Win 7 AntiVirus 2012
Posted: June 8, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Ranking: | 14,621 |
|---|---|
| Threat Level: | 8/10 |
| Infected PCs: | 719 |
| First Seen: | December 5, 2011 |
|---|---|
| Last Seen: | September 5, 2023 |
| OS(es) Affected: | Windows |
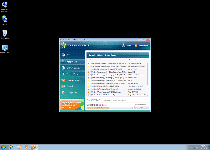
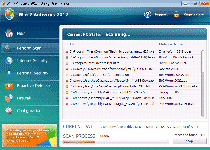 Win 7 Antivirus 2012 is a rogue antivirus program that uses fake alerts and system scans with dishonest results to make you think that purchasing Win 7 Antivirus 2012 is the only way to save your PC from an army of infections. Even the registered version of Win 7 Antivirus 2012 can't remove or find real threats, however, and keeping Win 7 Antivirus 2012 on your PC will actually result in browser hijacks and problems running other programs. You should remove Win 7 Antivirus 2012 as soon as it's possible by using a real anti-virus scanner.
Win 7 Antivirus 2012 is a rogue antivirus program that uses fake alerts and system scans with dishonest results to make you think that purchasing Win 7 Antivirus 2012 is the only way to save your PC from an army of infections. Even the registered version of Win 7 Antivirus 2012 can't remove or find real threats, however, and keeping Win 7 Antivirus 2012 on your PC will actually result in browser hijacks and problems running other programs. You should remove Win 7 Antivirus 2012 as soon as it's possible by using a real anti-virus scanner.
The Fake Security Features That Win 7 Antivirus 2012 Wants You to Know About
Win 7 Antivirus 2012, like many other rogue security programs, has two sides – a directly visible side where it pretends to be an anti-virus and security product, and a hidden side where Win 7 Antivirus 2012 attacks your PC while trying to hide its malicious nature. Win 7 Antivirus 2012 is in the same subcategory as many other rogue security programs that belongs to the FakeRean family that fake anti-virus features; some other examples of threats that are nearly identical to Win 7 Antivirus 2012 are Antivirus 2008 Pro, Antivirus XP 2008, Windows Antivirus 2008, Vista Antivirus 2008, PC Clean Pro, Antivirus Pro 2009, Rogue.Vista Antivirus 2008, AntiSpy Safeguard, ThinkPoint, Spyware Protection 2010, Internet Antivirus 2011, Palladium Pro, XP Anti-Virus 2011, CleanThis, XP Security 2012, XP Home Security 2012 and AntiVirus PRO 2015.
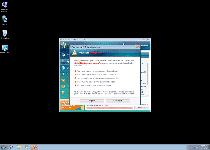
Like all of the above rogue security programs, Win 7 Antivirus 2012 looks like a normal anti-virus application and will even scan your computer. Instead of finding real threats, however, Win 7 Antivirus 2012 creates fake threat alerts to push you into purchasing an updated version of Win 7 Antivirus 2012 that can 'remove' these threats. Win 7 Antivirus 2012 will also reinforce the impression of multiple infections on your computer by using fake warning notifications.
These pop-ups are never the result of Win 7 Antivirus 2012 scanning your computer for threats, and notifying you about them once they've been detected. Win 7 Antivirus 2012 can't find or delete Trojans and other PC threats even in its registered version, and, therefore, you should never pay money for Win 7 Antivirus 2012.
The Working Features That Win 7 Antivirus 2012 Doesn't Want You to See
Despite brazenly displaying anti-virus features that don't actually work, Win 7 Antivirus 2012 has functional features that it tries to misdirect you away from:
- Win 7 Antivirus 2012 can hijack popular web browser applications. The primary symptom of a hijack is when you're redirected to a strange and inevitably malicious website for no reason, although hijacks can also conceal themselves in changed search results, altered homepage settings, and even fake website error pages.
- Win 7 Antivirus 2012 may also shut down different programs to stop you from using security-related software to remove Win 7 Antivirus 2012 from your PC. In a fit of surprising subtlety, Win 7 Antivirus 2012 can even use fake errors such as the examples listed earlier, to make it look like there's a real problem with the program that it's shutting down.
