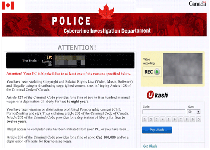
Mariposa
Mariposa (Spanish for 'butterfly'), also known as Rimecud , is a group of multi-component worms that include backdoor Trojan functions (such as enabling DDoS-causing botnets), as well as optional spyware components. Although Mariposa's servers were dismantled by legal authorities, Mariposa managed to achieve a name for itself by infecting anywhere from eight to twelve million PCs before Mariposa was shut down. Mariposa is once again in the eyes of the news media due to the ongoing trial of...