XP Security 2012
Posted: June 8, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 96 |
| First Seen: | August 9, 2011 |
|---|---|
| Last Seen: | November 10, 2020 |
| OS(es) Affected: | Windows |
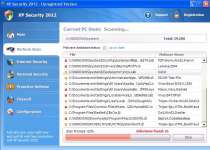 XP Security 2012 is a rogue security program that imitates system scans and threat alerts, but detects nonexistent infections instead of real ones. Like many other threats, XP Security 2012 may block programs to prevent itself from being removed, and can also hijack your web browser to redirect you to harmful websites. Rather than spending money on a security program with no real security features, it's strongly recommended that you uninstall XP Security 2012 with the help of a good anti-malware scanner.
XP Security 2012 is a rogue security program that imitates system scans and threat alerts, but detects nonexistent infections instead of real ones. Like many other threats, XP Security 2012 may block programs to prevent itself from being removed, and can also hijack your web browser to redirect you to harmful websites. Rather than spending money on a security program with no real security features, it's strongly recommended that you uninstall XP Security 2012 with the help of a good anti-malware scanner.
XP Security 2012: A Derivative but Still Deadly Threat to Your PC
XP Security 2012 shares its graphical skin and the majority of its functional code with other rogue security programs in the same family. Some recent examples of rogue security programs that are related to XP Security 2012 include Antivirus 2008 Pro, Windows Antivirus 2008, Vista Antivirus 2008, Antivirus XP 2008, PC Clean Pro, Antivirus Pro 2009, AntiSpy Safeguard, ThinkPoint, Spyware Protection 2010, Internet Antivirus 2011, Palladium Pro, XP Anti-Virus 2011, CleanThis, Rogue.Vista Antivirus 2008, XP Home Security 2012 and AntiVirus PRO 2015. In spite of their different names, you should treat all of these threats as essentially the same malicious program.
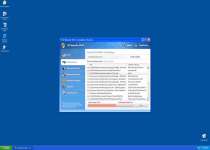
Like the above PC threats, XP Security 2012 also uses imitations of system scans and infection warning pop-ups to mislead you about the state of your PC's health. Regardless of how few infections are on your PC, XP Security 2012 will always announce that it's found many different attackers that can only be deleted if you purchase XP Security 2012. The purchasable version of XP Security 2012 isn't any more able to delete or detect threats to your PC than the 'free' version is, so you should save your money.
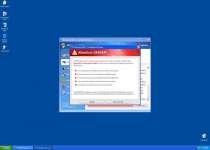
Many of the pop-up warnings that XP Security 2012 can create may look similar the examples listed here:
System warning!
Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer.
System warning!
Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start.
Security Alert!
Your computer is being attacked from a remote machine !
Block Internet access to your computer to prevent system infection.
Critical Warning!
Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended)
You should never take any of the suggestions that these pop-ups offer, since doing so can cause you to delete uninfected files or download additional malicious software besides XP Security 2012. Visiting the XP Security 2012 website, which it will try to direct you towards on a regular basis, can also result in other infections that exploit your browser's security limitations to install themselves.
Where XP Security 2012's Real Functions Come Into Play
XP Security 2012's anti-virus and security features are all fake, but XP Security 2012 does have real features that work perfectly well. Sadly, these functions are all related to attacking your PC or stopping you from removing XP Security 2012.
- During its installation, XP Security 2012 will have startup entries added to your Windows Registry. These entries let XP Security 2012 run by default, unless you use Safe Mode or boot your OS from another source (like a CD) that bypasses the default Registry.
- XP Security 2012 can stop you from using a wide range of programs, although the programs that are most likely to be attacked by XP Security 2012 are security-related and system maintenance applications. Popular anti-virus brands and standard Windows tools like MSConfig and the Registry Editor are all likely targets.
