XP Home Security 2012
Posted: June 9, 2011
Threat Metric
The following fields listed on the Threat Meter containing a specific value, are explained in detail below:
Threat Level: The threat level scale goes from 1 to 10 where 10 is the highest level of severity and 1 is the lowest level of severity. Each specific level is relative to the threat's consistent assessed behaviors collected from SpyHunter's risk assessment model.
Detection Count: The collective number of confirmed and suspected cases of a particular malware threat. The detection count is calculated from infected PCs retrieved from diagnostic and scan log reports generated by SpyHunter.
Volume Count: Similar to the detection count, the Volume Count is specifically based on the number of confirmed and suspected threats infecting systems on a daily basis. High volume counts usually represent a popular threat but may or may not have infected a large number of systems. High detection count threats could lay dormant and have a low volume count. Criteria for Volume Count is relative to a daily detection count.
Trend Path: The Trend Path, utilizing an up arrow, down arrow or equal symbol, represents the level of recent movement of a particular threat. Up arrows represent an increase, down arrows represent a decline and the equal symbol represent no change to a threat's recent movement.
% Impact (Last 7 Days): This demonstrates a 7-day period change in the frequency of a malware threat infecting PCs. The percentage impact correlates directly to the current Trend Path to determine a rise or decline in the percentage.
| Threat Level: | 10/10 |
|---|---|
| Infected PCs: | 61 |
| First Seen: | June 9, 2011 |
|---|---|
| OS(es) Affected: | Windows |
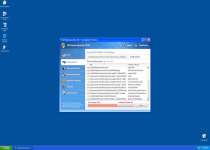
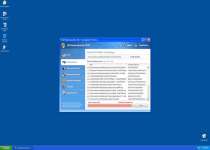
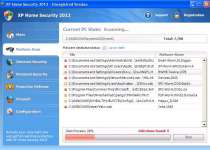 XP Home Security 2012 looks like an anti-virus and general security program, but XP Home Security 2012 actually is a threat that can only warn you about infections that don't exist. Besides creating these fake warnings, XP Home Security 2012 may also prevent you from using certain programs or take over your web browser to control which websites you can visit. XP Home Security 2012 can be removed by using real security software after you've avoided XP Home Security 2012's automatic startup routine by using Safe Mode or similar anti-malware tactics.
XP Home Security 2012 looks like an anti-virus and general security program, but XP Home Security 2012 actually is a threat that can only warn you about infections that don't exist. Besides creating these fake warnings, XP Home Security 2012 may also prevent you from using certain programs or take over your web browser to control which websites you can visit. XP Home Security 2012 can be removed by using real security software after you've avoided XP Home Security 2012's automatic startup routine by using Safe Mode or similar anti-malware tactics.
XP Home Security 2012 – Not Just a Threat to Windows XP
XP Home Security 2012 pretends to be a unique and individual anti-malware program, but XP Home Security 2012 is really a threat that's identical other rogue security programs like Antivirus 2008 Pro, Windows Antivirus 2008, Vista Antivirus 2008, Antivirus XP 2008, PC Clean Pro, Antivirus Pro 2009, AntiSpy Safeguard, ThinkPoint, Spyware Protection 2010, Internet Antivirus 2011, Palladium Pro, XP Anti-Virus 2011, CleanThis, Rogue.Vista Antivirus 2008, XP Security 2012 and AntiVirus PRO 2015.. Like most rogue security applications from the FakeRean family, XP Home Security 2012 relies on fake pop-ups and misleading system scan simulations, to make you believe that your PC is under attack by many threats.
However, threats that are detected by XP Home Security 2012 aren't real, and are generated from semi-random warning lists with examples like the following:
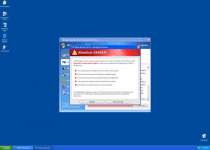
System warning!
Continue working in unprotected mode is very dangerous. Viruses can damage your confidential data and work on your computer. Click here to protect your computer.
System warning!
Security Essentials Ultimate Pack software detects programs that may compromise your privacy and harm your systems. It is highly recommended you scan your PC right now. Click here to start.
