CryptoWall Ransomware Updated to Version 3.0 With Destructive Features
It is almost a sacrilegious thing for hackers to stand still with the development and improvements of popular malware threats they have unleashed on the internet. You can think of hackers to be a perpetual movement of malware improvements. To reiterate that notion, hackers have unleashed a new and improved version of the famous CryptoWall ransomware threat, a program known for encrypting files on an infected computer and then asking that a hefty fee be paid to decrypt those same files.
CryptoWall has made a name for itself as a sophisticated ransomware application that uses strong cryptographic algorithms. Computer users who encounter CryptoWall on their system have reported instances where the threat asks them to pay a fee of $500 in bitcoins so they may allegedly receive a decryption key to recover their encrypted files, as shown in Figure 1 below.
Figure 1. - What the latest CryptoWall 3.0 Ransomware message looks like
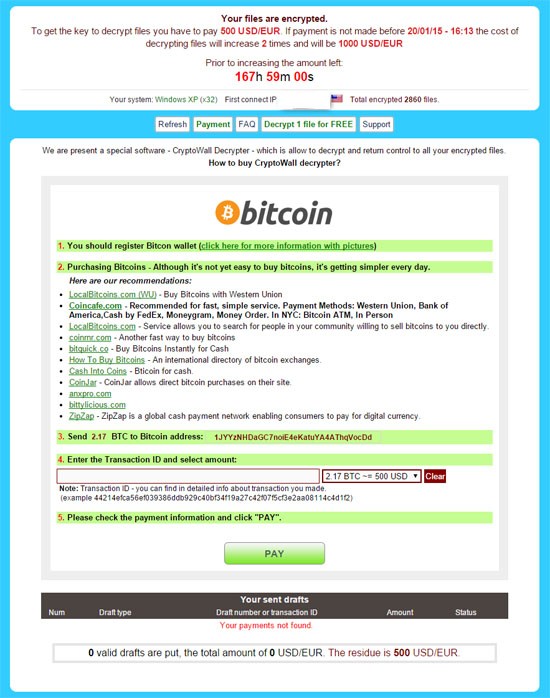
In the latest efforts for attackers to capitalize more on CryptoWall's money extortion scheme, the ransomware has been updated to CryptoWall 3.0, a version that now uses localization and passes traffic to a site where users can pay for their decryption key. The two anonymity networks discovered to aid in this effort are Tor and I2P (the Invisible Internet Project), which have several malicious domains associated with them. These hidden networks evidently now pass web traffic and end up putting an affected system at additional risk of malware infections or exploitation of stored data.
Other malware, that utilize the I2P network, were ones found to be banking Trojans and other malicious apps that communicate with a command-and-control server. You can almost think of this CryptoWall 3.0 update to be a mild botnet in a sense where it is steadily communicating with another entity so it may be custom tailored to the language that the computer user speaks. For instance, the ransom note displayed by CryptoWall 3.0 may be in French if it lands on an infected computer in France or a French-speaking country.
The distribution of CryptoWall 3.0 is sent through drive-by download attacks that exploit vulnerabilities, such as those found in outdated software or web browser application plugins. Moreover, Crowti Ransomware is another encryption-type of threat that researchers at Microsoft have associated with CryptoWall. They utilize a similar distribution channel and their messages are eerily similar. The methods for distribution were also used by its predecessors, which is no big surprise here. What is a surprise, is that after a full two months of inactivity, CryptoWall 3.0 comes out of nowhere catching many off guard. Some researchers thought the threat was gone or at the end of its life span. This goes to show, malware and aggressive ransomware threats have no expiration date no matter how "dead" the threat may seem at the moment. It is best to always act by taking proactive steps to safeguard your computer.
Leave a Reply
Please note that we are not able to assist with billing and support issues regarding SpyHunter or other products. If you're having issues with SpyHunter, please get in touch with SpyHunter customer support through your SpyHunter . If you have SpyHunter billing questions, we recommend you check the Billing FAQ. For general suggestions or feedback, contact us.