Interpol Department of Cybercrime Ransomware
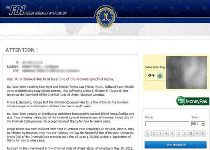
 'Interpol Department of Cybercrime' ransomware is an updated version of ransomware Trojans from the same family as the Metropolitan Police Ukash Virus , ' The Great Britain Police Central e-crime Unit' Ransomware ', the Polícia de Segurança Pública Portuguese Virus , Office Central de Lutte contre la Criminalité Ransomware , the Athens Security Prosecution of Electronic Crime Ransomware and the Cuerpo Nacional de Policia Virus . Despite its minor updates, 'Interpol Department of...
'Interpol Department of Cybercrime' ransomware is an updated version of ransomware Trojans from the same family as the Metropolitan Police Ukash Virus , ' The Great Britain Police Central e-crime Unit' Ransomware ', the Polícia de Segurança Pública Portuguese Virus , Office Central de Lutte contre la Criminalité Ransomware , the Athens Security Prosecution of Electronic Crime Ransomware and the Cuerpo Nacional de Policia Virus . Despite its minor updates, 'Interpol Department of...