe is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server. |
i can't afford to pay the fee for one year to get the service. I am a senior on SS getting under $700 a month. that is why my system has lost the security i should have. Sorry but please unscribe me since I can't do anything except see what is affected. Thank you. Please stop the pop-ups that are a real pain in the a==. Again, Thank You.
How can I purchase from infected computer with getting my credit card hacked.
How do I get this program uninstalled. I don't want it on any of my computers. Tell me how to get it off.
Judy how did you get this dumb program off your computer?