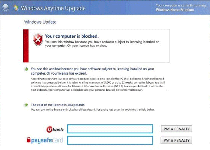
Rootkit.Boot.STT.a
Rootkit.Boot.STT.a is a rootkit that's often associated with the presence of rogue anti-malware products and PC threats that infect removable drives (such as worms). Rootkit.Boot.STT.a is still actively-distributed, although symptoms of Rootkit.Boot.STT.a attacks may not always readily visible. Like other rootkits, Rootkit.Boot.STT.a compromises your operating system's integrity to conceal itself, and SpywareRemove.com malware research team recommends that you use advanced anti-malware...