- When it's not stopping you from using your browser entirely, XP Security 2012 may choose to hijack it instead. Hijacks can change settings like your homepage, redirect you to harmful websites or make it impossible for you to visit safe websites. XP Security 2012 may use fake error screens that tell you that a website is unsafe to make you think that your browser is pro-actively protecting you.
Aliases
More aliases (88)
Technical Details
File System Modifications
Tutorials: If you wish to learn how to remove malware components manually, you can read the tutorials on how to find malware, kill unwanted processes, remove malicious DLLs and delete other harmful files. Always be sure to back up your PC before making any changes.
The following files were created in the system:%SystemDrive%\Documents and Settings\Ashlyn\Application Data\Protector-lrqe.exe
File name: Protector-lrqe.exeSize: 2.21 MB (2216960 bytes)
MD5: 32b652fee344c25f4bfed0ca2a472b1f
Detection count: 73
File type: Executable File
Mime Type: unknown/exe
Path: %SystemDrive%\Documents and Settings\Ashlyn\Application Data
Group: Malware file
Last Updated: July 20, 2012
install.exe
File name: install.exeSize: 344.06 KB (344064 bytes)
MD5: a8a1ec0be621d5e5237e5057d428640a
Detection count: 56
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: August 9, 2011
setup.exe
File name: setup.exeSize: 348.16 KB (348160 bytes)
MD5: d91454e0e028db3aad86196f404676af
Detection count: 55
File type: Executable File
Mime Type: unknown/exe
Group: Malware file
Last Updated: August 9, 2011
C:\KDownloader\AddAm\WDvdauthoe.cpl
File name: WDvdauthoe.cplSize: 171.41 KB (171417 bytes)
MD5: ae0c989485969d8b48a65b7c96b5a88a
Detection count: 54
Mime Type: unknown/cpl
Path: C:\KDownloader\AddAm
Group: Malware file
Last Updated: July 19, 2012
%WINDIR%\system32\config\systemprofile\AppData\Local\fjn.exe
File name: fjn.exeSize: 372.22 KB (372224 bytes)
MD5: 5f4ef2db6bcaff93b96025b60ed03fae
Detection count: 30
File type: Executable File
Mime Type: unknown/exe
Path: %WINDIR%\system32\config\systemprofile\AppData\Local
Group: Malware file
Last Updated: August 9, 2011
%USERPROFILE%\My Documents\Downloads\U-Ch3atsSFDFI_012912.dll
File name: U-Ch3atsSFDFI_012912.dllSize: 582.14 KB (582144 bytes)
MD5: 1d80d09144d6e714627dbdbd55b0acfd
Detection count: 2
File type: Dynamic link library
Mime Type: unknown/dll
Path: %USERPROFILE%\My Documents\Downloads
Group: Malware file
Last Updated: July 13, 2012
%AllUsersProfile%\[RANDOM CHARACTERS]
File name: %AllUsersProfile%\[RANDOM CHARACTERS]Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS]
File name: %AppData%\Local\[RANDOM CHARACTERS]Group: Malware file
%AppData%\Local\[RANDOM CHARACTERS].exe
File name: %AppData%\Local\[RANDOM CHARACTERS].exeFile type: Executable File
Mime Type: unknown/exe
Group: Malware file
%AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS]
File name: %AppData%\Roaming\Microsoft\Windows\Templates\[RANDOM CHARACTERS]Group: Malware file
%Temp%\[RANDOM CHARACTERS]
File name: %Temp%\[RANDOM CHARACTERS]Group: Malware file
Registry Modifications
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Classes\.exe "(Default)" = 'exefile'HKEY_CURRENT_USER\Software\Classes\.exe "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon "(Default)" = '%1" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile "(Default)" = 'Application'HKEY_CURRENT_USER\Software\Classes\exefile "Content Type" = 'application/x-msdownload'HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon "(Default)" = '%1'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "IsolatedCommand" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "(Default)" = '"%1" %*'HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command "IsolatedCommand" – '"%1" %*'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Mozilla Firefox\firefox.exe"'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Mozilla Firefox\firefox.exe" -safe-mode'HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%Program Files%\Internet Explorer\iexplore.exe"HKEY..\..\..\..{RegistryKeys}HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'HKEY_CLASSES_ROOT\exefile\shell\open\command "(Default)" = '"%UserProfile%\Local Settings\Application Data\[RANDOM CHARACTERS].exe" /START "%1" %*'
Additional Information
| # | Message |
|---|---|
| 1 | Privacy threat! Spyware intrusion detected. Your system is infected. System integrity is at risk. Private data can be stolen by third parties, including credit card details and passwords. Click here to perform a security repair. |
| 2 | Stealth intrusion! Infection detected in the background. Your computer is now attacked by spyware and rogue software. Eliminate the infection safely, perform a security scan and deletion now. |
| 3 | XP Security 2012 Alert Security Hole Detected! A program is trying to exploit Windows security holes! Passwords and sensitive data may be stolen. Do you want to block this attack? |
I am unable to locate the above noted files & I'm still infected by XP Security 2012
Please help
I'm having the same problem Sean. If you use the F8 function key on startup, get into safe mode, at least you can get to a few more things. I've tried the Spy Doctor and had no luck. I've been working at mine 2 or 3 days now. The files they mention can't be found with a search. I'm going to keep trying, as I can't afford to pay for anything. I'm unemployed and it barely pays my rent. Wish I could help, but I'm in the same fix.
did the scan but found nothing - not at all helpful but XP Security 2012 is there and stopping me doing anything on ie.
If you have backed up your hard drive before this got on your PC. then do as I did format drive reinstall windows then reinstall backed up drive. When I got it it would not let me use any of my programmes unless I purchased the programme
Running the SpyHunter 4 now, it has found the rogue XP security 2012, hoping it can completely remove it too when the scan has finished, this is the 3rd fake antivirus Ive had >.> all because my brother watches stupid shows on the internet with red WOT warnings 🙁 Really ruins a persons day to have these things, and Im no computer expert so Im just hoping I dont completely break my bad computer for it is the only pc I have, and will have for atleast a long time.
I've got the same problem - hoped to download something to get rid of it but can't open internet at all or add/remove progs. Already did as Jaykay said last year at PC World and not brave enough to do it again myself. Going to ask a computer boffin friend so will let you know if we solve it!
REMOVE XP SECURITY 2012 FROM MY PC NOW
I can\'t even restore the system
i tried to download all the spyware doctor and other stuff to remove xp home security but it won't let me open it. PLEASE I NEED HELP
Well,i just got this stupid Virus "XP Security 2012" and it would'nt let me open any programs or any of my browsers.I was however able to do a system restore and that seemed to work...for now.We'll see if it lasts.I really wish the government would find and execute all bad hackers,they deserve a horrible death,cheers 🙂
Okay,I just got this stupid "XP Security 2012" virus and it wouldn't let me open any of my browsers or run any programs at all,saying that they were infected with worms and such.I was however able to do a system restore and it seemed to work.....for now.We'll see if it lasts.I really wish and hope that all black hackers are publicly executed and die horrible deaths,cheers 🙂
My PC was also hijacked by XP Security 2012. However, I was able to kill the process in Task Manager long enough for me to scan my system with a malware detection program. (I use Microsoft Security Essentials).
The XP Security 2012 virus was identified as "pyj.exe" on in my Task Manager.
Mine was "myj.exe" in task manager. if u end process it gives u relief long enough to download a virus removal tool from the internet. What a pain that was.
will my AVG soft ware help me rid myself of this XP 2012 infection -- and does SpyHunter 4 work? I have not bought it yet
SpyHunter 4 worked great for me. Took a while for it to finish scanning but in the end it found more garbage on my PC than any other program. Norton FAILED to find any of that spyware junk. I hate norton and will be writing them a letter telling them they need to detect spyware and not just viruses!!!!