Security Alert!
Your computer is being attacked from a remote machine!
Block Internet access to your computer to prevent system infection.
Critical Warning!
Critical System Warning! Your system is probably infected with a version of Trojan-Spy.HTML.Visafraud.a. This may result in website access passwords being stolen from Internet Explorer, Mozilla Firefox, Outlook etc. Click Yes to scan and remove threats. (recommended)
If you attempt to detect these threats with other anti-malware programs, you'll notice that they will not show up. However, you may still experience malfunctions with programs that XP Home Security 2012 tells you are infected. This is purely due to XP Home Security 2012 blocking you from using the program. In many cases, renaming the program file to a generic file like 'explorer.exe' or 'iexplore.exe' will bypass XP Home Security 2012's program block list.
XP Home Security 2012's Browser-Based Warfare
In addition to blocking programs and faking anti-virus functions, XP Home Security 2012 may also engage in browser hijack attacks. These attacks can:
XP Home Security 2012 may also use other means to redirect you towards malicious websites that can steal your credit card number and other sensitive information. To prevent these attacks from happening, you can switch to Safe Mode, which will stop XP Home Security 2012's automatic startup.
Once XP Home Security 2012 isn't active, deleting XP Home Security 2012 by using suitable security programs should prove to be a simple task. Since XP Home Security 2012 is a new threat as of June 2011, it's advised that you update threat definitions for your software before launching a scan for XP Home Security 2012.
File System Modifications
- The following files were created in the system:
# File Name 1 %AllUsersProfile%\Application Data\u3f7pnvfncsjk2e86abfbj5h 2 %Documents and Settings%\[UserName]\Local Settings\Application Data\[RANDOM CHARACTERS] 3 %Documents and Settings%\[UserName]\Local Settings\Application Data\[RANDOM CHARACTERS].exe 4 %Documents and Settings%\[UserName]\Local Settings\Temp\[RANDOM CHARACTERS] 5 %Documents and Settings%\[UserName]\Templates\[RANDOM CHARACTERS] 6 %Documents and Settings%\All Users\Application Data\[RANDOM CHARACTERS] 7 %LocalAppData%\kdn.exe 8 %LocalAppData%\u3f7pnvfncsjk2e86abfbj5h 9 %Temp%\u3f7pnvfncsjk2e86abfbj5h 10 %UserProfile%\Templates\u3f7pnvfncsjk2e86abfbj5h
Registry Modifications
- The following newly produced Registry Values are:
HKEY..\..\..\..{Subkeys}HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command “(Default)” = ‘”%Documents and Settings%\[UserName]\Local Settings\Application Data\[RANDOM CHARACTERS].exe” -a “%1? %*’HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command “(Default)” = ‘”%Documents and Settings%\[UserName]\Local Settings\Application Data\[RANDOM CHARACTERS].exe” -a “%1? %*’HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command “(Default)” = ‘”%Documents and Settings%\[UserName]\Local Settings\Application Data\[random].exe” -a “%Program Files%\Mozilla Firefox\firefox.exe”‘HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command “(Default)” = ‘”%Documents and Settings%\[UserName]\Local Settings\Application Data\[random].exe” -a “%Program Files%\Mozilla Firefox\firefox.exe” -safe-mode’HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command “(Default)” = ‘”%Documents and Settings%\[UserName]\Local Settings\Application Data\[random].exee” -a “%Program Files%\Internet Explorer\iexplore.exe”‘HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center “AntiVirusOverride” = ’1?HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center “FirewallOverride” = ’1?HKEY_USERS\.DEFAULT\Software\Microsoft\Internet Explorer\BrowserEmulation “TLDUpdates” = ’1?HKEY..\..\..\..{RegistryKeys}HKEY_CLASSES_ROOT\.exe\shell\open\command “(Default)” = ‘”%Documents and Settings%\[UserName]\Local Settings\Application Data\[RANDOM CHARACTERS].exe” -a “%1? %*’
XP Home Security 2012 was a pain. Now removed and PC is faster. Thanks