Like the majority of threats, Win 7 Antivirus 2012 will attack your Registry to enable its own automatic startup every time Windows loads. Preventing the above attacks without stopping Win 7 Antivirus 2012 from loading is difficult, and it's suggested that you use Safe Mode or another alternate boot method to disable Win 7 Antivirus 2012's startup. Afterwards, removing a disabled Win 7 Antivirus 2012 by applying a good anti-malware program is a fairly straightforward process.
template:removal]
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%AllUsersProfile%\[RANDOM CHARACTERS]
File name: %AllUsersProfile%\[RANDOM CHARACTERS]Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS]
File name: %AppData%\Local\[RANDOM CHARACTERS]Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS].exe
File name: %AppData%\Local\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS]
File name: %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS]Group: Malware file
%Temp%\[RANDOM CHARACTERS]
File name: %Temp%\[RANDOM CHARACTERS]Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Classes\.exe "(Default)" = 'exefile'HKEY_CURRENT_USER\Software\Classes\.exe "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon "(Default)" = '%1' = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile "(Default)" = 'Application'HKEY_CURRENT_USER\Software\Classes\exefile "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon "(Default)" = '%1'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "IsolatedCommand" – '"%1" %*'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Mozilla Firefox\firefox.exe"'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Mozilla Firefox\firefox.exe" -safe-mode'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Internet Explorer\iexplore.exe"'HKEY..\..\..\..{RegistryKeys}HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CLASSES_ROOT\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'
Additional Information
| # | Message |
|---|---|
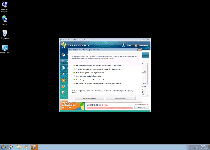
| 1 | Attention: DANGER! ALERT! System scan for spyware, adware, trojans and viruses is complete. Win 7 Antivirus 2012 detected 35 critical system objects. |
| 2 | System danger! Your system is in danger. Privacy threats detected. Spyware, keyloggers or Trojans may be working in the |
| 3 | Win 7 Antivirus 2012 ALERT Internet Explorer alert. Visiting this site may pose a security threat to your system. |
I think it is shameful that someone can "contrive" a program, like this, just to make money off of people, under the auspices of scaring them into believing that they have viruses. THERE SHOULD BE A BE A LAW AGAINST THIS TYPE OF ACTION AND USE OF THE INTERNET!!!!
whats the way to remove win 7 home security 2012 from my computer without downloading anything because its blocking my downloads
what is the other way you can get rid of win 7 home security 2012 because it is blocking my downloads and what do you do when it says security hole detected do you want block this attack do i clink yes or no please answer
I a, working on someones Mac right now as that Win 7 Anti Virus 2012 Program will NOT let me USE the Internet. It BLOCKS me. I called my server Teksavvy and all is well as far as me receiving my Internet connection.
I have NO clue as to what to do as I can NOT even get into my Internet through Internet Explorer or Safari. I am on a Disability Pension. live alone and yada yada yada. Yes it is a problem but I have always seemed to manage.
But this one has stymied me completely. I shut my computer off and I even unplugged it.
That\\\\\\\'s how paranoid I am about this.
Any help would greatly be appreciated. And ADMITTEDLY I am perhaps just a \\\\\\\'vit; past being a \\\\\\\'novice\\\\\\\' in computers.
May Thanks if you can help.
Gary Spears Hamilton Ontario
Canada
You have to run your computer in safe mode with networking THEN download the spyhunter program. Otherwise the Win 7 antivirus will not let you continue.
so useful tnx very much
Mhm. My sister got this. I knew it was malicious the first milisecond I saw it.
She said that she was just browsing on facebook and stuff, then it popped up saying verify or something. That\'s when she got the series of constant threat messages.
I\'ve dealt with this before on my own machine. It wasn\'t this one but it was still a rogue anti-virus. I basically got annoyed about it and told her she was a fool for even verifying ANYTHING like this on the Internet.
I managed to delete the kvk.exe\'s (The Win 7 2012 Antivirus apps) and keep Windows Task Manager open on the side to tell me when they did re-open again. I had to system restore so it got rid of it completely.
I\'d seriously recommend everyone to make sure their PC has system restore points.
@Linda,
There is a law... like you if you steal..we will get you for fraud etc... but it does not help normal folks who has no idea about this kind of vicious attack.
thanks for the program. too bad win 7 won\'t let you download anything. I ran my own anti-virus [I was suprised that was still working] and got enough of it removed to download the program. I have to open the program after restarting my computer but the issue is that if win 7 antivirus boots up before you open the program the program becomes blocked. I open it and every time I open it the program says I need new updates. If I\'m lucky I can get the updates downloaded then it tells me to restart my computer to initilize it. so I restart the computetr and race to open the program and start the scan only for it to tell me I have to download more updates [when I previously downloaded the updates not even 5minutes earlier] I can\'t tell if this program is useless or just the attempts
omg i have it!! I had to log into another desktop acct to even get my malwarebytes to run, so when i go to do a restart windows starts installing updates....now i cannot even access my acct, just a black screen with an error message that goes away so fast i cannot even see it!
Andrea, thanks so much for the tip...after three hours I came upon your comment and was able to run everything in safe mode and removed it......
One easy way to get around it temporarily is open every program u want to use by right clicking then saying "Run as Administrator" this bypasses every interruption to that program opening. Using that, i am surfing the internet for ways to fix this annoying problem.
iv read all the comments and have not got my answers to fix my problem
There are many blogs that have instructions on how to get rid of this virus, but none that tell you how to avoid getting it in the first place. In my case, I kept getting the virus back from torrent download sites.