The furst thing it does is update the Registry to take control of the Windows shell ("explorer"), so that it can "intercept" any pgsm executed (all execution is done via the Windows shell) and prevent you from directlyu executing any pgms, getting into Control Panel, My Computer (properties), etc. There are a few ways to beat this. If you need to open a document (like a Word doc), you can r-click the doc itself and say "Open With...". Pgms seem to open up that way. I'm able to open docs, pics, MPEGs, etc. (anything that could take a file as a parameter). I know the weasels that wrote the hack are prob trolling the help sites like this to gauge how people are beating their sftware so they can close those holes in subsequnt versions (I know I would be), so hate to give up too much, but the 1st thing I did to find the pgm is open task Mgr, try to start something like a pgm or Regedt32, or do "Properties" on My Computer, and see the pgm that pops up. Then attach a debugger to it in Task Mgr (dont kill the process). I have Visual Studio on mine and I was able to stop the pgm in debug mode, get the properties on it/find the folder (because as another person said, it doesn't come up in in a normal search). It's usu in your "Local Settings\Application Data" folder. Mine was called "ccs.exe". I deleted it, but becauswe it's prob the pgm used as the interceptor in the Registry, I then started getting the "Open with" dialog on any EXE i tried to run. Work-around was to r-click on the EXE ur trying to open, and say "run as"/choose current user (clear the checkbix underneath as a precaution). Any programs that are subsequently called by the top-level EXE will get an error because u didn't get a chance to interceded to do "run as" manually, but not many EXEs call other EXEs (except install pgms ). i use ZoneAlarm - thebest by far out there. Has more security/vaulting options, isn't expensive, and has always cleaned any "fake virus scanning" product I got stuck with. Was able to do this to execute my ZoneAlarm download/install pgm, but because the pgm starts the real ZA install EXE by itself, got an error because I couldn't get in there to do a "run as". So I remembered I could use this trc=ick to just go ahead and run the ZA I already had installed, and that worked (it's not calling any other EXEs only DLLs). Scanning my PC now. Oh also, disable your internet connection while fighting this thing whenever you can, so it cant sneak any of your info out or download another helper pgm or something (in case the 1 pgm you find isn'tt the only 1 (they work together sometimes, so they can download anything you might find/delete.
The problem I am having is that after I erase the registry files, when I come back to check them minutes later the values set have regenerated. I was able to manually remove the 2011 version, but this 2012 has me beat. Is there a way for me to get the values for the registries I erase to not repopulate after so many minutes or seconds?
Apparently, this continues to be a problem. I was hit yesterday. Managed to revert to an earlier restore point before the virus hit. Had to do it in Safe Mode but in command line mode. It wouldnt work in regular Safe Mode. Running virus detection now just to make sure its all gone. Good luck!
i was on the internet yesterday night and looking at pictures i could draw for my 11th grade art class and after i closed up. on my way to bed the XP Sercurity 2012 popped up and i've been fighting in since.... i can't get onto the internet....so far i can access my control panel and computer.... help
What a pain in the #@$@# !! I was able to get rid of this by starting in diagnostic mode and disabling it in Task Manager. The file was haw.exe This at least supressed it for a while as I was able to run SpyHunter4. Once I did the first SH4 scan, I was able to restart and get to the internet and update SH4 definitions. I rescanned again and the colored risk bar went to full red (scary!) It instantly picked it up and quaranteened it. So far so good. Hope this helps.
I got rid of this through Task Manager and SpyHunter4. The file in Task Manager for me was haw.exe. Once I ended this process, it gave me time to run SpyHunter4 and suppress it for a while. I ran a normal start up and got to the internet and instantly updated SH4 definitions and rescanned. It instantly got it and quarranteed it. The colored risk bar went to full red (scary!) So far so good, hope this helps.
2012 beat Sophos. Adaware could not find it. Spybot wont run even in safe mode. Cant install or run "SuperAntiSpyware", "MalwareBytes", or AVG. The exe is labeled "XHU.EXE". I shut it down it comes back. I was successful in using CCleaner registry thing.
I'm no pro. I'm unemployed. I'm about tho be homeless here real soon and now this shit happens.
I work in the industry and have just been handed a personal laptop with this error which I\\\'ve not seen until today. Before downloading and paying for spy/maware doctor programs do the following.....
Open Task Manager (Ctrl Alt Del). Select processes tab (leave open). Click the XP Security shield in system tray and observe the file which takes CPU when \\"scanning\\". In my case it was cgx.exe. Highlight and end process.
Leave task manager open. If the XP security starts again at any point, end process in task manager.
Go to Control Panel > Click on Help and Support (on right).
Select \\"Undo changes to your computer with a system restoere\\" (on right hand side).
Select \\"restore my computer to an earlier time\\" and then a suitable date (shown in bold).
Select defaults, next etc and let the laptop/PC do the rest.
It will not lose data unless it has been applied since the last restore point you used. (In which case try to back up said data first, if possible).
In the time it has taken me to type this, the laptop I was handed is now fixed.
It popped up as sgj.exe on task manager and the icon was suspended until i opened another program...at least i\'m able to watch video and not be interuptted with pop up. still looking for cure.
Killing the process for as long as you need to select the last good recovery point worked perfectly for me. Thanks, Adam. BTW: Is this little mf really not doing anything else except annoyingly blocking things in Win?
`Hi, so my Windows Xp laptop claims there are trojans virsues infecting my system. I have googled on how to remove it and I came onto a different website on how to remove XP Home Security and I am having difficultly enlimitaing that process at the moment, but for some reason my Internet is not working and now I am stuck. So I came onto this website and it has a similar process it is telling me to do on here, but I can't find my Home Security file on my laptop nor find the HEKY thing, and my laptop is a netbook so it I will be unable to copy the Spyware software onto a CD and procede from there. Is there something else I am missing, am I supposed to go on Task Manager and go from there or delete the file and then go to task manager?
Hi, I am having some issues, firstly I can not find HEKY thingy nor Home Security file on my laptop, nothing is seeming to be working, especially my internet. I don't know what to do and I am a bit confused. I have googled and found a website to remove Home Securtiy but again I am struggling to find my Home Security file. No I have not purchased it to remove and protect my system. And again its a Windows Xp (HP Mini Netbook). Please help!? Thanks! 🙂
Thank you thank you thank you! After HOURS of trying to figure out what was happening (I do NOT work in the industry) your suggestion solved my problem in a matter of minutes.
thank you so much for your input, it gave me the idea to open task manager (after 4 hours of trying everything to remove it) i even try to download avg virus protector, and several others. all i had to do was open task manager and go to APPLICATIONS and highlight XP Security 2012 and and click END PROCESS and it worked like a charm!!! thank you soo much!!
to open task manager click and hold Ctrl - Alt - Delete, and it will open task manager
I just fixed a friends xp laptop that had this and it had a rootkit also was a job to get all cleaned up.I dont run a Windows Operating system anymore because of all this crap I run Debian Linux No viruses no spyware no trojans nothing has touched me in 3 years now of running Linux I dont need antivirus software never have to defrag it runs fast as a bullit Ill never go back to windows.
Be sure to delete the restore partition AFTER doing your system restore. When Windows takes a "snapshot" of your system you can bet the Malware WILL BE COPIED to the restore partition and IT WILL COME BACK!
Help me remove XP Security 2012! I cannot get past the first pop-up when Windows starts up. It keeps my from using Internet Explorer. Cannot download anything.
got rid of a few of these adwares and raepired the registry after .EXE programs were stopped from being run,but the programs have gone when the start button is clicked,how do you put them back? could you inbox me how if you know.