Windows Active Defender
Posted: June 14, 2012
Threat Metric
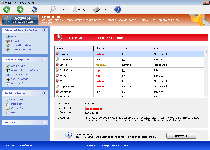
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 19 |
| First Seen: | June 14, 2012 |
|---|---|
| Last Seen: | January 8, 2020 |
| OS(es) Affected: | Windows |
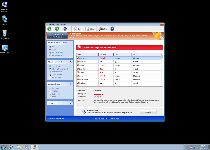
 Windows Active Defender is another entry into the annals of rogue anti-malware software that's classified under the umbrella of the Win32/FakeVimes (or simply FakeVimes) family. While Windows Active Defender doesn't have any true functions intended for the protection of your computer against viruses, rootkits and other PC threats, Windows Active Defender's pop-up alerts and system scans will display inaccurate information to convince you otherwise. Attacks by Windows Active Defender may also include the creation of junk files, browser redirects or blocking legitimate PC security applications. Since Windows Active Defender's real features place your PC in a state of considerable vulnerability, SpywareRemove.com malware experts encourage the use of exhaustive anti-malware scans to find and delete Windows Active Defender and anything else that was included in its installation attack.
Windows Active Defender is another entry into the annals of rogue anti-malware software that's classified under the umbrella of the Win32/FakeVimes (or simply FakeVimes) family. While Windows Active Defender doesn't have any true functions intended for the protection of your computer against viruses, rootkits and other PC threats, Windows Active Defender's pop-up alerts and system scans will display inaccurate information to convince you otherwise. Attacks by Windows Active Defender may also include the creation of junk files, browser redirects or blocking legitimate PC security applications. Since Windows Active Defender's real features place your PC in a state of considerable vulnerability, SpywareRemove.com malware experts encourage the use of exhaustive anti-malware scans to find and delete Windows Active Defender and anything else that was included in its installation attack.
Windows Active Defender: a Vigorous Offense Hiding Behind a Lackluster Defense
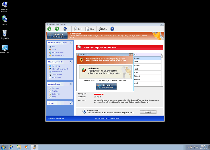
Windows Active Defender uses the same methodology common to all scamware: creating fake reasons to panic as an incentive for spending money on its fraudulent security software. Buying Windows Active Defender's registration key should never be considered a wise idea, even though Windows Active Defender will constantly announce the presence of everything from keyloggers to unauthorized network activity to remote attempts to steal your identity. Because Windows Active Defender's system scans and other security pretenses are all utterly fake, SpywareRemove.com malware researchers note that the best thing that you can do is ignore them wholesale.
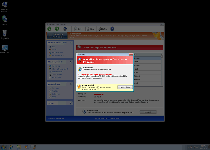
As long as Windows Active Defender is active in memory, Windows Active Defender may also be a source of other attacks that Windows Active Defender will attempt to make look like activities of unrelated PC threats. These can include:
- Browser redirects that promote malicious sites, including spam-based search engines. SpywareRemove.com malware researchers especially advise you to minimize contact with any sites that are promoted by Windows Active Defender's browser attacks.
- Blocked security and anti-malware tools, up to and including basic utilities like your Windows Task Manager.
- The creation of dummy files that Windows Active Defender may use to implicate other types of malware. These files are, in and of themselves, harmless, except insofar as they're symptoms of a Windows Active Defender infection.
- Reduced security settings for various programs, including the Windows OS and your web browser.
The PC Security That Even Windows Active Defender Can't Defend Itself Against
Windows Active Defender should always be disabled and removed as soon as possible, assuming you have access to anti-malware products that can do so with maximum safety. If Windows Active Defender attempts to block software that could remove Windows Active Defender, SpywareRemove.com malware researchers recommend booting into Safe Mode or using other alternatives in OS boot-up techniques to ensure that Windows Active Defender can't launch. Failure to do this prior to a system scan can result in Windows Active Defender or other PC threats surviving even if they're detected.
Similar precautions should be taken against any other member of WinPC Defender, such as Ultimate Defender, SystemDefender, IE Defender, XP Defender, Advanced XP Defender, WinDefender2008, PCTotalDefender, PC Defender 2008, Personal Defender 2009, WinDefender 2009, Perfect Defender 2009, Total Defender, Malware Defender 2009, WinPC Defender, PC Privacy Defender, Smart Defender Pro, Rogue.UltimateDefender, FraudTool.LastDefender.b and Security Defender Pro 2015. Modern FakeVimes variants are particularly likely to resemble Windows Active Defender in both their appearances and naming schemes – the latter of which will usually (but not always) follow a pattern such as 'Windows [adjective] [noun].'
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:C:\rogueware samples\WintionalityChecker samples\Older Fakevimes\Windows Active Defender.exe
File name: Windows Active Defender.exeSize: 1.93 MB (1939456 bytes)
MD5: 6cbcda5f9b1954a1f35fd4bbdacaa9a4
Detection count: 9
File type: Executable File
Mime Type: unknown/exe
Path: C:\rogueware samples\WintionalityChecker samples\Older Fakevimes\Windows Active Defender.exe
Group: Malware file
Last Updated: May 6, 2024
%AppData%\Protector-[RANDOM CHARACTERS].exe
File name: %AppData%\Protector-[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
Registry Modifications
HKEY..\..\{Value}HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Inspector = %AppData%\Protector-[RANDOM CHARACTERS].exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\a.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\About.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ackwin32.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ad-Aware.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alogserv.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\aAvgApi.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\adaware.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentsvr.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\advxdwin.exe\"Debugger" = "svchost.exe"HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentw.exe\Debugger = svchost.exeHKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV\"Debugger" = "svchost.exe"
Okay, got the SpyHunter installed and somehow my internet will not access due to Windows Active Defender. HOw do I restore internet? SpyHunter has detected this Windows Active Defender and I will proceed to remove it now.
keeps kicking me out of browsers. cannot go into internet to download anything. using neighbors laptop. what can i do?
@ Angie, Go into your device manager, VIA control panel/Performance and maintenance/Computer Management/Device manager. Now find your network adapters Double click on the selections and trubleshoot and or udate drivers if this does not work roll back your drivers.
You have to go into safe mode so Windows Active Defender won't block anything.