As the removal instructions indicate, the infection changes a registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet
The infection also hides the fake antivirus program on your hard drive, somewhere in your user profile directory. The fake antivirus program is given a random name, like nwa, so you can’t find it by looking for something specific.
The infection changes the key so that when you try to start your browser, the fake antivirus program starts up instead. Yes, you can get rid of it (that is well documented), but short of never visiting a site (such as a torrent site) where you can get the infection again, you need to protect the key from getting changed again. Windows 7 is supposed to prevent unauthorized changes to the system, using a feature called User Account Control. I set User Account Control to its highest setting, but it did not prevent the key changes. Spybot Search and Destroy also has a feature to do something similar, but it likewise failed to prevent the key change.
However, if you are able to use regedit, and understand file and folder security permissions, you can beat the virus from returning. I’ll provide an overview of what I did, but will leave the EXACT actions to you.
1. Using regedit, navigate to the key, and right click to bring up the context menu. Click Permission to access ACL (access control list) settings. If you know how to work with the ACL for files and folders, the method is the same.
2. The ACL includes the groups and/or users (such as Administrators, Creator Owner, System, etc) and their permissions for the key. For each user, for each permission (Read, Write, Full Control, etc) you can specify “Allow” or “Deny.” Add the user Everyone to the ACL.
3. Set “Deny” for the “Full Control” permission for the Everyone user. Deny overrides Allow. Note that “Everyone” permissions apply to EVERYONE, even Administrators. So if Everyone has Full Control denied, it will override Administrators having Full Control allowed. Now, the key values (data) can’t be changed, not even the System can change the key data. You can no longer even SEE the key values (Read permission is denied). You can’t change the permission back, because Deny also applies to changing permissions, not just to changing data values. It’s (almost) a one-way street.
4. If you ever need to turn off Deny, you can, with administrative authority, take ownership of the key. As the key owner, you can remove the Deny permission.
I intentionally did not provide step-by-step directions, because if you are not already intimately familiar with Windows file permissions, you should not be messing with the registry this way. This post is intended to bring attention of this solution only to those experienced with ACLs.
I assume that if you have the right antivirus software installed, it could prevent the key change instead of using the procedure described here. But I don’t have anything other than Microsoft Security Essentials for malware protection, and it did not do the job.
I could not load any program at all including regedit it disables the .exe.
I had to use windows repair and ran a scan after it went to a back up
If it wasn\'t for SRware Iron\'s security I wouldn\'t be able to get on the internet, I ended up using IObit\'s Malware Fighter to remove the registry mods and find out it was associated with Whitesmoke Translator, a program I don\'t remember downloading in the first place.
This virus is actually running a script. fst.exe is the process that is behind this script. Kill it and you can regain control over your pc. It will try to relaunch itself. It also stops and screws up the Windows Defender service then deploys a fake windows defender process. Once you disable the fst.exe you should be able to download the tool above.
all i want to know is where is the guy or company making this crap, I say lets hunt them down and kill them and blow up their stuff so they can't screw over any one else...KILL THEM ALL!!!
Andrea, please explain how run my computer in safe mode with networking. I appriciate.
I have had a panicky few hours findingout my PC has been infected with this virus! I've got a laptop that I've been able to investigating the net with - thankfully. I hope that I've now got rid of it, and the way that I've done this is by starting the PC in safe mode and then doing a system restore to a few days ago. Fingers crossed so far.
I agree. lets.
if im not mistaken there are laws against cyber terrorism
I can't seem to get out of safe mode. I thought I deleted win7 antivirus but I notice it is still there. Please help. I have purchased norton antivirus, but it stalls. So I am missing something
I just got this thing on my computer, I could not open any anti-spyware program or IE. I restored my computer to a previous restore point (last Windows Update) & this wiped it from my computer, so if all else fails;try that. 😉
Wow, this problem has proven to be quite complicated on my computer.
I have finally started windows in safe mode, however I am unable to open task manager. A box pops up saying \"C:\\Windows\\system32\\taskmgr.exe\" and something like \"Unable to find this application\". In fact, I get this response when I try to open ANY program. Also, when I try to open the mozilla as the administrator, it opens, but I can not access the internet. When I try to restore my system to a previous restore point, a box pops up prompting me to choose a program to open my file, and the only program it offers as an option is Internet Explorer....which is obviously not what I need to open my system restore.
This doesn\'t make any sense!
Does anyone have any advice on how to remove this virus if I do not have access to the task manager, system restore, or the internet?
Thank you!
Oh. I don't like AVG. Merely not detecting viruses in many cases. My vote is for the Spyhunter. it found it and removed after register. tanks.