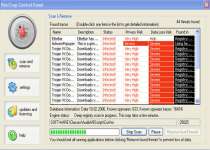
Ilona Trojan
Ilona trojan is a dangerous spyware and a potent threat for those users, who have no good defence on their PCs. This spyware usually performs many actions on the infected machine; some of these actions may annoy the user, others are really destructive and make the computer work in unstable way. It's always a wise decision to remove Ilona Trojan from the infected machine as soon as possible.
The following files were created in the system: