Windows Custom Management
Posted: June 26, 2012
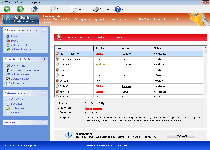
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 6,909 |
|---|---|
| Threat Level: | 1/10 |
| Infected PCs: | 1,450 |
| First Seen: | June 26, 2012 |
|---|---|
| Last Seen: | October 14, 2023 |
| OS(es) Affected: | Windows |
 Although Windows Custom Management might look like a cornucopia of PC security features, Windows Custom Management has been verified as a clone of recent variants of FakeVimes, a classification of rogue anti-malware software that's also noted for causing browser redirects and attacking overall system security. The most noticeable symptoms of a Windows Custom Management infection include inaccurate pop-up advisories about attacks against your computer and system scans that always detect PC threats that fail to show up with reputable anti-malware scanners. Because SpywareRemove.com malware researchers have found that Windows Custom Management's system changes can make your PC vulnerable to other attacks from both related and unrelated PC threats, they suggest deleting Windows Custom Management with a legitimate anti-malware application posthaste.
Although Windows Custom Management might look like a cornucopia of PC security features, Windows Custom Management has been verified as a clone of recent variants of FakeVimes, a classification of rogue anti-malware software that's also noted for causing browser redirects and attacking overall system security. The most noticeable symptoms of a Windows Custom Management infection include inaccurate pop-up advisories about attacks against your computer and system scans that always detect PC threats that fail to show up with reputable anti-malware scanners. Because SpywareRemove.com malware researchers have found that Windows Custom Management's system changes can make your PC vulnerable to other attacks from both related and unrelated PC threats, they suggest deleting Windows Custom Management with a legitimate anti-malware application posthaste.
Examples of Windows Custom Management's Shoddy Computer Management at Work
Windows Custom Management may try to act like an anti-malware product upon initial inspection, but a careful look at its threat alerts and scan results will show that Windows Custom Management doesn't have any ability to detect malicious software or other forms of PC threats. Because Windows Custom Management's security features aren't designed to hold even the slightest bit of accuracy, SpywareRemove.com malware experts strongly discourage following their advice, since this may cause you to delete harmless files or damage programs that Windows Custom Management is blocking for its own purposes.
The ultimate reason for this security information is for Windows Custom Management to make it look as though you need to spend money on purchasing Windows Custom Management to solve your computer problems. To achieve this, Windows Custom Management may also leverage other attacks while simultaneously trying to make it look as though unrelated PC threats are responsible, such as:
- Search engine redirects to malicious sites and 'spam' sites that promote irrelevant advertisements as their primary form of content.
- Changed Registry settings to disable various unrelated programs, disable the UAC or disable default protection against downloaded files with invalid signatures.
- Security and anti-malware applications being blocked once their processes are detected in memory. This Windows Custom Management attack is particularly likely for baseline utilities for Windows (such as the Task Manager and Registry Editor).
An Alternative to Spending Your Way Out of Windows Custom Management Problems
Because Windows Custom Management and related PC threats can interfere with security programs that are required to remove Windows Custom Management safely, SpywareRemove.com malware analysts encourage you routinely to use additional security measures when dealing with such FakeVimes-based PC threats. Blocking Windows Custom Management's startup routine can be achieved via Safe Mode reboots or system boots from removable hard drive-based sources, which will allow you to launch anti-malware scans without interference.
Windows Custom Management does alter Windows components during its installation, and, depending on the case, this can extend to sabotaging the Registry entries of other applications. You may need to reinstall some applications while Windows Custom Management is disabled. Similar procedures should also be used for other FakeVimes-based PC threats such as Privacy Guard Pro, PrivacyGuard Pro 2.0, Extra Antivirus, Fast Antivirus 2009, Presto TuneUp, Windows Security Suite, Smart Virus Eliminator, Packed.Generic.245, Volcano Security Suite, Windows Enterprise Suite, Enterprise Suite, Additional Guard, Live PC Care, PC Live Guard, Live Enterprise Suite, Security Antivirus, My Security Wall, CleanUp Antivirus and Smart Security.


How did I get my computer infected with this program??? Is there anything we can do to dismatle this company. Any agency we can report them to????