CTB-Locker (Critoni) Ransomware
Posted: July 21, 2014
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 14,807 |
|---|---|
| Threat Level: | 10/10 |
| Infected PCs: | 44 |
| First Seen: | July 21, 2014 |
|---|---|
| Last Seen: | September 14, 2023 |
| OS(es) Affected: | Windows |
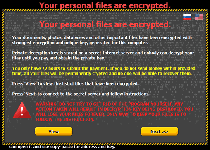 The Critoni Ransomware is a file encryption Trojan that rearranges the data of your PC's files to block access to documents, pictures and other digital content. The Critoni Ransomware's overall goal is to acquire revenue through ransoming the restoration of these files at a high price, although malware experts would recommend restoring your data from a backup, instead. Because the Critoni Ransomware is a 2014-era threat that still is in active distribution to its clientele, you should take all appropriate anti-malware security steps for blocking its varied installation methods and if called for, removing the Critoni Ransomware from your computer.
The Critoni Ransomware is a file encryption Trojan that rearranges the data of your PC's files to block access to documents, pictures and other digital content. The Critoni Ransomware's overall goal is to acquire revenue through ransoming the restoration of these files at a high price, although malware experts would recommend restoring your data from a backup, instead. Because the Critoni Ransomware is a 2014-era threat that still is in active distribution to its clientele, you should take all appropriate anti-malware security steps for blocking its varied installation methods and if called for, removing the Critoni Ransomware from your computer.
The Ransomware that Uses Tor Both Coming and Going
The Critoni Ransomware's developers have offered the Critoni Ransomware as a supposedly new version of Cryptolocker since June of 2014, with other persons allowed to rent its services at a cost of 3,000 USD. While the Critoni Ransomware attacks often focus on Russia, its use by diverse third parties has begun to seep over into its choice of victims, putting other nations at risk from this PC threat. Although the Critoni Ransomware frequently uses exploits included in webpage-hosted threats like the Angler Exploit Kit, malware experts can confirm that the Critoni Ransomware also uses other methods to install itself, such as spam and disguised social networking links.
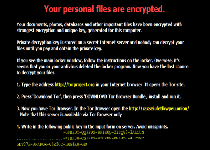
Distribution methods aside, the Critoni Ransomware's primary functions are the same as other file-encrypting Trojans: the Critoni Ransomware uses encryption attacks to make arbitrarily-selected files unreadable. Various methods are used (including .TXT files left in appropriate directories) for demanding a Bitcoin-based ransom fee to reverse these attacks. The Critoni Ransomware claims to use an elliptic curve-based encryption method that can't be reversed by third-party tools, and while malware experts have yet to confirm this, they do note that remote backups are the most uncomplicated methods to defend your information from encryption attacks.
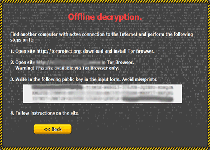
From a programming standpoint, the Critoni Ransomware is well-designed both for requiring the use of the Tor Browser (an anonymity-enabling Web browser) to process payments, and for using that same program to communicate with its C&C servers. The latter is a feature that malware researchers more often find in banking Trojans, and indicates a level of long-term commitment to anonymity and personal safety on the part of the Critoni Ransomware's developers.
Bailing Yourself out of a Ransom with not a Bitcoin Lost
As usual, the Critoni Ransomware's ransom messages include countdown timers that warn you to pay your ransom before retrieving your files becomes impossible. Nonetheless, malware experts find no negative consequences to ignoring this timer and, hopefully, removing the Critoni Ransomware from your computer through proper anti-malware solutions. There is not yet a third-party decryption tool available for reversing the Critoni Ransomware's attacks, but standard file backup strategies should be sufficient for restoring any lost data. Using browser settings that maximize safety, such as disabling automatic website scripts, also may provide a degree of protection from the Critoni Ransomware's known distribution techniques.
The Critoni Ransomware also was verified to be able to modify files on PCs lacking Internet connections, although malware experts have yet to find any worm-based distribution methods that would allow the Critoni Ransomware to compromise such systems without the assistance of additional threats. The full range of OSes vulnerable to the Critoni Ransomware is under investigation.
As infection rates of CTB-Locker increase, it has been noted that the infection is relentless when it comes to destroying files through encryption. The only way for computer users to restore their files is to utilize either a backup copy of their hard drive or restore the files from a previous restore point saved on their system or external hard drive.
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%MyDocuments%\AllFilesAreLocked [USER ID].bmp
File name: %MyDocuments%\AllFilesAreLocked [USER ID].bmpMime Type: unknown/bmp
Group: Malware file
%MyDocuments%\DecryptAllFiles [USER ID].txt
File name: %MyDocuments%\DecryptAllFiles [USER ID].txtMime Type: unknown/txt
Group: Malware file
%MyDocuments%\[RANDOM].html
File name: %MyDocuments%\[RANDOM].htmlMime Type: unknown/html
Group: Malware file
%Temp%\[RANDOM].exe
File name: %Temp%\[RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%WinDir%\Tasks\[RANDOM].job
File name: %WinDir%\Tasks\[RANDOM].jobMime Type: unknown/job
Group: Malware file
C:\Documents and Settings\<username>\Application Data\[RANDOM].exe
File name: C:\Documents and Settings\<username>\Application Data\[RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
C:\Documents and Settings\<username>\Local Application Data\[RANDOM].exe
File name: C:\Documents and Settings\<username>\Local Application Data\[RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
C:\Users\<username>\AppData\Local\[RANDOM].exe
File name: C:\Users\<username>\AppData\Local\[RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
C:\[RANDOM]\[RANDOM].exe
File name: C:\[RANDOM]\[RANDOM].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Control Panel\Desktop "Wallpaper" = "%MyDocuments%\AllFilesAreLocked [USER ID].bmp"
Hello everybody!
My files also became encrypted due to CTB-Locker. I'm ready to pay some money for my stupidity, but 3 BTC is too much for me just because I'm from Ukraine, we have ongoing war now, economics is falling, etc.
I can pay 100 USD to anyone who can decrypt my files
Hi, has nyone a tool to decrypt the files?
Thanks!
Unfortunally, each decryption key are unique for each computer infected ...
Trying a system restore may help you getting your files .
hi, just found out i have the same above mentioned trojan, is there any way i can get my files back, any progress?i've lost all my pictures, of my decesed parents,friends, important documents, everything!!whoever did this are real bXXXXXs!!
I had this 'Locker' appear when using a Library computer with HD attached via USB for storage. Files on the HD were corrupted, (though ...of course... I had Back-ups of everything), but I did notice Wordpad/Notepad files OPEN at the time of infection were NOT corrupted !?! .... also, while images on the Library PC WERE unviewable at the TINE, several days later the pics ARE working fine again. I did ASK if anything had been done TO the P.C. by Library Staff, (they said NO), though every evening the computers are all Switched Off then back ON again the next day ... Ultimate answer, of course, with External/BU HD's so cheap these days, does seem to be to BACK-UP EVERYTHING important, (at least ONCE) 🙂
will this program really work to get ctb-locker off with out loosing any files? guarantee to work or money back! please reply